The North Korea-joined danger actor recognised as Kimsuky has been connected to the use of a new destructive Google Chrome extension that is intended to steal sensitive facts as part of an ongoing intelligence assortment energy.
Zscaler ThreatLabz, which noticed the exercise in early March 2024, has codenamed the extension TRANSLATEXT, highlighting its means to assemble email addresses, usernames, passwords, cookies, and browser screenshots.
The specific marketing campaign is stated to have been directed from South Korean academia, precisely all those targeted on North Korean political affairs.
Kimsuky is a notorious hacking crew from North Korea that is identified to be active considering that at the very least 2012, orchestrating cyber espionage and monetarily determined assaults focusing on South Korean entities.

A sister team of the Lazarus cluster and portion of the Reconnaissance Common Bureau (RGB), it is also tracked under the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet, Springtail, and Velvet Chollima.
In latest weeks, the group has weaponized a regarded security flaw in Microsoft Business office (CVE-2017-11882) to distribute a keylogger and has employed occupation-themed lures in attacks aimed at aerospace and defense sectors with an purpose to fall an espionage tool with data collecting and secondary payload execution functionalities.
“The backdoor, which does not appear to have been publicly documented just before, allows the attacker to perform essential reconnaissance and drop supplemental payloads to acquire in excess of or remotely manage the equipment,” cybersecurity enterprise CyberArmor said. It has supplied the campaign the identify Niki.
The specific mode of initial access connected with the newly identified activity is at the moment unclear, although the group is acknowledged to leverage spear-phishing and social engineering assaults to activate the an infection chain.
The beginning place of the attack is a ZIP archive that purports to be about Korean military services background and which consists of two files: A Hangul Phrase Processor document and an executable.
Launching the executable benefits in the retrieval of a PowerShell script from an attacker-managed server, which, in flip, exports information about the compromised sufferer to a GitHub repository and downloads extra PowerShell code by indicates of a Windows shortcut (LNK) file.
Zscaler said it uncovered the GitHub account, designed on February 13, 2024, briefly hosting the TRANSLATEXT extension below the identify “GoogleTranslate.crx,” while its shipping approach is presently mysterious.

“These data files ended up existing in the repository on March 7, 2024, and deleted the upcoming working day, implying that Kimsuky intended to minimize exposure and use the malware for a limited time period to target specific folks,” security researcher Seongsu Park said.
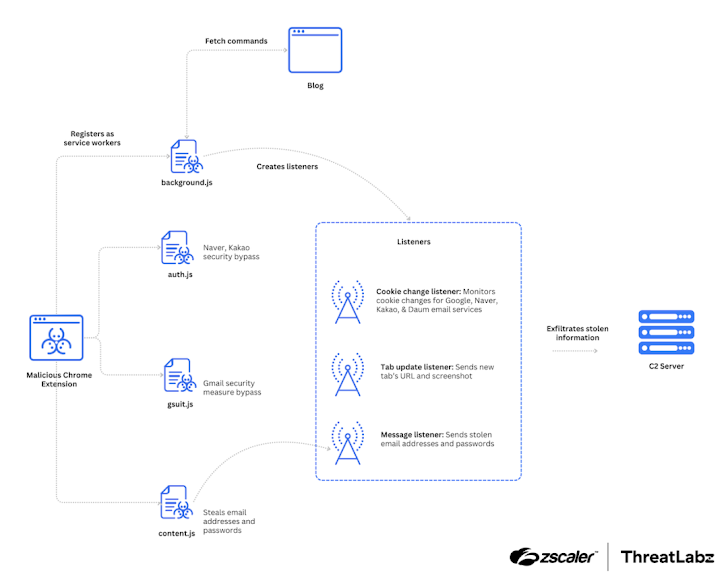
TRANSLATEXT, which masquerades as Google Translate, incorporates JavaScript code to bypass security steps for products and services like Google, Kakao, and Naver siphon email addresses, qualifications, and cookies capture browser screenshots and exfiltrate stolen info.
It is also developed to fetch instructions from a Blogger Blogspot URL in purchase to consider screenshots of recently opened tabs and delete all cookies from the browser, between many others.
“1 of the most important goals of the Kimsuky team is to conduct surveillance on academic and government personnel in purchase to acquire worthwhile intelligence,” Park explained.
Identified this report exciting? Follow us on Twitter and LinkedIn to go through more unique content material we post.
Some parts of this article are sourced from:
thehackernews.com


 GitLab Releases Patch for Critical CI/CD Pipeline Vulnerability and 13 Others
GitLab Releases Patch for Critical CI/CD Pipeline Vulnerability and 13 Others