The modern day destroy chain is eluding enterprises simply because they aren’t shielding the infrastructure of modern-day company: SaaS.
SaaS carries on to dominate software program adoption, and it accounts for the biggest share of general public cloud paying out. But enterprises and SMBs alike have not revised their security programs or adopted security tooling constructed for SaaS.
Security teams preserve jamming on-prem pegs into SaaS security holes
The mature security controls CISOs and their groups depended on in the age of on-prem dominance have vanished. Firewalls now shield a compact perimeter, visibility is limited, and even if SaaS distributors offer you logs, security groups will need homegrown middleware to digest them and thrust into their SIEM.
SaaS sellers do have perfectly-outlined security scopes for their solutions, but their prospects must deal with SaaS compliance and info governance, identity and entry administration (IAM), and application controls — the places exactly where most incidents occur. Even though this SaaS shared obligation design is common amid SaaS apps, no two SaaS programs have identical security options.
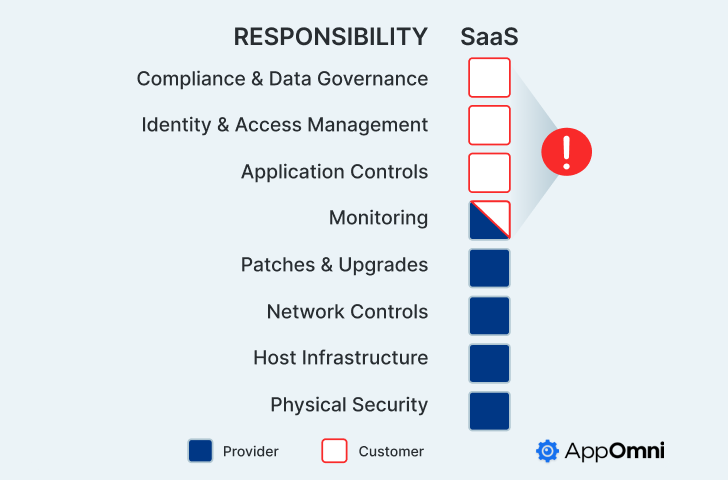 Determine 1. In the context of SaaS security worries, the application company is liable for all physical infrastructure, as well as the network, OS, and software. The shopper is accountable for knowledge security and identity management. The SaaS shared responsibility product demands SaaS buyers to think ownership of parts that danger actors attack most typically. Illustration courtesy of AppOmni.
Determine 1. In the context of SaaS security worries, the application company is liable for all physical infrastructure, as well as the network, OS, and software. The shopper is accountable for knowledge security and identity management. The SaaS shared responsibility product demands SaaS buyers to think ownership of parts that danger actors attack most typically. Illustration courtesy of AppOmni.
AppOmni research experiences that on normal, a one occasion of SaaS has 256 SaaS-to-SaaS connections, several of which are no more time in use, but even now have extreme permissions into main business enterprise applications these as Salesforce, Okta, and GitHub, amongst other individuals.
Concerning the multitude of distinctive SaaS security settings and continual updates that alter them, security groups are unable to correctly keep track of these connections. The amount of entry points multiplies exponentially when employees permit SaaS-to-SaaS (also called “third get together” or “equipment”) connections. Equipment identities can use API keys, techniques, classes, electronic certificates, cloud obtain keys, and other qualifications to permit devices to talk with a single another.
As the attack surface area migrated outdoors the network perimeter, so did the destroy chain — the way in which danger actors orchestrate the many phases of their attacks.
