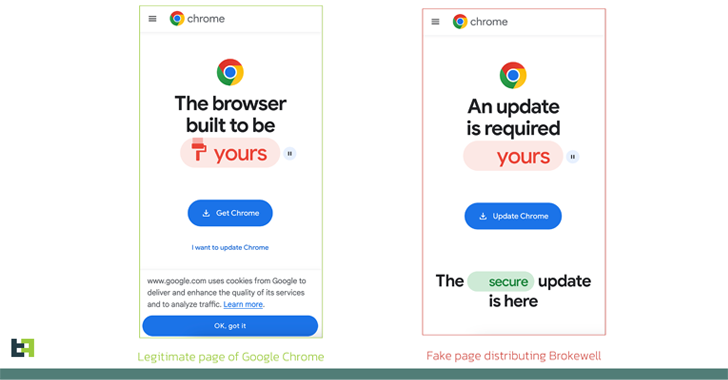
Pretend browser updates are staying used to drive a previously undocumented Android malware called Brokewell.
“Brokewell is a common contemporary banking malware equipped with each info-stealing and remote-command abilities designed into the malware,” Dutch security firm ThreatFabric mentioned in an examination published Thursday.
The malware is mentioned to be in lively growth, including new instructions to seize touch activities, textual info shown on screen, and the purposes a target launches.
The record of Brokewell apps that masquerade as Google Chrome, ID Austria, and Klarna is as follows –
- jcwAz.EpLIq.vcAZiUGZpK (Google Chrome)
- zRFxj.ieubP.lWZzwlluca (ID Austria)
- com.brkwl.upstracking (Klarna)
Like other the latest Android malware households of its form, Brokewell is capable of having all-around constraints imposed by Google that avoid sideloaded applications from requesting accessibility company permissions.

The banking trojan, after mounted and launched for the initial time, prompts the target to grant permissions to the accessibility support, which it subsequently takes advantage of to automatically grant other permissions and have out different malicious actions.
This includes displaying overlay screens on prime of focused applications to pilfer user credentials. It can also steal cookies by launching a WebView and loading the reputable web page, after which the session cookies are intercepted and transmitted to an actor-managed server.
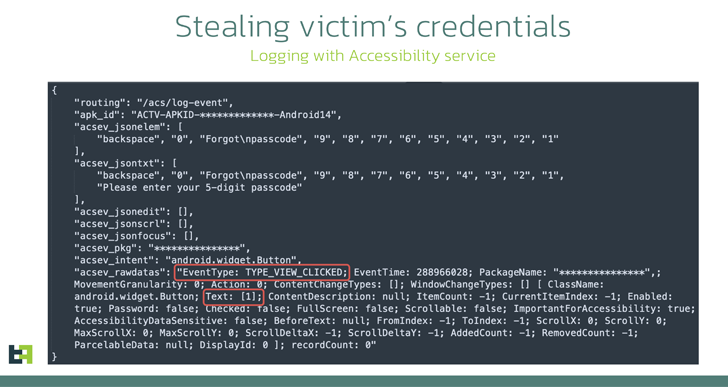
Some of the other characteristics of Brokewell include things like the capability to document audio, just take screenshots, retrieve phone logs, access device area, checklist mounted apps, file each and every each individual celebration taking place on the unit, deliver SMS messages, do phone phone calls, set up and uninstall applications, and even disable the accessibility service.
The menace actors can also leverage the malware’s remote control operation to see what is actually exhibited on screen in real-time, as perfectly as interact with the gadget by clicks, swipes, and touches.
Brokewell is explained to be the do the job of a developer who goes by the name “Baron Samedit Marais” and manages the “Brokewell Cyber Labs” venture, which also involves an Android Loader publicly hosted on Gitea.

The loader is designed to act as a dropper that bypasses accessibility permissions limits in Android variations 13, 14, and 15 utilizing a approach previously adopted by dropper-as-a-assistance (DaaS) offerings like SecuriDropper and deploy the trojan implant.
By default, the loader apps generated by this course of action have the package deal identify “com.brkwl.apkstore,” though this can configured by the user by both providing a distinct name or enabling the random offer name generator.
The no cost availability of the loader usually means it could be embraced by other menace actors on the lookout to sidestep Android’s security protections.
“Next, current ‘Dropper-as-a-Service’ choices that at the moment deliver this functionality as a distinct characteristic will very likely both close their providers or try to reorganize,” ThreatFabric said.
“This even more lowers the entry barrier for cybercriminals on the lookout to distribute cellular malware on modern-day products, making it easier for far more actors to enter the area.”
Uncovered this report exciting? Stick to us on Twitter and LinkedIn to examine more unique content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack
Palo Alto Networks Outlines Remediation for Critical PAN-OS Flaw Under Attack