Installers for three diverse program products created by an Indian corporation named Conceptworld have been trojanized to distribute information and facts-thieving malware.
The installers correspond to Notezilla, RecentX, and Copywhiz, in accordance to cybersecurity agency Fast7, which found out the source chain compromise on June 18, 2024. The issue has considering the fact that been remediated by Conceptworld as of June 24 inside of 12 hrs of accountable disclosure.
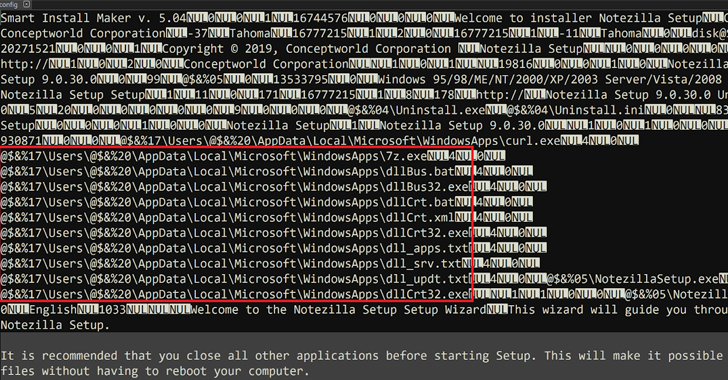
“The installers experienced been trojanized to execute info-stealing malware that has the capacity to down load and execute added payloads,” the enterprise said, including the malicious versions experienced a larger file dimension than their respectable counterparts.
Specially, the malware is geared up to steal browser credentials and cryptocurrency wallet information and facts, log clipboard contents and keystrokes, and down load and execute further payloads on infected Windows hosts. It also sets up persistence utilizing a scheduled job to execute the key payload each and every a few hrs.

It can be at the moment not very clear how the formal area “conceptworld[.]com” was breached to phase the counterfeit installers. Having said that, at the time mounted, the consumer is prompted to continue with the set up approach associated with the genuine application, whilst it is really also built to drop and execute a binary “dllCrt32.exe” that is liable for jogging a batch script “dllCrt.bat.”
Apart from establishing persistence on the device, it really is configured to execute yet another file (“dllBus32.exe”), which, in change, establishes connections with a command-and-regulate (C2) server and incorporates functionality to steal sensitive details as effectively as retrieve and operate much more payloads.
This includes collecting qualifications and other information and facts from Google Chrome, Mozilla Firefox, and many cryptocurrency wallets (e.g., Atomic, Coinomi, Electrum, Exodus, and Guarda). It really is also capable of harvesting documents matching a certain established of extensions (.txt, .doc, .png, and .jpg), logging keystrokes, and grabbing clipboard contents.
“The malicious installers noticed in this case are unsigned and have a file size that is inconsistent with copies of the respectable installer,” Swift7 stated.
Consumers who have downloaded an installer for Notezilla, RecentX, or Copywhiz in June 2024 are advisable to study their systems for indications of compromise and get appropriate action – these as re-imaging the influenced ones – to undo the nefarious modifications.
Uncovered this report intriguing? Adhere to us on Twitter and LinkedIn to read more special articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 End-to-End Secrets Security: Making a Plan to Secure Your Machine Identities
End-to-End Secrets Security: Making a Plan to Secure Your Machine Identities