A likely China-linked condition-sponsored menace actor has been joined to a cyber espionage campaign concentrating on federal government, academic, technology, and diplomatic corporations in Taiwan among November 2023 and April 2024.
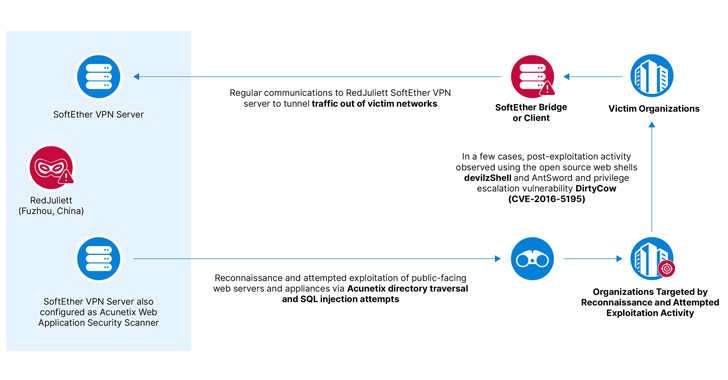
Recorded Future’s Insikt Team is tracking the activity under the identify RedJuliett, describing it as a cluster that operates Fuzhou, China, to help Beijing’s intelligence selection ambitions connected to the East Asian place. It is really also tracked below the names Flax Storm and Ethereal Panda.
Among the other international locations targeted by the adversarial collective involve Djibouti, Hong Kong, Kenya, Laos, Malaysia, the Philippines, Rwanda, South Korea, and the U.S.

In all, as a lot of as 24 target corporations have been observed communicating with the danger actor infrastructure, like authorities businesses in Taiwan, Laos, Kenya, and Rwanda. It’s also estimated to have specific at minimum 75 Taiwanese entities for broader reconnaissance and stick to-on exploitation.
“The group targets internet-experiencing appliances these kinds of as firewalls, load balancers, and company virtual non-public network VPN items for first accessibility, as effectively as making an attempt structured question language SQL injection and listing traversal exploits towards web and SQL applications,” the company explained in a new report published right now.
As formerly documented by CrowdStrike and Microsoft, RedJuliett is regarded to utilize the open up-source application SoftEther to tunnel destructive targeted visitors out of victim networks and leverage living-off-the-land (LotL) methods to fly less than the radar. The team is considered to be active considering that at minimum mid-2021.
“In addition, RedJuliett utilized SoftEther to administer operational infrastructure consisting of each risk actor-managed servers leased from digital non-public server VPS providers and compromised infrastructure belonging to a few Taiwanese universities,” Recorded Long term pointed out.
A successful preliminary obtain is adopted by the deployment of the China Chopper web shell to preserve persistence, alongside other open-source web shells like devilzShell, AntSword, and Godzilla. A number of situations have also entailed the exploitation of a Linux privilege escalation vulnerability known as DirtyCow (CVE-2016-5195).

“RedJuliett is possible interested in gathering intelligence on Taiwan’s financial plan and trade and diplomatic relations with other nations around the world,” it reported.
“RedJuliett, like a lot of other Chinese menace actors, is most likely concentrating on vulnerabilities in internet-experiencing equipment for the reason that these devices have limited visibility and security methods out there, and focusing on them has proven to be an effective way to scale preliminary access.”
Found this article intriguing? Follow us on Twitter and LinkedIn to go through far more special material we article.
Some parts of this article are sourced from:
thehackernews.com

 Multiple Threat Actors Deploying Open-Source Rafel RAT to Target Android Devices
Multiple Threat Actors Deploying Open-Source Rafel RAT to Target Android Devices