Various threat actors, together with cyber espionage teams, are utilizing an open-resource Android remote administration instrument identified as Rafel RAT to fulfill their operational aims by masquerading it as Instagram, WhatsApp, and many e-commerce and antivirus applications.
“It offers destructive actors with a potent toolkit for distant administration and command, enabling a assortment of malicious actions from data theft to product manipulation,” Check out Place stated in an assessment printed very last week.
It boasts a broad vary of characteristics, these kinds of as the capability to wipe SD cards, delete connect with logs, siphon notifications, and even act as ransomware.

The use of Rafel RAT by DoNot Group (aka APT-C-35, Brainworm, and Origami Elephant) was beforehand highlighted by the Israeli cybersecurity business in cyber attacks that leveraged a structure flaw in Foxit PDF Reader to trick end users into downloading destructive payloads.
The campaign, which took put in April 2024, is said to have utilized armed forces-themed PDF lures to deliver the malware.
Test Stage reported it recognized around 120 distinct malicious campaigns, some targeting significant-profile entities, that span many countries like Australia, China, Czechia, France, Germany, India, Indonesia, Italy, New Zealand, Pakistan, Romania, Russia, and the U.S.
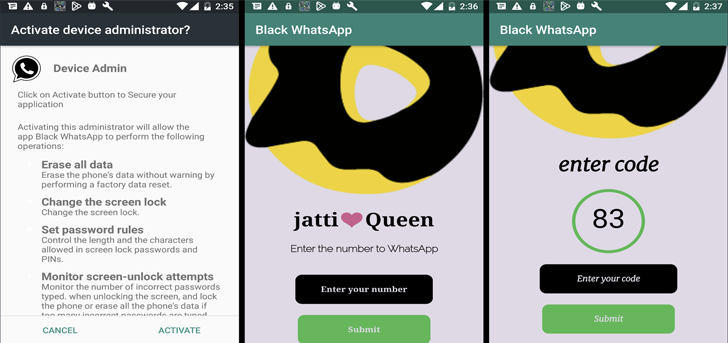
“The bulk of victims had Samsung phones, with Xiaomi, Vivo, and Huawei customers comprising the second-major team amongst the qualified victims,” it pointed out, incorporating no fewer than 87.5% of the infected products are running out-of-date Android variations that no more time receive security fixes.
Regular attack chains involve the use of social engineering to manipulate victims into granting the malware-laced applications intrusive permissions in purchase to hoover delicate facts like speak to data, SMS messages (e.g., 2FA codes), place, call logs, and the list of installed programs, among the other individuals.
Rafel RAT generally makes use of HTTP(S) for command-and-handle (C2) communications, but it can also employ Discord APIs to make contact with the menace actors. It also comes with an accompanying PHP-based C2 panel that registered buyers can leverage to issue commands to compromised equipment.

The tool’s performance throughout several threat actors is corroborated by its deployment in a ransomware operation carried out by an attacker probable originating from Iran, who despatched a ransom note composed in Arabic by means of an SMS that urged a victim in Pakistan to call them on Telegram.
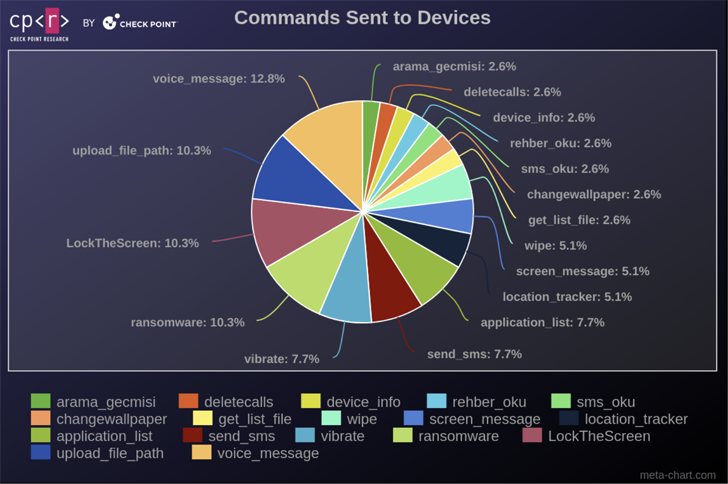
“Rafel RAT is a powerful illustration of the evolving landscape of Android malware, characterised by its open-resource nature, substantial element set, and widespread utilization across numerous illicit things to do,” Examine Point said.
“The prevalence of Rafel RAT highlights the want for continual vigilance and proactive security measures to safeguard Android gadgets in opposition to destructive exploitation.”
Observed this short article exciting? Comply with us on Twitter and LinkedIn to study extra special articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 ExCobalt Cyber Gang Targets Russian Sectors with New GoRed Backdoor
ExCobalt Cyber Gang Targets Russian Sectors with New GoRed Backdoor