The North Korea-linked threat actor known as Lazarus Group used its time-examined fabricated job lures to produce a new remote entry trojan known as Kaolin RAT.
The malware could, “aside from conventional RAT performance, adjust the previous write timestamp of a selected file and load any gained DLL binary from [command-and-control] server,” Avast security researcher Luigino Camastra said in a report released past week.
The RAT functions as a pathway to deliver the FudModule rootkit, which has been not too long ago observed leveraging a now-patched admin-to-kernel exploit in the appid.sys driver (CVE-2024-21338, CVSS score: 7.8) to receive a kernel go through/create primitive and eventually disable security mechanisms.
The Lazarus Group’s use of position offer you lures to infiltrate targets is not new. Dubbed Operation Desire Job, the prolonged-jogging campaign has a observe document of working with various social media and immediate messaging platforms to produce malware.

These original entry vectors trick targets into launching a destructive optical disc image (ISO) file bearing 3 data files, 1 of which masquerades as an Amazon VNC customer (“AmazonVNC.exe”) that, in fact, is a renamed model of a authentic Windows application termed “decision.exe.”
The two other data files are named “version.dll” and “aws.cfg.” The executable “AmazonVNC.exe” is made use of to side-load “edition.dll,” which, in transform, spawns an IExpress.exe system and injects into it a payload residing within “aws.cfg.”
The payload is designed to obtain shellcode from a command-and-handle (C2) domain (“henraux[.]com”), which is suspected to be an precise-but-hacked site belonging to an Italian organization that specializes in excavating and processing marble and granite.
When the exact character of the shellcode is unclear, it’s stated to be employed to start RollFling, a DLL-based mostly loader that serves to retrieve and start the future-stage malware named RollSling, which was disclosed by Microsoft previous yr in relationship with a Lazarus Team campaign exploiting a critical JetBrains TeamCity flaw (CVE-2023-42793, CVSS score: 9.8).
RollSling, executed directly in memory in a very likely endeavor to evade detection by the security program, signifies the following phase of the infection procedure. Its major perform is to cause the execution of a 3rd loader dubbed RollMid that is also run in the system’s memory.
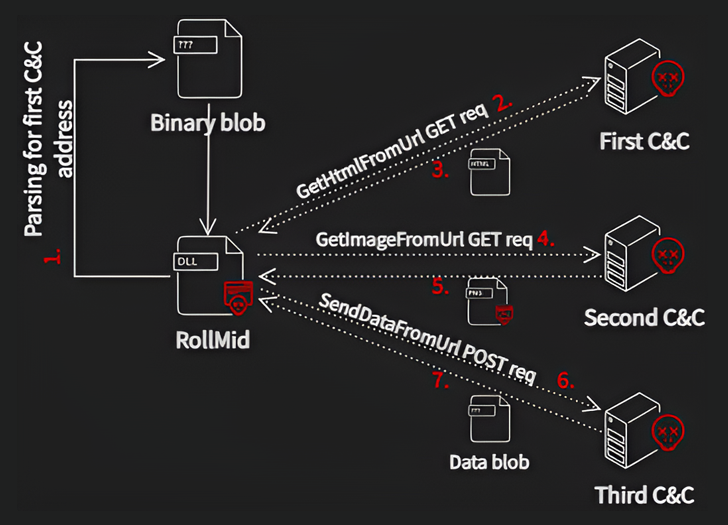
RollMid will come fitted with capabilities to set the stage for the attack and create get in touch with with a C2 server, which includes a three-stage procedure of its possess as follows –
- Connect with the 1st C2 server to fetch a HTML that contains the deal with of the second C2 server
- Talk with the 2nd C2 server to fetch a PNG image that embeds a malicious ingredient employing a procedure called steganography
- Transmit knowledge to the 3rd C2 server making use of the tackle specified in the hid info inside of the graphic
- Retrieve an additional Foundation64-encoded information blob from the third C2 server, which is the Kaolin RAT
The specialized sophistication behind the multi-phase sequence, even though no question elaborate and intricate, borders on overkill, Avast opined, with the Kaolin RAT paving the way for the deployment of the FudModule rootkit just after setting up communications with the RAT’s C2 server.

On leading of that, the malware is equipped to enumerate information have out file functions add information to the C2 server alter a file’s past modified timestamp enumerate, develop, and terminate procedures execute commands making use of cmd.exe download DLL files from the C2 server and connect to an arbitrary host.
“The Lazarus team qualified persons by way of fabricated job features and employed a innovative toolset to reach much better persistence while bypassing security goods,” Camastra said.
“It is apparent that they invested important means in producing such a complicated attack chain. What is sure is that Lazarus had to innovate repeatedly and allocate massive sources to investigate many factors of Windows mitigations and security products. Their potential to adapt and evolve poses a major problem to cybersecurity initiatives.”
Uncovered this report intriguing? Adhere to us on Twitter and LinkedIn to read additional special information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Network Threats: A Step-by-Step Attack Demonstration
Network Threats: A Step-by-Step Attack Demonstration