A new malware campaign has been exploiting the updating mechanism of the eScan antivirus computer software to distribute backdoors and cryptocurrency miners like XMRig through a long-standing menace codenamed GuptiMiner concentrating on substantial company networks.
Cybersecurity firm Avast mentioned the action is the work of a danger actor with probable connections to a North Korean hacking group dubbed Kimsuky, which is also acknowledged as Black Banshee, Emerald Sleet, and TA427.
“GuptiMiner is a remarkably complex risk that utilizes an intriguing infection chain together with a couple of methods that contain performing DNS requests to the attacker’s DNS servers, undertaking sideloading, extracting payloads from harmless-looking pictures, signing its payloads with a tailor made trustworthy root anchor certification authority, between other individuals,” Avast stated.
The intricate and elaborate infection chain, at its core, leverages a security shortcoming in the update system of Indian antivirus seller eScan to propagate the malware by signifies of an adversary-in-the-middle (AitM) attack.

Exclusively, it involves hijacking the updates by substituting the package deal file with a malicious variation by having benefit of the reality that the downloads were being not signed and secured working with HTTPS. The issue, which went unnoticed for at minimum 5 decades, has been rectified as of July 31, 2023.
The rogue DLL (“updll62.dlz”) executed by the eScan computer software aspect-hundreds a DLL (“model.dll”) to activate a multi-stage sequence beginning with a PNG file loader that, in flip, employs malicious DNS servers to make contact with a command-and-management (C2) server and fetch a PNG file with appended shellcode.
“GuptiMiner hosts their possess DNS servers for serving true place area addresses of C&C servers by means of DNS TXT responses,” researchers Jan Rubín and Milánek reported.
“As the malware connects to the destructive DNS servers instantly, the DNS protocol is wholly separated from the DNS network. Hence, no reputable DNS server will ever see the targeted traffic from this malware.”
The PNG file is then parsed to extract the shellcode, which is then liable for executing a Gzip loader that’s designed to decompress a different shellcode making use of Gzip and execute it in a separate thread.
The 3rd-phase malware, dubbed Puppeteer, pulls all the strings, ultimately deploying the XMRig cryptocurrency miner and backdoors on the contaminated units.
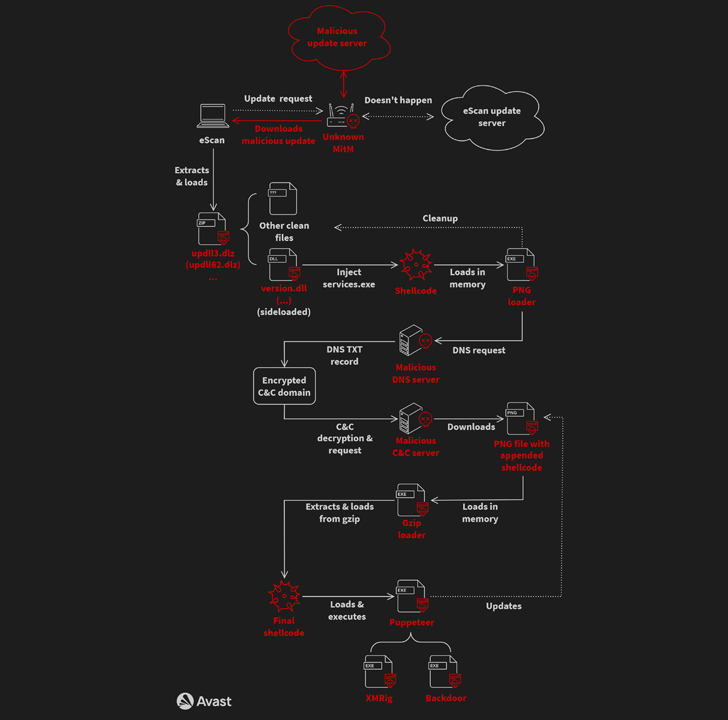
Avast claimed it encountered two various types of backdoors that appear equipped with characteristics to empower lateral movement, accept instructions from the danger actor, and produce further parts as needed.
“The 1st is an increased build of PuTTY Url, offering SMB scanning of the neighborhood network and enabling lateral motion over the network to possibly vulnerable Windows 7 and Windows Server 2008 devices on the network,” the researchers stated.
“The next backdoor is multi-modular, accepting commands from the attacker to install a lot more modules as well as concentrating on scanning for stored non-public keys and crypto wallets on the local program.”
The deployment of XMRig has been explained as “unexpected” for what’s or else a sophisticated and meticulously executed operation, increasing the probability that the miner acts as a distraction to stop victims from getting the correct extent of the compromise.
GuptiMiner, recognised to be active considering that at least 2018, also makes use of a variety of approaches like anti-VM and anti-debug methods, code virtualization, dropping the PNG loader for the duration of process shutdown events, storing payloads in Windows Registry, and incorporating a root certification to Windows’ certification keep to make the PNG loader DLLs surface dependable.

The one-way links to Kimusky occur from an facts stealer that, while not dispersed by GuptiMiner or through the an infection movement, has been used “across the whole GuptiMiner marketing campaign” and shares overlaps with a keylogger beforehand determined as utilized by the group.
It truly is at present not obvious who the targets of the marketing campaign are, but GuptiMiner artifacts have been uploaded to VirusTotal from India and Germany as early as April 2018, with Avast telemetry knowledge highlighting new bacterial infections likely originating from out-of-day eScan clientele.
The findings appear as the Korean Countrywide Police Agency (KNPA) referred to as out North Korean hacking crews this sort of as Lazarus, Andariel, and Kimsuky for targeting the protection sector in the region and exfiltrating beneficial data from some of them.
A report from the Korea Financial Every day reported the risk actors penetrated the networks of 83 South Korean defense contractors and stole private data from about 10 of them from October 2022 to July 2023.
Uncovered this article appealing? Follow us on Twitter and LinkedIn to examine additional unique content we put up.
Some parts of this article are sourced from:
thehackernews.com


 CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers
CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers