A by no means-in advance of-viewed botnet named Goldoon has been noticed concentrating on D-Link routers with a almost 10 years-aged critical security flaw with the purpose of applying the compromised gadgets for more assaults.
The vulnerability in problem is CVE-2015-2051 (CVSS score: 9.8), which has an effect on D-Link DIR-645 routers and lets remote attackers to execute arbitrary commands by signifies of specifically crafted HTTP requests.
“If a focused device is compromised, attackers can achieve total command, enabling them to extract program info, build conversation with a C2 server, and then use these gadgets to start further attacks, this sort of as distributed denial-of-assistance (DDoS),” Fortinet FortiGuard Labs researchers Cara Lin and Vincent Li stated.
Telemetry facts from the network security firm points to a spike in the botnet activity around April 9, 2024.
It all commences with the exploitation of CVE-2015-2051 to retrieve a dropper script from a remote server, which is responsible for responsible for downloading the up coming-stage payload for unique Linux program architectures, including aarch64, arm, i686, m68k, mips64, mipsel, powerpc, s390x, sparc64, x86-64, sh4, riscv64, DEC Alpha, and PA-RISC.

The payload is subsequently introduced on the compromised system and functions as a downloader for the Goldoon malware from a remote endpoint, after which the dropper removes the executed file and then deletes itself in a bid to address up the path and fly below the radar.
Any try to accessibility the endpoint straight by means of a web browser displays the error concept: “Sorry, you are an FBI Agent & we are unable to aid you 🙁 Go away or I will kill you :)”
Goldoon, besides environment up persistence on the host employing various autorun approaches, establishes call with a command-and-control (C2) server to await instructions for follow-up actions.
This consists of an “astounding 27 unique procedures” to pull off DDoS flood attacks applying various protocols like DNS, HTTP, ICMP, TCP, and UDP.
“Though CVE-2015-2051 is not a new vulnerability and presents a minimal attack complexity, it has a critical security affect that can lead to distant code execution,” the researchers reported.
The improvement arrives as botnets keep on to evolve and exploit as numerous gadgets as achievable, even as cybercriminals and sophisticated persistent risk (APT) actors alike have shown an curiosity in compromised routers for use as an anonymization layer.
“Cybercriminals lease out compromised routers to other criminals, and most most likely also make them readily available to commercial household proxy providers,” cybersecurity enterprise Development Micro mentioned in a report.
“Country-state threat actors like Sandworm applied their individual devoted proxy botnets, although APT group Pawn Storm had obtain to a legal proxy botnet of Ubiquiti EdgeRouters.”
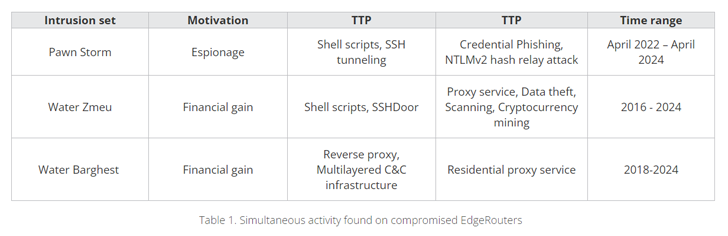
In making use of the hacked routers as proxies, the objective is to disguise traces of their presence and make detection of destructive activities far more challenging by blending their action in with benign standard visitors.
Before this February, the U.S. governing administration took steps to dismantle parts of a botnet called MooBot that, amongst other internet-experiencing units like Raspberry Pi and VPS servers, generally leveraged Ubiquiti EdgeRouters.

Craze Micro reported it noticed the routers staying employed for Protected Shell (SSH) brute forcing, pharmaceutical spam, using server information block (SMB) reflectors in NTLMv2 hash relay assaults, proxying stolen credentials on phishing internet sites, multi-goal proxying, cryptocurrency mining, and sending spear phishing email messages.
Ubiquiti routers have also come beneath assault from an additional menace actor that infects these equipment with a malware dubbed Ngioweb, which are then applied as exit nodes in a commercially accessible household proxy botnet.
The conclusions even further underscore the use of different malware family members to wrangle the routers into a network that risk actors could management, correctly turning them into covert listening posts able of monitoring all network site visitors.
“Internet routers continue to be a well known asset for risk actors to compromise because they normally have lessened security monitoring, have considerably less stringent password insurance policies, are not up-to-date regularly, and may well use effective working techniques that lets for installation of malware these kinds of as cryptocurrency miners, proxies, distributed denial of provider (DDoS malware), destructive scripts, and web servers,” Trend Micro stated.
Uncovered this write-up fascinating? Observe us on Twitter and LinkedIn to read through a lot more special content we submit.
Some parts of this article are sourced from:
thehackernews.com


 CISA Warns of Active Exploitation of Severe GitLab Password Reset Vulnerability
CISA Warns of Active Exploitation of Severe GitLab Password Reset Vulnerability