A new QBot malware campaign is leveraging hijacked organization correspondence to trick unsuspecting victims into setting up the malware, new findings from Kaspersky reveal.
The hottest action, which commenced on April 4, 2023, has mostly specific end users in Germany, Argentina, Italy, Algeria, Spain, the U.S., Russia, France, the U.K., and Morocco.
QBot (aka Qakbot or Pinkslipbot) is a banking trojan which is recognized to be active considering the fact that at least 2007. In addition to stealing passwords and cookies from web browsers, it doubles up as a backdoor to inject following-phase payloads these as Cobalt Strike or ransomware.
Distributed by way of phishing campaigns, the malware has witnessed consistent updates during its life span that pack in anti-VM, anti-debugging, and anti-sandbox strategies to evade detection. It has also emerged as the most prevalent malware for the thirty day period of March 2023, for every Check Issue.
“Early on, it was dispersed by contaminated web sites and pirated software,” Kaspersky scientists mentioned, detailing QBot’s distribution solutions. “Now the banker is sent to possible victims by way of malware currently residing on their computers, social engineering, and spam mailings.”
Email thread hijacking attacks are not new. It happens when cybercriminals insert them selves into existing small business conversations or initiate new discussions based on information and facts earlier gleaned by compromised email accounts.
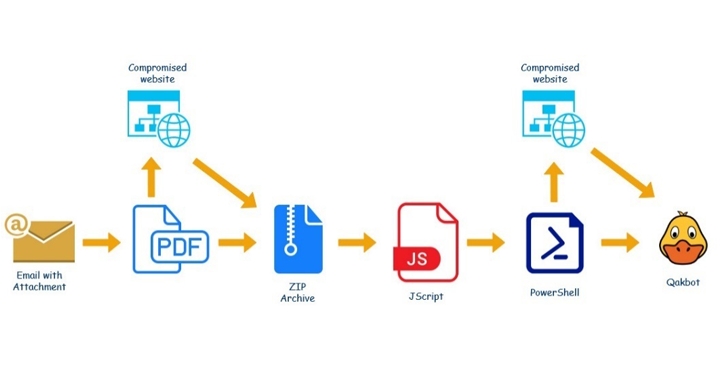
The aim is to entice victims into opening malicious links or destructive attachments, in this circumstance, an enclosed PDF file that masquerades as a Microsoft Business office 365 or Microsoft Azure warn.
Upcoming WEBINARMaster the Artwork of Dark Web Intelligence Collecting
Learn the artwork of extracting menace intelligence from the dark web – Join this skilled-led webinar!
Save My Seat!
Opening the doc sales opportunities to the retrieval of an archive file from an contaminated website that, in change, includes an obfuscated Windows Script File (.WSF). The script, for its aspect, incorporates a PowerShell script that downloads destructive DLL from a remote server. The downloaded DLL is the QBot malware.
The findings come as Elastic Security Labs unearthed a multi-phase social engineering marketing campaign that employs weaponized Microsoft Word paperwork to distribute Agent Tesla and XWorm by signifies of a custom .NET-based loader.
Located this post intriguing? Follow us on Twitter and LinkedIn to read more exclusive articles we article.
Some parts of this article are sourced from:
thehackernews.com

 Qbot Banking Trojan Increasingly Delivered Via Business Emails
Qbot Banking Trojan Increasingly Delivered Via Business Emails