A new malware referred to as Cuttlefish is focusing on tiny place of work and home office environment (SOHO) routers with the goal of stealthily checking all site visitors via the gadgets and acquire authentication information from HTTP GET and Put up requests.
“This malware is modular, made principally to steal authentication content observed in web requests that transit the router from the adjacent local region network (LAN),” the Black Lotus Labs group at Lumen Technologies said in a report revealed nowadays.
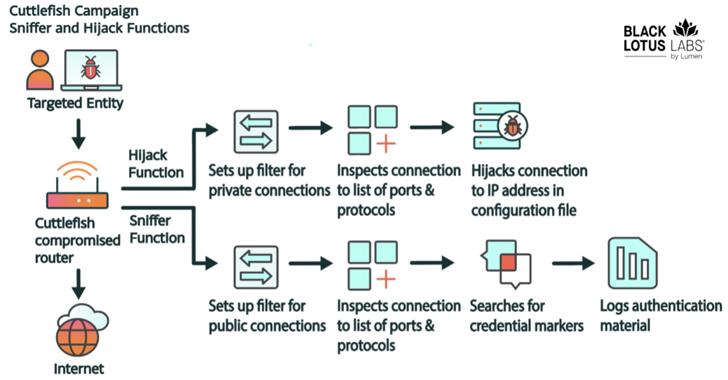
“A secondary functionality presents it the ability to accomplish both DNS and HTTP hijacking for connections to non-public IP house, related with communications on an interior network.”
There is supply code evidence suggesting overlaps with a further previously acknowledged exercise cluster known as HiatusRAT, though no shared victimology has been observed to date. It’s said that these two functions are jogging concurrently.

Cuttlefish has been energetic since at the very least July 27, 2023, with the latest campaign operating from October 2023 via April 2024 and predominantly infecting 600 unique IP addresses linked with two Turkish telecom vendors.
The specific preliminary obtain vector applied to compromise networking machines is unclear. However, a productive foothold is followed by the deployment of a bash script that gathers host info, these types of as the contents of /and many others, running processes, energetic connections, and mounts, and exfiltrates the details to an actor-managed area (“kkthreas[.]com/upload”).

It subsequently downloads and executes the Cuttlefish payload from a devoted server depending on the router architecture (e.g., Arm, i386, i386_i686, i386_x64, mips32, and mips64).
A noteworthy element is that the passive sniffing of the network packets is generally made to one out authentication details involved with public cloud-primarily based solutions this kind of as Alicloud, Amazon Web Services (AWS), Electronic Ocean, CloudFlare, and BitBucket by making an prolonged Berkeley Packet Filter (eBPF).
This performance is ruled based mostly on a ruleset that dictates the malware to possibly hijack site visitors destined to a non-public IP address, or initiate a sniffer function for targeted visitors heading to a public IP in purchase to steal credentials if specified parameters are met.

The hijack rules, for their part, are retrieved and updated from a command-and-control (C2) server set up for this goal right after setting up a protected relationship to it applying an embedded RSA certification.
The malware is also outfitted to act as a proxy and a VPN to transmit the captured data by means of the infiltrated router, thereby enabling the menace actors to use the stolen qualifications to access focused assets.
“Cuttlefish signifies the most current evolution in passive eavesdropping malware for edge networking products […] as it brings together a number of characteristics,” the cybersecurity business mentioned.
“It has the skill to carry out route manipulation, hijack connections, and employs passive sniffing capacity. With the stolen important materials, the actor not only retrieves cloud resources linked with the qualified entity but gains a foothold into that cloud ecosystem.”
Observed this short article attention-grabbing? Follow us on Twitter and LinkedIn to read a lot more distinctive material we publish.
Some parts of this article are sourced from:
thehackernews.com

 Bitcoin Forensic Analysis Uncovers Money Laundering Clusters and Criminal Proceeds
Bitcoin Forensic Analysis Uncovers Money Laundering Clusters and Criminal Proceeds