Cybersecurity scientists are calling notice to a zero-working day flaw in Microsoft Office that could be abused to realize arbitrary code execution on affected Windows units.
The vulnerability came to light soon after an impartial cybersecurity investigation group known as nao_sec uncovered a Phrase doc (“05-2022-0438.doc”) that was uploaded to VirusTotal from an IP deal with in Belarus.
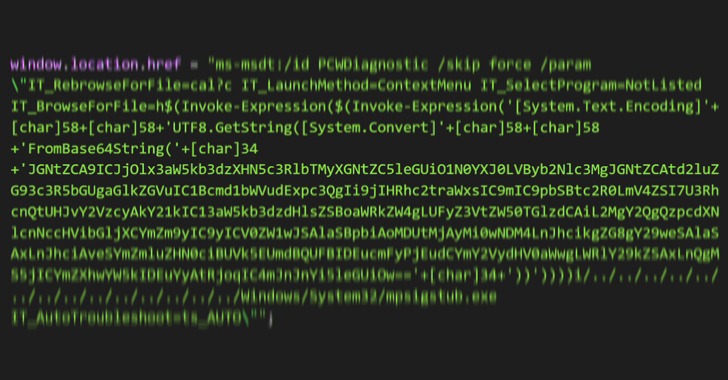
“It employs Word’s exterior link to load the HTML and then utilizes the ‘ms-msdt’ scheme to execute PowerShell code,” the scientists mentioned in a sequence of tweets last 7 days.

According to security researcher Kevin Beaumont, who dubbed the flaw “Follina,” the maldoc leverages Word’s distant template characteristic to fetch an HTML file from a server, which then tends to make use of the “ms-msdt://” URI scheme to run the destructive payload.
MSDT is quick for Microsoft Assist Diagnostics Tool, a utility that is applied to troubleshoot and acquire diagnostic facts for evaluation by guidance gurus to solve a trouble.
“There’s a good deal likely on in this article, but the first problem is Microsoft Term is executing the code by means of msdt (a assist software) even if macros are disabled,” Beaumont stated.

“Safeguarded View does kick in, whilst if you alter the document to RTF sort, it operates without the need of even opening the doc (by using the preview tab in Explorer) permit by yourself Shielded Look at,” the researcher included.
Multiple Microsoft Business variations, together with Workplace, Office environment 2016, and Workplace 2021, are explained to be afflicted, although other variations are anticipated to be susceptible as effectively.
What’s more, Richard Warren of NCC Group managed to demonstrate an exploit on Place of work Qualified Pro with April 2022 managing on an up-to-date Windows 11 device with the preview pane enabled.
“Microsoft are heading to want to patch it throughout all the different products choices, and security sellers will need to have robust detection and blocking,” Beaumont explained. We have attained out to Microsoft for remark, and we will update the story as soon as we hear again.
Found this report exciting? Observe THN on Facebook, Twitter and LinkedIn to go through more unique articles we article.
Some parts of this article are sourced from:
thehackernews.com