The modern-day SaaS eliminate chain commonly involves:
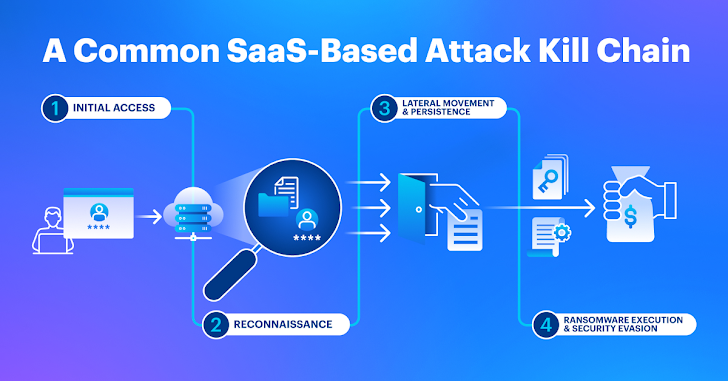 Figure 2. Productive SaaS eliminate chains normally include 4 overarching ways: original entry, reconnaissance, lateral motion and persistence, and ransomware execution and security evasion. Illustration courtesy of AppOmni.
Figure 2. Productive SaaS eliminate chains normally include 4 overarching ways: original entry, reconnaissance, lateral motion and persistence, and ransomware execution and security evasion. Illustration courtesy of AppOmni.
Breaking down a real-globe SaaS destroy chain: Scattered Spider/Starfraud
SaaS security chief AppOmni’s newest risk intelligence briefing webinar delineated the destroy chain of the Scattered Spider/Starfraud threat actor groups’ (affiliates of ALPHV) productive attack on an undisclosed focus on in September 2023:
- A consumer opened a phishing email that contained backlinks to a spoofed IdP login web site, and they unknowingly logged into the fake IdP web site.
- The risk actor teams immediately known as that user and convinced them, by social engineering, to offer their time-based, one particular-time password (TOTP) token.
- Soon after obtaining the user’s login credentials and TOTP token, the risk actors tricked the MFA protocol into contemplating they’re the legitimate consumer.
- Though in reconnaissance mode, the danger actors had obtain to a privileged escalation, enabling them to get hold of credentials into Amazon S3, then Azure Ad, and lastly Citrix VDI (virtual desktop infrastructure).
- The threat actors then deployed their individual malicious server in the IaaS ecosystem, in which they executed a privileged Azure Advert escalation attack.
- The attackers encrypted all the details within their access and delivered a ransom be aware.
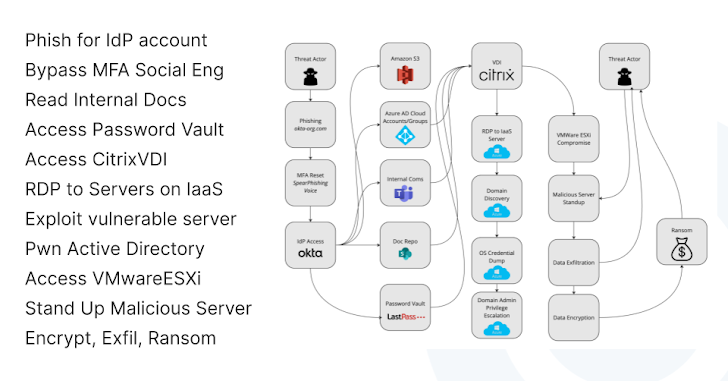 Determine 3. The destroy chain made use of by the Scattered Spider/Starfraud risk actor teams. Illustration courtesy of AppOmni.
Determine 3. The destroy chain made use of by the Scattered Spider/Starfraud risk actor teams. Illustration courtesy of AppOmni.
Scattered Spider/Starfraud probably achieved this sequence of situations around various times. When SaaS serves as the entry issue, a major attack can include the company network and infrastructure. This SaaS/on-prem connectivity is widespread in today’s company attack surfaces.
SaaS attack exercise from acknowledged and unfamiliar menace actors is growing
Most SaaS breaches are not dominating headlines, but the repercussions are significant. IBM studies that knowledge breaches in 2023 averaged $4.45 million for each instance, symbolizing a 15% maximize in excess of 3 yrs.
Risk actors are constantly relying on the similar TTPs and playbook of the Scattered Spider/Starfraud destroy chain to gain unauthorized accessibility and scan SaaS tenants, including Salesforce and M365 where configuration issues could be manipulated to present access afterwards.
