A new ongoing malware marketing campaign has been noticed distributing three different stealers, these as CryptBot, LummaC2, and Rhadamanthys hosted on Content Shipping Network (CDN) cache domains considering the fact that at least February 2024.
Cisco Talos has attributed the activity with average self-confidence to a danger actor tracked as CoralRaider, a suspected Vietnamese-origin team that came to light before this thirty day period.
This assessment is primarily based on “several overlaps in methods, techniques, and procedures (TTPs) of CoralRaider’s Rotbot campaign, like the first attack vector of the Windows Shortcut file, intermediate PowerShell decryptor and payload down load scripts, the FoDHelper strategy used to bypass User Obtain Controls (UAC) of the sufferer device,” the firm claimed.

Targets of the marketing campaign span different company verticals across geographies, including the U.S., Nigeria, Pakistan, Ecuador, Germany, Egypt, the U.K., Poland, the Philippines, Norway, Japan, Syria, and Turkey.
Attack chains entail end users downloading files masquerading as film information by means of a web browser, increasing the possibility of a large-scale attack.
“This risk actor is employing a Information Shipping and delivery Network (CDN) cache to retail outlet the destructive information on their network edge host in this marketing campaign, steering clear of request hold off,” Talos researchers Joey Chen, Chetan Raghuprasad, and Alex Karkins reported. “The actor is utilizing the CDN cache as a obtain server to deceive network defenders.”
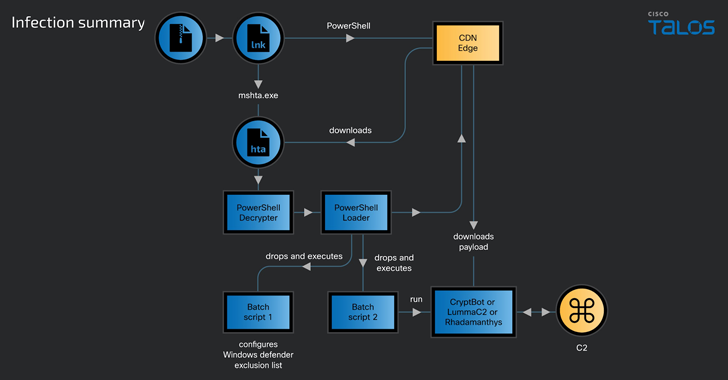
The first obtain vector for the push-by downloads is suspected to be phishing email messages, employing them as a conduit to propagate booby-trapped one-way links pointing to ZIP archives that contains a Windows shortcut (LNK) file.
The shortcut file, in flip, runs a PowerShell script to fetch a upcoming-phase HTML application (HTA) payload hosted on the CDN cache, which subsequently runs Javascript code to launch an embedded PowerShell loader that will take steps to fly below the radar and eventually downloads and runs 1 of the a few stealer malware.

The modular PowerShell loader script is intended to bypass the Consumer Entry Controls (UAC) in the victim’s device working with a known approach referred to as FodHelper, which has also been set to use by Vietnamese danger actors connected to an additional stealer recognised as NodeStealer that is capable of thieving Facebook account information.
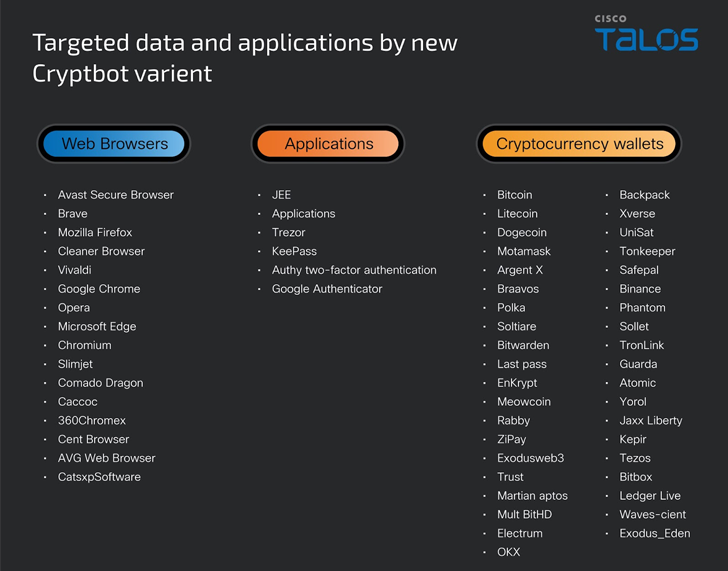
The stealer malware, irrespective of what’s deployed, grabs victims’ info, such as program and browser knowledge, credentials, cryptocurrency wallets, and economic details.
What is actually noteworthy about the marketing campaign is that it makes use of an up-to-date edition of CryptBot that packs in new anti-assessment tactics and also captures password supervisor software databases and authenticator application data.
Identified this post interesting? Follow us on Twitter and LinkedIn to go through far more exceptional content we post.
Some parts of this article are sourced from:
thehackernews.com

 Apache Cordova App Harness Targeted in Dependency Confusion Attack
Apache Cordova App Harness Targeted in Dependency Confusion Attack