Severe Flaws Disclosed in Brocade SANnav SAN Management Software
Various security vulnerabilities disclosed in Brocade SANnav storage place network (SAN) management application could be exploited to compromise vulnerable appliances. The 18 flaws impression all variations up to and like 2.3., in accordance to unbiased security…
Severe Flaws Disclosed in Brocade SANnav SAN Management SoftwareRead More

10 Critical Endpoint Security Tips You Should Know
In today’s digital earth, wherever connectivity is procedures all, endpoints provide as the gateway to a business’s electronic kingdom. And because of this, endpoints are 1 of hackers’ most loved targets. According to the IDC, 70%…
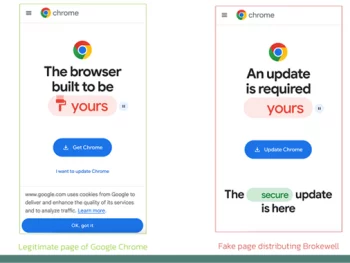
New ‘Brokewell’ Android Malware Spread Through Fake Browser Updates
Pretend browser updates are staying used to drive a previously undocumented Android malware called Brokewell. “Brokewell is a common contemporary banking malware equipped with each info-stealing and remote-command abilities designed into the malware,” Dutch security firm…
New ‘Brokewell’ Android Malware Spread Through Fake Browser UpdatesRead More

Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack
Palo Alto Networks has shared remediation advice for a just lately disclosed critical security flaw impacting PAN-OS that has arrive less than active exploitation. The vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.), could be weaponized to…
Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under AttackRead More

Hackers Exploiting WP-Automatic Plugin Bug to Create Admin Accounts on WordPress Sites
Danger actors are trying to actively exploit a critical security flaw in the WP‑Automatic plugin for WordPress that could permit web site takeovers. The shortcoming, tracked as CVE-2024-27956, carries a CVSS score of 9.9 out of…
Hackers Exploiting WP-Automatic Plugin Bug to Create Admin Accounts on WordPress SitesRead More

North Korea’s Lazarus Group Deploys New Kaolin RAT via Fake Job Lures
The North Korea-linked threat actor known as Lazarus Group used its time-examined fabricated job lures to produce a new remote entry trojan known as Kaolin RAT. The malware could, “aside from conventional RAT performance, adjust the…
North Korea’s Lazarus Group Deploys New Kaolin RAT via Fake Job LuresRead More