Other attackers achieve original entry with session hijacking and difficult vacation. The moment they have transferred the hijacked session to a diverse host, their lateral movement often includes communications platforms such as SharePoint, JIRA, DocuSign, and Slack, as properly as document repositories like Confluence. If they can entry GitHub or other supply code repositories, risk actors will pull down that source code and analyze it for vulnerabilities in a target application. They are going to endeavor to exploit these vulnerabilities to exfiltrate the focus on app’s data.
The AppOmni risk intelligence briefing also reviews that details exfiltration by means of authorization sharing continues to be a major SaaS security problem. This occurs, for example, in Google Workspace when the unauthorized person improvements directories to a quite open degree of permissions. The attacker may perhaps share them with a different exterior entity by means of email forwarding, or shifting conditional rules so attackers are integrated as BCC recipients in a distribution record.
How do you defend your SaaS environments?
1. Concentrate on SaaS devices cleanliness
Set up a SaaS ingestion and critique procedure to determine what SaaS you may allow in your firm. This procedure really should have to have answers to security issues these types of as:
- Does all SaaS require to be SOC 2 Form 2 qualified?
- What is the optimum security configuration for every single tenant?
- How will your enterprise stay away from configuration drift?
- How will you decide if computerized SaaS updates will have to have modifying security manage settings?
Make certain you can detect Shadow IT SaaS (or unsanctioned SaaS apps) and have a reaction plan so alerts aren’t created in vain.
If you are not monitoring your SaaS tenants and ingesting all of the logs from them in some unified approach, you’ll in no way be in a position to detect suspicious behaviors and acquire alerts primarily based on them.
2. Inventory and continually monitor machine accounts/identities
Risk actors focus on equipment identities for their privileged obtain and lax authentication expectations, frequently hardly ever requiring MFA.
In 2023, threat actors efficiently focused and breached major CI/CD instruments Travis CI, CircleCI, and Heroku, thieving OAuth tokens for all of these providers’ prospects. The blast radius expands substantially in these circumstances.
With the typical business that contains 256 equipment identities, cleanliness is normally lacking. Many of them are made use of the moment or two times and then stay stagnant for yrs.
Stock all of your device identities and triage these critical challenges. At the time you have mitigated these, create policies that prescribe:
- What sort of accounts will be granted machine identities, and the demands these sellers have to meet up with to be granted accessibility.
- The time frame for how prolonged their entry/tokens are energetic prior to they will be revoked, refreshed, or regranted.
- How you’ll observe these accounts for their usage and make sure they are nonetheless wanted if they encounter durations of dormancy.
3. Create out a correct Zero Rely on architecture in your SaaS estate
Zero Have faith in architecture builds on the theory of the very least privilege (PLP) with a “under no circumstances have faith in, usually verify” tactic. Whilst Zero Rely on has been proven in standard networks, it truly is rarely realized in SaaS environments.
Zero Trust Network Access (ZTNA)’s network-centric technique can’t detect misconfigurations, machine integrations, or undesirable user obtain entitlements in and to SaaS platforms, which can have 1000’s or even tens of millions of exterior users accessing data.
Zero Believe in Posture Management (ZTPM), an rising SaaS security resource, extends Zero Have faith in to your SaaS estate. It bridges the SaaS security hole that SASE produces by:
- Preventing unauthorized ZTNA bypass
- Permitting for wonderful-tuned obtain decisions
- Enforcing your security guidelines with continuous opinions loops
- Extending Zero Rely on to machine integrations and cloud connections
With SSPM, ZTPM, and a SaaS security method in spot, your workforce will attain the visibility and intelligence it demands to identify intruders in the lower-risk levels of your kill chain — and end them just before a breach gets devastating.
Found this report appealing? This short article is a contributed piece from a person of our valued partners. Adhere to us on Twitter and LinkedIn to go through more exclusive material we article.
Some parts of this article are sourced from:
thehackernews.com


 New SnailLoad Attack Exploits Network Latency to Spy on Users’ Web Activities
New SnailLoad Attack Exploits Network Latency to Spy on Users’ Web Activities