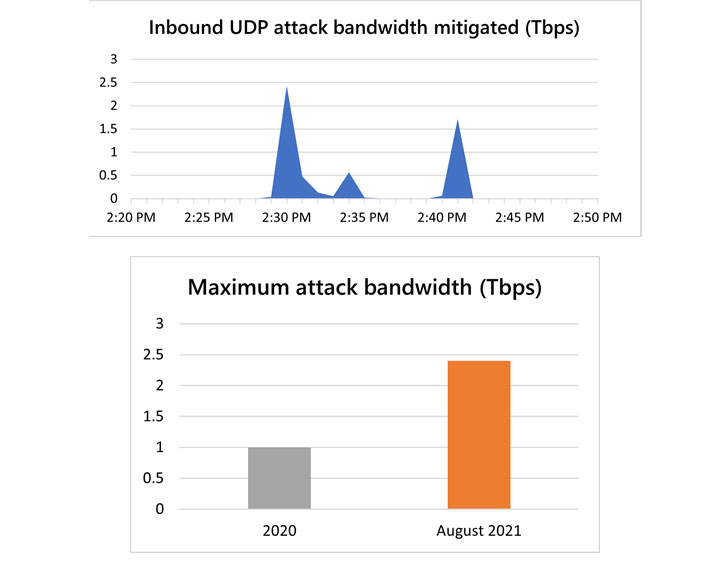
Microsoft on Monday exposed that its Azure cloud system mitigated a 2.4 Tbps distributed denial-of-service (DDoS) attack in the very last week of August concentrating on an unnamed client in Europe, surpassing a 2.3 Tbps attack stopped by Amazon Web Providers in February 2020.
“This is 140 p.c better than 2020’s 1 Tbps attack and greater than any network volumetric event beforehand detected on Azure,” Amir Dahan, senior system manager for Azure Networking, mentioned in a article, contacting it a “UDP reflection” long lasting for about 10 minutes.

Reflected amplification assaults are a sort of denial of service attacks wherein a menace actor usually takes benefit of the connectionless mother nature of UDP protocol with spoofed requests so as to overwhelm a goal server or network with a flood of packets, resulting in disruption or rendering the server and its surrounding infrastructure unavailable.
The attack is mentioned to have originated from a botnet of close to 70,000 compromised devices generally situated across the Asia-Pacific location, such as Malaysia, Vietnam, Taiwan, Japan, and China, as well as the U.S.
Microsoft said it noticed three quick-lived bursts, each ramping up in seconds to terabit volumes — the very first at 2.4 Tbps, the 2nd at .55 Tbps, and the 3rd at 1.7 Tbps.

Information of the DDoS attack will come a month just after Russian internet giant Yandex became the target of a history-breaking distributed denial-of-provider (DDoS) attack by a new botnet called Mēris, which battered the firm’s web infrastructure with tens of millions of HTTP requests, ahead of hitting a peak of 21.8 million requests per second (RPS).
“Bad actors, now much more than at any time, continuously appear for techniques to get purposes offline,” Dahan said. “Attacks of this measurement demonstrate the ability of lousy actors to wreak havoc by flooding targets with gigantic targeted visitors volumes seeking to choke network capacity.”
Found this short article appealing? Observe THN on Facebook, Twitter and LinkedIn to read through additional exclusive information we post.
Some parts of this article are sourced from:
thehackernews.com


 Instagram is testing in-app notifications for service outages
Instagram is testing in-app notifications for service outages