Like antivirus software program, vulnerability scans depend on a database of identified weaknesses.
That is why web sites like VirusTotal exist, to give cyber practitioners a probability to see whether or not a malware sample is detected by various virus scanning engines, but this concept has not existed in the vulnerability administration house.
The rewards of working with several scanning engines
Frequently talking, vulnerability scanners goal to make checks for as a lot of vulnerabilities as achievable. However, the number of vulnerabilities uncovered yr on calendar year is now so superior, reaching approximately 30,000 a calendar year, or 80 a day, that it truly is not possible for a single scanning engine to hold up with them all.
As a outcome, even the pretty best, sector-main primary scanners will wrestle to test for each individual known vulnerability out there, and normally they will favour specified sets of computer software known to be used by their shoppers.
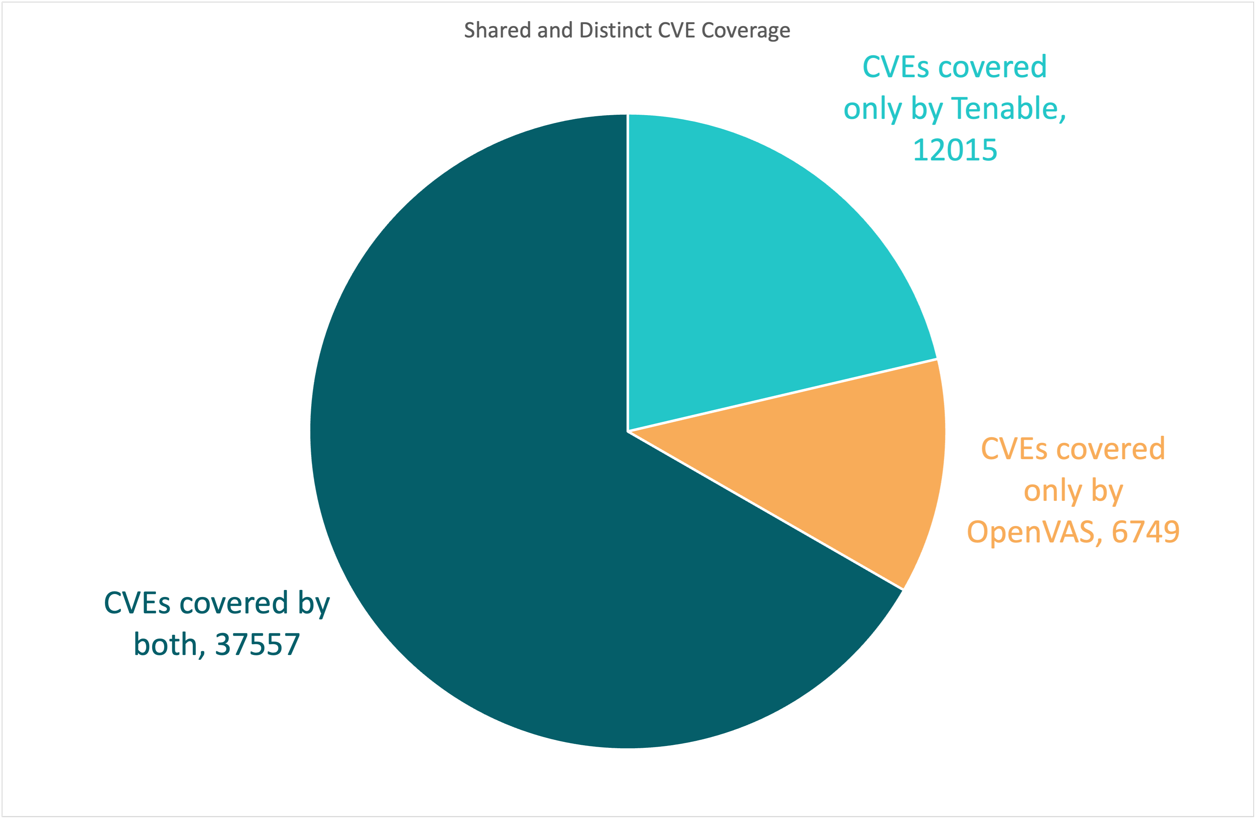
For case in point, Intruder’s investigation from early 2023 which in contrast Tenable’s Nessus and OpenVAS confirmed substantial discrepancies in coverage in between scanners, with just one being frequently more robust in industrial application, and the other favouring open supply:
“Tenable checks for 12,015 CVEs which OpenVAS does not check for and OpenVAS checks for 6,749 CVEs which Tenable does not test for.”
Scanning engine vendors also choose other variables into consideration, like no matter whether a vulnerability has been exploited in the wild, or no matter if it is really in program products which are extremely widely made use of. But even though your preferred scanner may be earning sensible conclusions on which vulnerabilities to compose checks for there could nevertheless be gaps in coverage for your estate.
So it is really a severe actuality that one day you could find out that you have been compromised by means of an attack vector which your vulnerability scanner simply would not have a check for.
This raises significant inquiries for all those hunting to shield their digital estates, not only which scanner they should choose. But whether one scanner is even ample?
The multi-scanning motor tactic
It is apparent that having various complementary scanners would boost protection by obtaining more vulnerabilities, and finding additional about what your attack surface appears like. But functioning many scanning units would be much too significantly for most organisations to afford, both in price range and time constraints.
That’s why the group at Intruder, a foremost Attack Area Management seller, resolved from the get started to include multiple scanning engines, supplying shoppers the widest breadth of checks, when streamlining funds and time constraints by offering them in a solitary system.
