Many China-nexus menace actors have been connected to the zero-working day exploitation of 3 security flaws impacting Ivanti appliances (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893).
The clusters are becoming tracked by Mandiant below the monikers UNC5221, UNC5266, UNC5291, UNC5325, UNC5330, and UNC5337. Another group joined to the exploitation spree is UNC3886.
The Google Cloud subsidiary mentioned it has also noticed monetarily determined actors exploiting CVE-2023-46805 and CVE-2024-21887, probable in an try to perform cryptocurrency mining operations.
“UNC5266 overlaps in component with UNC3569, a China-nexus espionage actor that has been observed exploiting vulnerabilities in Aspera Faspex, Microsoft Trade, and Oracle Web Apps Desktop Integrator, amid other people, to obtain preliminary accessibility to focus on environments,” Mandiant scientists mentioned.

The threat actor has been connected to submit-exploitation action main to the deployment of the Sliver command-and-manage (C2) framework, a variant of the WARPWIRE credential stealer, and a new Go-based mostly backdoor dubbed TERRIBLETEA that arrives with command execution, keylogging, port scanning, file technique interaction, and display screen capturing capabilities.
UNC5330, which has been noticed combining CVE-2024-21893 and CVE-2024-21887 to breach Ivanti Hook up Safe VPN appliances at least due to the fact February 2024, has leveraged custom made malware these kinds of as TONERJAM and PHANTOMNET for facilitating put up-compromise steps –
- PHANTOMNET – A modular backdoor that communicates utilizing a personalized communication protocol more than TCP and employs a plugin-based process to obtain and execute extra payloads
- TONERJAM – A launcher that is built to decrypt and execute PHANTOMNET
Aside from utilizing Windows Management Instrumentation (WMI) to conduct reconnaissance, move laterally, manipulate registry entries, and create persistence, UNC5330 is regarded to compromise LDAP bind accounts configured on the infected equipment in get to domain admin entry.
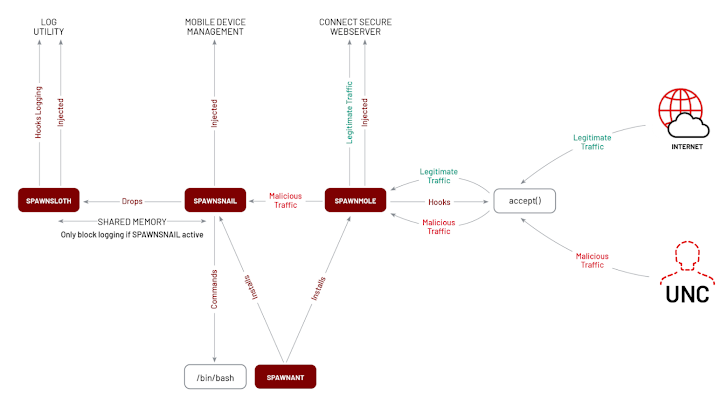
A different notable China-connected espionage actor is UNC5337, which is claimed to have infiltrated Ivanti products as early as January 2024 working with CVE-2023-46805 and CVE-2024 to produce a tailor made malware toolset known as SPAWN that includes four unique parts that get the job done in tandem to perform as a stealthy and persistent backdoor –
- SPAWNSNAIL – A passive backdoor that listens on localhost and is geared up to launch an interactive bash shell as nicely as start SPAWNSLOTH
- SPAWNMOLE – A tunneler utility which is able of tunneling destructive targeted visitors to a unique host
- SPAWNANT – An installer that is responsible for guaranteeing the persistence of SPAWNMOLE and SPAWNSNAIL by using edge of a coreboot installer operate
- SPAWNSLOTH – A log tampering program that disables logging and log forwarding to an exterior syslog server when the SPAWNSNAIL implant is jogging
Mandiant has assessed with medium self confidence that UNC5337 and UNC5221 are one particular and the exact threat team, noting the SPAWN device is “designed to help very long-term entry and keep away from detection.”

UNC5221, which was earlier attributed to web shells this sort of as BUSHWALK, CHAINLINE, FRAMESTING, and LIGHTWIRE, has also unleashed a Perl-primarily based web shell referred to as ROOTROT which is embedded into a reputable Connect Protected .ttc file situated at “/data/runtime/tmp/tt/setcookie.thtml.ttc” by exploiting CVE-2023-46805 and CVE-2024-21887.
A profitable deployment of the web shell is followed by network reconnaissance and lateral motion, in some instances, ensuing in the compromise of a vCenter server in the sufferer network by means of a Golang backdoor termed BRICKSTORM.
“BRICKSTORM is a Go backdoor concentrating on VMware vCenter servers,” Mandiant researchers discussed. “It supports the means to established by itself up as a web server, accomplish file process and listing manipulation, accomplish file operations these kinds of as add/obtain, run shell instructions, and execute SOCKS relaying.”
The past amongst the five China-dependent teams tied to the abuse of Ivanti security flaws is UNC5291, which Mandiant stated possible has associations with an additional hacking group UNC3236 (aka Volt Typhoon), largely owing to its targeting of tutorial, electricity, protection, and health and fitness sectors.
“Activity for this cluster started off in December 2023 focusing on Citrix Netscaler ADC and then shifted to emphasis on Ivanti Hook up Secure equipment just after facts were manufactured general public in mid-Jan. 2024,” the company mentioned.
The findings the moment again underscore the menace confronted by edge appliances, with the espionage actors using a mix of zero-day flaws, open-supply tooling, and customized backdoors to tailor their tradecraft depending on their targets to evade detection for extended intervals of time.
Uncovered this article appealing? Comply with us on Twitter and LinkedIn to go through additional distinctive material we post.
Some parts of this article are sourced from:
thehackernews.com


 Vietnam-Based Hackers Steal Financial Data Across Asia with Malware
Vietnam-Based Hackers Steal Financial Data Across Asia with Malware