A new marketing campaign is tricking customers searching for the Meta Quest (formerly Oculus) software for Windows into downloading a new adware family members identified as AdsExhaust.
“The adware is able of exfiltrating screenshots from infected gadgets and interacting with browsers utilizing simulated keystrokes,” cybersecurity company eSentire explained in an evaluation, adding it identified the action earlier this thirty day period.
“These functionalities enable it to automatically simply click by ads or redirect the browser to particular URLs, creating income for the adware operators.”
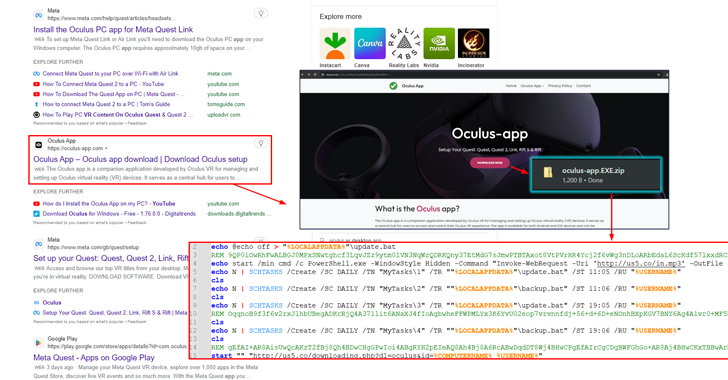
The original infection chain requires surfacing the bogus web-site (“oculus-app[.]com”) on Google lookup results webpages making use of lookup engine optimization (Seo) poisoning methods, prompting unsuspecting web page readers to obtain a ZIP archive (“oculus-application.EXE.zip”) that contains a Windows batch script.
The batch script is built to fetch a next batch script from a command-and-handle (C2) server, which, in turn, is made up of a command to retrieve another batch file. It also creates scheduled tasks on the machine to operate the batch scripts at distinctive periods.

This step is followed by the obtain of the legit app onto the compromised host, while at the same time extra Visual Simple Script (VBS) documents and PowerShell scripts are dropped to get IP and method data, seize screenshots, and exfiltrate the info to a distant server (“us11[.]org/in.php”).
The reaction from the server is the PowerShell-primarily based AdsExhaust adware that checks if Microsoft’s Edge browser is running and decides the last time a consumer input happened.
“If Edge is working and the system is idle and exceeds 9 minutes, the script can inject clicks, open up new tabs, and navigate to URLs embedded in the script,” eSentire explained. “It then randomly scrolls up and down the opened site.”
It is really suspected that this behavior is meant to set off factors these as ads on the web page, specifically considering AdsExhaust performs random clicks in just certain coordinates on the screen.
The adware is also capable of closing the opened browser if mouse movement or consumer interaction is detected, developing an overlay to conceal its pursuits to the target, and seeking for the term “Sponsored” in the at the moment opened Edge browser tab in purchase to simply click on the ad with the purpose of inflating ad revenue.
In addition, it really is equipped to fetch a record of keyword phrases from a remote server and carry out Google lookups for all those search phrases by launching Edge browser periods through the Begin-Process PowerShell command.
“AdsExhaust is an adware threat that cleverly manipulates consumer interactions and hides its things to do to generate unauthorized earnings,” the Canadian enterprise noted.
“It includes many tactics, these as retrieving destructive code from the C2 server, simulating keystrokes, capturing screenshots, and creating overlays to stay undetected when partaking in destructive pursuits.”
The progress will come as similar fake IT guidance web-sites surfaced through search results are currently being utilised to produce Hijack Loader (aka IDAT Loader), which ultimately prospects to a Vidar Stealer an infection.
What helps make the attack stand out is that the threat actors are also leveraging YouTube video clips to publicize the phony website and working with bots to publish fraudulent opinions, supplying it a veneer of legitimacy to customers on the lookout for answers to tackle a Windows update error (error code 0x80070643).
“This highlights the efficiency of social engineering strategies and the require for end users to be careful about the authenticity of the remedies they obtain on the web,” eSentire mentioned.

The disclosure also arrives on the heels of a malpsam marketing campaign concentrating on people in Italy with bill-themed ZIP archive lures to produce a Java-centered remote obtain trojan named Adwind (aka AlienSpy, Frutas, jRAT, JSocket, Sockrat, and Unrecom).
“Upon extraction the user is served with .HTML information this sort of as Bill.html or Document.html that guide to malicious .jar files,” Broadcom-owned Symantec said.
“The ultimate dropped payload is Adwind distant accessibility trojan (RAT) that allows the attackers manage over the compromised endpoint as nicely as private facts assortment and exfiltration.”
Discovered this report fascinating? Abide by us on Twitter and LinkedIn to examine additional distinctive content material we publish.
Some parts of this article are sourced from:
thehackernews.com

 U.S. Treasury Sanctions 12 Kaspersky Executives Amid Software Ban
U.S. Treasury Sanctions 12 Kaspersky Executives Amid Software Ban