Russian corporations have been specific by a cybercrime gang known as ExCobalt utilizing a formerly unfamiliar Golang-centered backdoor identified as GoRed.
“ExCobalt focuses on cyber espionage and incorporates many users lively since at minimum 2016 and presumably after aspect of the notorious Cobalt Gang,” Constructive Systems scientists Vladislav Lunin and Alexander Badayev mentioned in a specialized report released this 7 days.
“Cobalt attacked economic establishments to steal cash. One particular of Cobalt’s hallmarks was the use of the CobInt tool, a little something ExCobalt started to use in 2022.”

Attacks mounted by the risk actor have singled out a variety of sectors in Russia around the previous yr, which includes governing administration, facts technology, metallurgy, mining, software enhancement, and telecommunications.
Original obtain to environments is facilitated by taking benefit of a earlier compromised contractor and a source chain attack, whereby the adversary contaminated a element made use of to make the goal firm’s reputable software package, suggesting a large diploma of sophistication.
The modus operandi involves the use of several instruments like Metasploit, Mimikatz, ProcDump, SMBExec, Spark RAT for executing instructions on the contaminated hosts, and Linux privilege escalation exploits (CVE-2019-13272, CVE-2021-3156, CVE-2021-4034, and CVE-2022-2586).
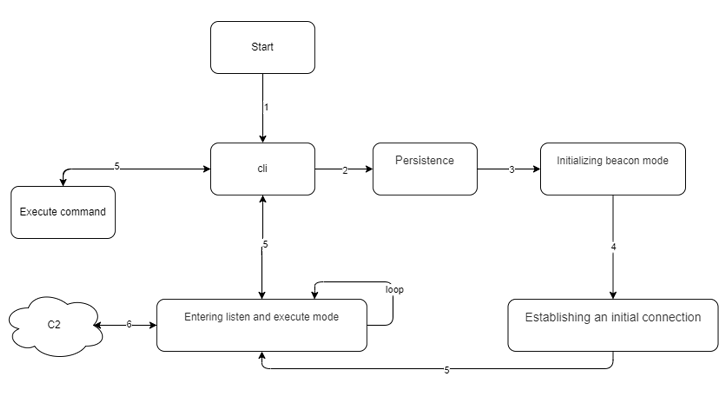
GoRed, which has gone through various iterations due to the fact its inception, is a detailed backdoor that enables the operators to execute commands, obtain qualifications, and harvest particulars of energetic processes, network interfaces, and file techniques. It utilizes the Remote Course of action Simply call (RPC) protocol to talk with its command-and-manage (C2) server.

What is actually much more, it supports a quantity of history commands to observe for information of interest and passwords as perfectly as empower reverse shell. The gathered information is then exported to the attacker-managed infrastructure.
“ExCobalt carries on to demonstrate a large degree of action and determination in attacking Russian providers, constantly adding new tools to its arsenal and bettering its strategies,” the scientists reported.
“In addition, ExCobalt demonstrates flexibility and flexibility by supplementing its toolset with modified normal utilities, which support the team to conveniently bypass security controls and adapt to adjustments in protection methods.”
Located this article interesting? Comply with us on Twitter and LinkedIn to go through extra exclusive content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Warning: New Adware Campaign Targets Meta Quest App Seekers
Warning: New Adware Campaign Targets Meta Quest App Seekers