A forensic assessment of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters related with illicit action and dollars laundering, which include detecting felony proceeds despatched to a crypto trade and previously unknown wallets belonging to a Russian darknet market place.
The results come from Elliptic in collaboration with researchers from the MIT-IBM Watson AI Lab.
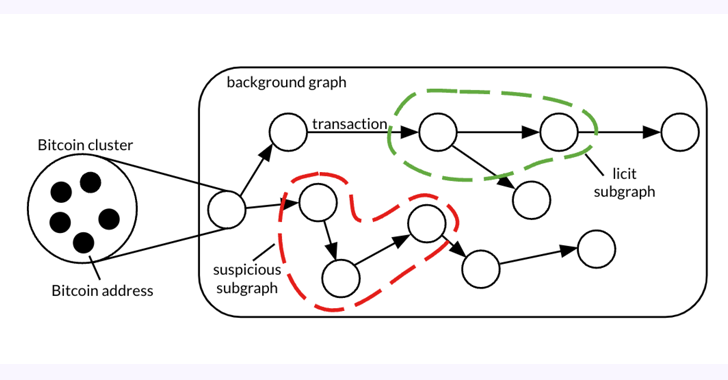
The 26 GB dataset, dubbed Elliptic2, is a “large graph dataset containing 122K labeled subgraphs of Bitcoin clusters in a history graph consisting of 49M node clusters and 196M edge transactions,” the co-authors stated in a paper shared with The Hacker News.
Elliptic2 builds on the Elliptic Facts Established (aka Elliptic1), a transaction graph that was manufactured community in July 2019 with the intention of combating economic crime using graph convolutional neural networks (GCNs).

The thought, in a nutshell, is to uncover illicit activity and revenue laundering styles by getting benefit of blockchain’s pseudonymity and combining it with information about the existence of licit (e.g., exchange, wallet supplier, miner, and so forth.) and illicit services (e.g., darknet market, malware, terrorist organizations, Ponzi plan, etc.) on the network.
“Applying equipment learning at the subgraph level – i.e., the groups of transactions that make up scenarios of cash laundering – can be successful at predicting regardless of whether crypto transactions represent proceeds of criminal offense,” Tom Robinson, main scientist and co-founder of Elliptic, told The Hacker Information.
“This is different to common crypto AML methods, which rely on tracing resources from known illicit wallets, or sample-matching with recognized revenue laundering methods.”
The review, which experimented with three diverse subgraph classification approaches on Elliptic2, these types of as GNN-Seg, Sub2Vec, and GLASS, recognized subgraphs that represented crypto trade accounts probably engaged in illegitimate action.
Additionally, it has created it achievable to trace back the supply of funds connected with suspicious subgraphs to various entities, which include a cryptocurrency mixer, a Panama-based mostly Ponzi scheme, and an invite-only Russian dark web forum.
Robinson mentioned just considering the “condition” – the nearby buildings inside of a elaborate network – of the cash laundering subgraphs proved to be an now powerful way to flag legal action.

More examination of the subgraphs predicted utilizing the properly trained GLASS model has also recognized regarded cryptocurrency laundering designs, this sort of as the presence of peeling chains and nested products and services.
“A peeling chain is exactly where a modest amount of money of cryptocurrency is ‘peeled’ to a location address, though the remainder is despatched to yet another address less than the user’s management,” Robinson explained. “This occurs regularly to kind a peeling chain. The pattern can have genuine monetary privateness purposes, but it can also be indicative of revenue laundering, in particular the place the ‘peeled’ cryptocurrency is repeatedly sent to an exchange company.”
“This is a recognised crypto laundering method and has an analogy in ‘smurfing’ in regular finance – so the simple fact that our equipment discovering method independently determined it is encouraging.”
As for the up coming methods, the exploration is envisioned to target on growing the accuracy and precision of these procedures, as very well as extending the operate to additional blockchains, Robinson extra.
Found this post attention-grabbing? Stick to us on Twitter and LinkedIn to go through much more exclusive articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 Android Malware Wpeeper Uses Compromised WordPress Sites to Hide C2 Servers
Android Malware Wpeeper Uses Compromised WordPress Sites to Hide C2 Servers