An updated edition of a malware loader codenamed IceXLoader is suspected of owning compromised 1000’s of individual and business Windows equipment across the planet.
IceXLoader is a commodity malware that’s sold for $118 on underground message boards for a life span license. It can be chiefly utilized to down load and execute supplemental malware on breached hosts.
This earlier June, Fortinet FortiGuard Labs reported it uncovered a edition of the trojan created in the Nim programming language with the intention of evading assessment and detection.
“Though the version identified in June (v3.) looked like a perform-in-development, we recently observed a newer v3.3.3 loader which seems to be to be totally functionable and contains a multi-phase shipping chain,” Natalie Zargarov, cybersecurity researcher at Minerva Labs, mentioned in a report posted Tuesday.
IceXLoader is usually distributed by phishing strategies, with emails that contains ZIP archives working as a bring about to deploy the malware. An infection chains have leveraged IceXLoader to supply DarkCrystal RAT and cryptocurrency miners.
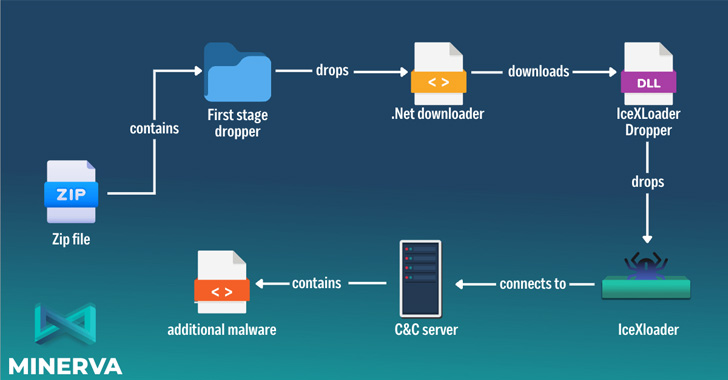
In the attack sequence specific by Minerva Labs, the ZIP file has been found to harbor a dropper, which drops a .NET-centered downloader that, as the title indicates, obtain a PNG picture (“Ejvffhop.png”) from a challenging-coded URL.
This graphic file, a further dropper, is subsequently transformed into an array of bytes, properly allowing for it to decrypt and inject IceXLoader into a new approach employing a method known as approach hollowing.


Edition 3.3.3 of IceXLoader, like its predecessor, is created in Nim and is geared up to obtain process metadata, all of which is exfiltrated to a distant attacker-managed area, although awaiting even more instructions issued by the server.
The commands involve the means to restart and uninstall the malware loader and halt its execution. But its primary attribute is to obtain and execute up coming-stage malware on disk or filelessly in memory.
Minerva Labs reported a SQLite database file hosted in the command-and-manage (C2) server is being continually up to date with facts about thousands of victims, introducing it really is in the process of notifying impacted businesses.
Observed this post interesting? Follow THN on Facebook, Twitter and LinkedIn to browse extra special material we publish.
Some parts of this article are sourced from:
thehackernews.com

 Microsoft Patches Six Zero-Day Bugs this Month
Microsoft Patches Six Zero-Day Bugs this Month