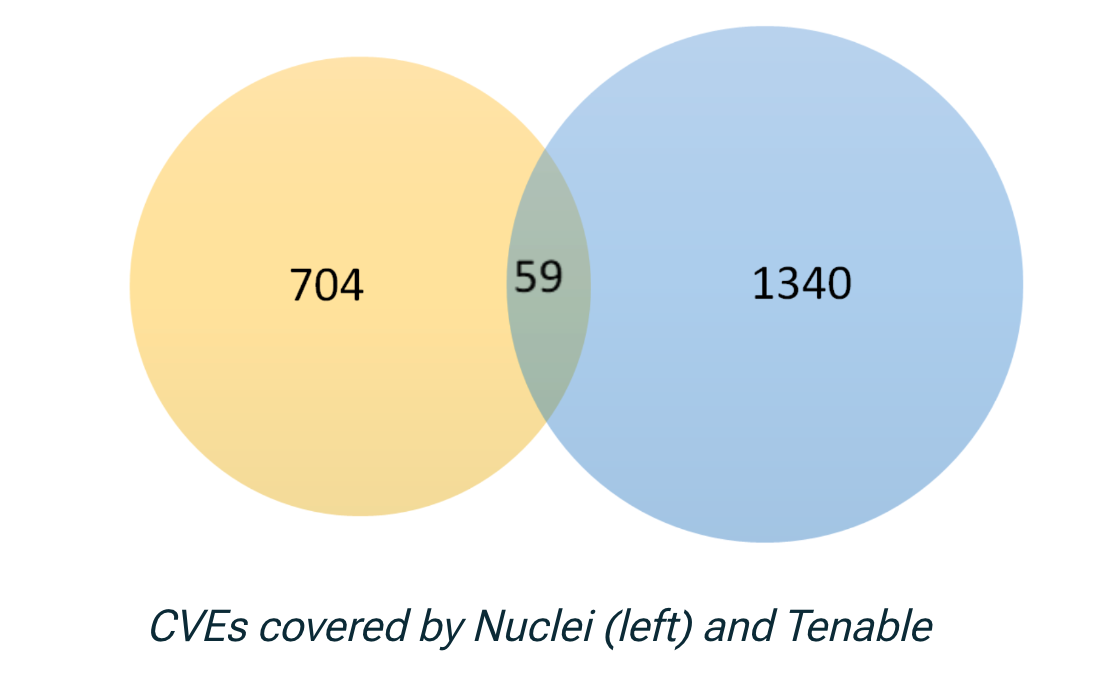
Most not long ago, Intruder has added Nuclei to its suite of vulnerability scanning engines, maximizing its potential to manage and protected attack surfaces.
With around 3,000 additional checks in this original launch, Intruder can give much broader and further protection and discovery abilities that won’t be able to be matched by utilizing a one vulnerability scanner on your own.
What is Nuclei?
Nuclei is an open-supply vulnerability scanning motor, comparable to OpenVAS, which is speedy, extensible, and handles a large array of weaknesses. It’s turn into ever more common with bug bounty hunters, penetration testers and researchers who want to create repeatable checks for significant weaknesses.
These experts, doing the job with the Nuclei advancement crew at ProjectDiscovery, combine their know-how and insights about reducing-edge weaknesses to produce checks really rapidly – which makes scanning as shortly as attainable following a vulnerability is identified.
 An example of a Nuclei check out in the Intruder platform
An example of a Nuclei check out in the Intruder platform
What does Nuclei insert to Intruder?
By integrating Nuclei as a scanning engine, Intruder further improves its vulnerability administration system abilities to test and secure attack surfaces much more effectively.
This includes expanded detection of exposures like login panels that really should not be exposed to the internet, and expanding the selection of checks for identified vulnerabilities in usually exposed expert services.
Nuclei augments Intruder’s present scanning engines, this kind of as Tenable and OpenVAS, by providing a deeper and broader check out of your attack area, as a result enabling much better safety by uncovering risks that would stay undetected by a single scanning engine.
Visualize and limit your publicity with Intruder
The measurement of your attack floor, and how properly it is really managed, is carefully tied to your risk of opportunistic attackers exploiting your methods. The a lot less you expose, and the far more hardened the services you expose are, the tougher it is for an attacker to exploit a weakness.
You can lessen your attack area by consistently monitoring for adjustments with an automatic vulnerability administration device like Intruder.
 A screenshot of Intruder’s attack area management dashboard.
A screenshot of Intruder’s attack area management dashboard.
Intruder’s platform will allow you to:
- Discover property: when new cloud expert services are spun up and exposed to the internet, Intruder kicks off a scan to come across any vulnerabilities so you can fix them speedier.
- Know what’s uncovered: get comprehensive visibility of your network perimeter, keep track of energetic and unresponsive targets, discover improvements, keep an eye on expiring certificates, and see any ports, solutions or protocols that shouldn’t be uncovered to the internet.
- Detect additional: Intruder uses several scanners to discover vulnerabilities and exposures throughout your attack surface supplying you the finest visibility.
- Focus on the big issues: see results prioritized primarily based on context, so you can concentration on the most pressing issues without squandering time sifting by the noise.
Discovered this short article fascinating? This posting is a contributed piece from a single of our valued companions. Comply with us on Twitter and LinkedIn to read through more exclusive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Dropbox Discloses Breach of Digital Signature Service Affecting All Users
Dropbox Discloses Breach of Digital Signature Service Affecting All Users