The advanced persistent menace known as Wintertime Vivern has been linked to campaigns concentrating on authorities officials in India, Lithuania, Slovakia, and the Vatican since 2021.
The exercise qualified Polish governing administration businesses, the Ukraine Ministry of Overseas Affairs, the Italy Ministry of International Affairs, and people inside the Indian federal government, SentinelOne mentioned in a report shared with The Hacker Information.
“Of individual curiosity is the APT’s concentrating on of non-public enterprises, together with telecommunications businesses that support Ukraine in the ongoing war,” senior threat researcher Tom Hegel said.
Winter Vivern, also tracked as UAC-0114, drew focus very last thirty day period after the Computer Emergency Response Team of Ukraine (CERT-UA) thorough a new malware campaign aimed at point out authorities of Ukraine and Poland to deliver a piece of malware dubbed Aperetif.
Earlier public experiences chronicling the team show that it has leveraged weaponized Microsoft Excel documents containing XLM macros to deploy PowerShell implants on compromised hosts.
Even though the origins of the menace actor are unidentified, the attack patterns recommend that the cluster is aligned with aims that assistance the pursuits of Belarus and Russia’s governments.
UAC-0114 has employed a wide range of strategies, ranging from phishing internet sites to destructive documents, that are tailored to the qualified firm to distribute its custom made payloads and gain unauthorized access to delicate systems.
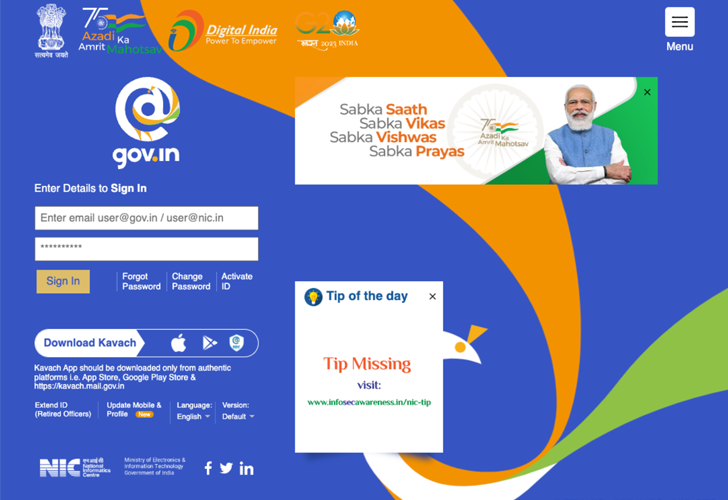
In a person set of assaults observed in mid-2022, Wintertime Vivern established up credential phishing web pages to entice end users of the Indian government’s authentic email service email.gov[.]in.
Standard attack chains include working with batch scripts masquerading as virus scanners to bring about the deployment of the Aperetif trojan from actor-controlled infrastructure such as compromised WordPress internet sites.
Aperetif, a Visible C++-based malware, comes with capabilities to collect target data, keep backdoor access, and retrieve further payloads from the command-and-management (C2) server.
“The Winter season Vivern APT is a resource-minimal but highly innovative group that shows restraint in the scope of their assaults,” Hegel mentioned.
“Their capacity to entice targets into the attacks, and their focusing on of governments and higher-price non-public companies exhibit the amount of sophistication and strategic intent in their operations.”
When Winter Vivern might have managed to evade the community eye for prolonged intervals of time, 1 group which is not way too involved about keeping underneath the radar is Nobelium, which shares overlaps with APT29 (aka BlueBravo, Cozy Bear, or The Dukes).
The Kremlin-backed country-condition team, infamous for the SolarWinds supply chain compromise in December 2020, has ongoing to evolve its toolset, creating new personalized malware like MagicWeb and GraphicalNeutrino.
It has also been attributed to nonetheless another phishing campaign directed versus diplomatic entities in the European Union, with specific emphasis on agencies that are “aiding Ukrainian citizens fleeing the country, and offering assist to the federal government of Ukraine.”
“Nobelium actively collects intelligence data about the nations supporting Ukraine in the Russia-Ukraine war,” BlackBerry reported. “The menace actors meticulously comply with geopolitical situations and use them to increase their probability of a thriving infection.”
The phishing emails, spotted by the firm’s investigation and intelligence team, incorporate a weaponized doc that includes a website link pointing to an HTML file.
WEBINARDiscover the Concealed Hazards of Third-Party SaaS Applications
Are you mindful of the pitfalls linked with third-bash app accessibility to your company’s SaaS apps? Be part of our webinar to find out about the kinds of permissions getting granted and how to lower risk.
RESERVE YOUR SEAT
The weaponized URLs, hosted on a reputable on-line library web page primarily based in El Salvador, options lures relevant to LegisWrite and eTrustEx, the two of which are utilized by E.U. nations for secure doc exchange.
The HTML dropper (dubbed ROOTSAW or EnvyScout) shipped in the marketing campaign embeds an ISO impression, which, in turn, is created to launch a malicious dynamic url library (DLL) that facilitates the delivery of a next-stage malware through Notion’s APIs.
The use of Notion, a popular notice-using application, for C2 communications was beforehand discovered by Recorded Long run in January 2023. It’s worthy of noting that APT29 has utilized various on the web solutions like Dropbox, Google Drive, Firebase, and Trello in an attempt to evade detection.
“Nobelium stays remarkably active, executing various strategies in parallel targeting govt organizations, non-governmental businesses (NGOs), intergovernmental businesses (IGOs), and consider tanks across the U.S., Europe, and Central Asia,” Microsoft stated past month.
The conclusions also appear as organization security agency Proofpoint disclosed aggressive email campaigns orchestrated by a Russia-aligned danger actor termed TA499 (aka Lexus and Vovan) due to the fact early 2021 to trick targets into taking part in recorded phone calls or online video chats and extract precious data.
“The menace actor has engaged in continuous exercise and expanded its concentrating on to include well known businesspeople and large-profile people today that have possibly built large donations to Ukrainian humanitarian attempts or all those building public statements about Russian disinformation and propaganda,” the company mentioned.
Located this write-up attention-grabbing? Abide by us on Twitter and LinkedIn to browse additional distinctive information we article.
Some parts of this article are sourced from:
thehackernews.com


 Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips
Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips