Cybersecurity scientists have identified an ongoing attack campaign which is leveraging phishing e-mail to provide malware named SSLoad.
The campaign, codenamed FROZEN#SHADOW by Securonix, also requires the deployment of Cobalt Strike and the ConnectWise ScreenConnect distant desktop software package.
“SSLoad is intended to stealthily infiltrate programs, assemble delicate details and transmit its conclusions again to its operators,” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker Information.
“At the time within the system, SSLoad deploys many backdoors and payloads to keep persistence and avoid detection.”
Attack chains require the use of phishing messages to randomly focus on organizations in Asia, Europe, and the Americas, with emails containing one-way links that guide to the retrieval of a JavaScript file that kicks off the an infection circulation.

Before this thirty day period, Palo Alto Networks uncovered at minimum two unique solutions by which SSLoad is dispersed, just one which involves the use of web-site call varieties to embed booby-trapped URLs and another involving macro-enabled Microsoft Word paperwork.
The latter is also noteworthy for the simple fact that malware acts as a conduit for providing Cobalt Strike, although the previous has been utilised to deliver a different malware termed Latrodectus, a most likely successor to IcedID.
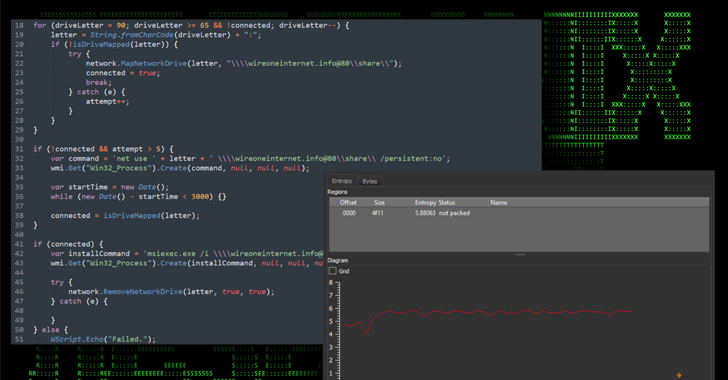
The obfuscated JavaScript file (“out_czlrh.js”), when released and operate utilizing wscript.exe, retrieves an MSI installer file (“slack.msi”) by connecting to a network share positioned at “\wireoneinternet[.]info@80share” and runs it working with msiexec.exe.
The MSI installer, for its component, contacts an attacker-managed area to fetch and execute the SSLoad malware payload working with rundll32.exe, pursuing which it beacons to a command-and-control (C2) server along with details about the compromised procedure.
The original reconnaissance section paves the way for Cobalt Strike, a genuine adversary simulation computer software, which is then employed to down load and install ScreenConnect, thereby allowing for the danger actors to remotely commandeer the host.

“With comprehensive access to the process the risk actors started making an attempt to receive qualifications and acquire other critical system details,” the researchers claimed. “At this stage they began scanning the victim host for credentials stored in documents as effectively as other potentially delicate documents.”
The attackers have also been noticed pivoting to other devices in the network, including the domain controller, eventually infiltrating the victim’s Windows area by building their have domain administrator account.
“With this level of obtain, they could get into any linked equipment in the domain,” the scientists reported. “In the conclusion, this is the worst scenario scenario for any organization as this level of persistence obtained by the attackers would be exceptionally time consuming and high-priced to remediate.”
The disclosure comes as the AhnLab Security Intelligence Heart (ASEC) revealed that Linux techniques are remaining infected with an open up-supply remote accessibility trojan named Pupy RAT.
Identified this article appealing? Follow us on Twitter and LinkedIn to study more unique articles we article.
Some parts of this article are sourced from:
thehackernews.com

 Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App Users
Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App Users