The Keksec danger actor has been joined to a formerly undocumented malware strain, which has been noticed in the wild masquerading as an extension for Chromium-based mostly web browsers to enslave compromised equipment into a botnet.
Called Cloud9 by security firm Zimperium, the destructive browser insert-on will come with a vast variety of characteristics that enables it to siphon cookies, log keystrokes, inject arbitrary JavaScript code, mine crypto, and even enlist the host to carry out DDoS attacks.
The extension “not only steals the data readily available in the course of the browser session but can also put in malware on a user’s unit and subsequently presume handle of the total unit,” Zimperium researcher Nipun Gupta mentioned in a new report.
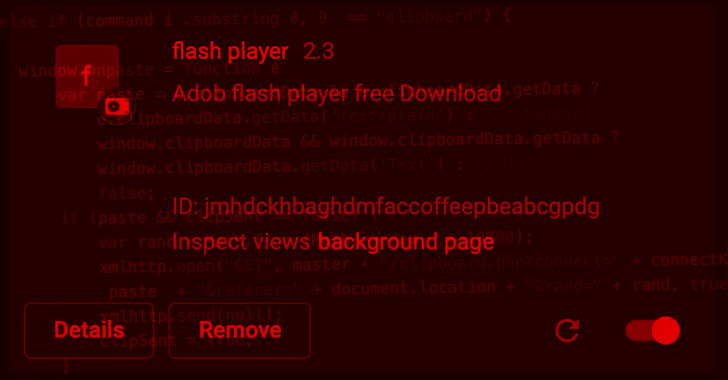
The JavaScript botnet just isn’t dispersed through Chrome Web Store or Microsoft Edge Increase-ons, but fairly as a result of faux executables and rogue internet sites disguised as Adobe Flash Player updates.
As soon as mounted, the extension is designed to inject a JavaScript file identified as “marketing campaign.js” on all internet pages, indicating the malware could also work as a standalone piece of code on any web page, respectable or in any other case, potentially top watering gap attacks.
The JavaScript code will take responsibility for cryptojacking operations, abusing the victim’s computing methods to illicitly mine cryptocurrencies, as properly as inject a second script named “cthulhu.js.”
This attack chain, in change, exploits flaws in web browsers these types of as Mozilla Firefox (CVE-2019-11708, CVE-2019-9810), Internet Explorer (CVE-2014-6332, CVE-2016-0189), and Edge (CVE-2016-7200) to escape the browser sandbox and deploy malware on the process.
The script further functions as a keylogger and a conduit for launching further instructions received from a remote server, letting it to steal clipboard knowledge, browser cookies, and launching layer 7 DDoS assaults from any area.
Zimperium attributed the malware to a danger actor tracked as Keksec (aka Kek Security, Necro, and FreakOut), which has a heritage of building a wide vary of botnet malware, including EnemyBot, for crypto mining and DDoS functions.
The link to Keksec comes from overlaps in the domains that have been beforehand recognized as utilized by the malware group.


The actuality that Cloud9 is JavaScript-centered and is made available both for totally free or a smaller fee on hacker discussion boards helps make it doable for considerably less-qualified cybercriminals to get effortless obtain to low-price tag possibilities for launching assaults concentrating on different browsers and operating devices.
The disclosure will come over a few months just after Zimperium identified a malicious browser insert-on dubbed ABCsoup that posed as a Google Translate tool to strike Russian customers of Google Chrome, Opera, and Mozilla Firefox browsers.
“Consumers should really be qualified on the dangers related with browser extensions exterior of official repositories, and enterprises should really consider what security controls they have in area for this kind of challenges,” Gupta reported.
Located this posting exciting? Stick to THN on Fb, Twitter and LinkedIn to examine much more special material we submit.
Some parts of this article are sourced from:
thehackernews.com

 Advanced RAT AgentTesla Most Prolific Malware in October
Advanced RAT AgentTesla Most Prolific Malware in October