A new malware marketing campaign leveraged two zero-working day flaws in Cisco networking equipment to produce custom malware and facilitate covert knowledge collection on focus on environments.
Cisco Talos, which dubbed the action ArcaneDoor, attributing it as the handiwork of a beforehand undocumented subtle condition-sponsored actor it tracks beneath the title UAT4356 (aka Storm-1849 by Microsoft).
“UAT4356 deployed two backdoors as factors of this campaign, ‘Line Runner’ and ‘Line Dancer,’ which were being utilised collectively to carry out malicious actions on-concentrate on, which included configuration modification, reconnaissance, network visitors capture/exfiltration and possibly lateral motion,” Talos reported.

The intrusions, which were being initially detected and verified in early January 2024, entail the exploitation of two vulnerabilities –
- CVE-2024-20353 (CVSS score: 8.6) – Cisco Adaptive Security Appliance and Firepower Danger Protection Software Web Services Denial-of-Services Vulnerability
- CVE-2024-20359 (CVSS rating: 6.) – Cisco Adaptive Security Equipment and Firepower Threat Defense Software program Persistent Regional Code Execution Vulnerability
It really is well worth noting that a zero-day exploit is the procedure or attack a malicious actor deploys to leverage an mysterious security vulnerability to acquire access into a procedure.
While the next flaw enables a local attacker to execute arbitrary code with root-stage privileges, administrator-amount privileges are required to exploit it. Addressed together with CVE-2024-20353 and CVE-2024-20359 is a command injection flaw in the very same equipment (CVE-2024-20358, CVSS score: 6.) that was uncovered throughout inside security tests.
The U.S. Cybersecurity and Infrastructure Security Company (CISA) has additional the shortcomings to its Known Exploited Vulnerabilities (KEV) catalog, requiring federal agencies to implement the vendor-supplied fixes by May 1, 2024.
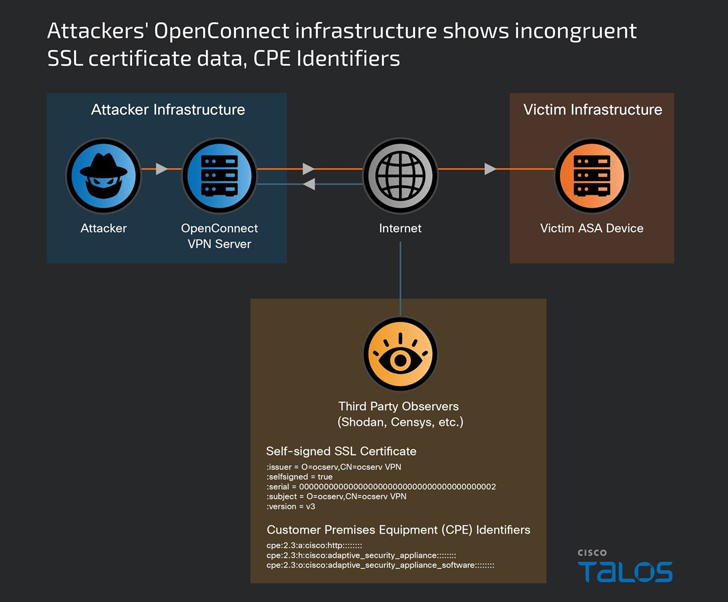
The precise original accessibility pathway utilised to breach the devices is presently mysterious, even though UAT4356 is stated to have commenced preparations for it as early as July 2023.
A productive foothold is followed by the deployment of two implants named Line Dancer and Line Runner, the previous of which is an in-memory backdoor that allows attackers to upload and execute arbitrary shellcode payloads, together with disabling procedure logs and exfiltrating packet captures.
Line Runner, on the other hand, is a persistent HTTP-dependent Lua implant put in on the Cisco Adaptive Security Appliance (ASA) by leveraging the aforementioned zero-times such that it can survive throughout reboots and upgrades. It has been observed being made use of to fetch details staged by Line Dancer.
“It is suspected that Line Runner may well be existing on a compromised device even if Line Dancer is not (e.g., as a persistent backdoor, or exactly where an impacted ASA has not still been given complete operational notice from the malicious actors),” according to a joint advisory posted by cybersecurity agencies from Australia, Canada, and the U.K.
At each individual period of the attack, UAT4356 is mentioned to have demonstrated meticulous awareness to hiding electronic footprints and the potential to make use of intricate procedures to evade memory forensics and decrease the likelihood of detection, contributing to its sophistication and elusive nature.
This also indicates that the danger actors have a finish knowledge of the interior workings of the ASA alone and of the “forensic actions frequently done by Cisco for network machine integrity validation.”

Particularly which state is behind ArcaneDoor is unclear, however equally Chinese and Russian condition-backed hackers have specific Cisco routers for cyber espionage uses in the previous. Cisco Talos also did not specify how several consumers were being compromised in these assaults.
The development at the time all over again highlights the greater targeting of edge units and platforms these types of as email servers, firewalls, and VPNs that traditionally lack endpoint detection and response (EDR) options, as evidenced by the the latest string of attacks focusing on Barracuda Networks, Fortinet, Ivanti, Palo Alto Networks, and VMware.
“Perimeter network devices are the perfect intrusion stage for espionage-concentrated campaigns,” Talos said.
“As a critical path for facts into and out of the network, these units require to be routinely and immediately patched using up-to-day hardware and software program variations and configurations and be closely monitored from a security point of view. Attaining a foothold on these devices lets an actor to instantly pivot into an firm, reroute or modify visitors and watch network communications.”
Identified this report interesting? Follow us on Twitter and LinkedIn to read much more exclusive written content we article.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks
U.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks