Cybersecurity researchers have thorough a now-patch security flaw impacting the Ollama open up-source synthetic intelligence (AI) infrastructure platform that could be exploited to realize distant code execution.
Tracked as CVE-2024-37032, the vulnerability has been codenamed Probllama by cloud security firm Wiz. Subsequent accountable disclosure on May perhaps 5, 2024, the issue was addressed in variation .1.34 released on Could 7, 2024.
Ollama is a provider for packaging, deploying, working substantial language products (LLMs) locally on Windows, Linux, and macOS units.
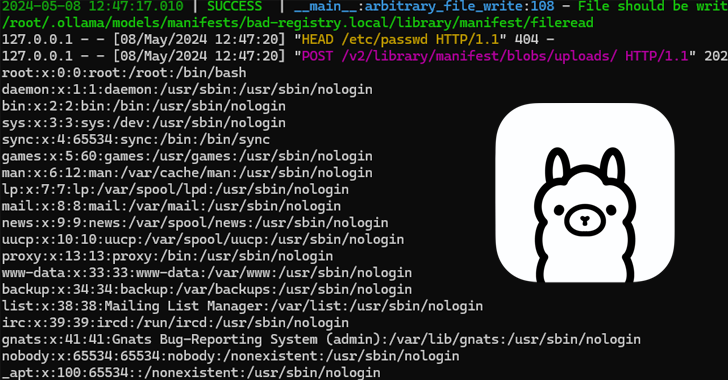
At its core, the issue relates to a scenario of insufficient input validation that success in a route traversal flaw an attacker could exploit to overwrite arbitrary data files on the server and in the long run direct to remote code execution.

The shortcoming demands the danger actor to mail specially crafted HTTP requests to the Ollama API server for prosperous exploitation.
It specifically usually takes benefit of the API endpoint “/api/pull” – which is used to down load a product from the formal registry or from a private repository – to deliver a destructive model manifest file that has a route traversal payload in the digest discipline.
This issue could be abused not only to corrupt arbitrary files on the method, but also to obtain code execution remotely by overwriting a configuration file (“and many others/ld.so.preload”) connected with the dynamic linker (“ld.so”) to consist of a rogue shared library and launch it just about every time prior to executing any software.
Though the risk of remote code execution is minimized to a excellent extent in default Linux installations owing to the truth that the API server binds to localhost, it truly is not the scenario with docker deployments, in which the API server is publicly exposed.
“This issue is incredibly extreme in Docker installations, as the server runs with `root` privileges and listens on `0…0` by default – which enables distant exploitation of this vulnerability,” security researcher Sagi Tzadik reported.
Compounding matters more is the inherent deficiency of authentication involved with Ollama, thus enabling an attacker to exploit a publicly-accessible server to steal or tamper with AI models, and compromise self-hosted AI inference servers.
This also demands that this kind of solutions are secured making use of middleware like reverse proxies with authentication. Wiz reported it recognized in excess of 1,000 Ollama exposed circumstances hosting a lot of AI styles without the need of any safety.

“CVE-2024-37032 is an straightforward-to-exploit remote code execution that affects fashionable AI infrastructure,” Tzadik explained. “Inspite of the codebase becoming rather new and published in fashionable programming languages, classic vulnerabilities these kinds of as Route Traversal stay an issue.”
The growth comes as AI security business Guard AI warned of about 60 security problems influencing numerous open up-supply AI/ML tools, which include critical issues that could lead to info disclosure, entry to limited methods, privilege escalation, and total process takeover.
The most critical of these vulnerabilities is CVE-2024-22476 (CVSS rating 10.), an SQL injection flaw in Intel Neural Compressor software that could allow attackers to download arbitrary data files from the host program. It was tackled in version 2.5..
Found this write-up fascinating? Abide by us on Twitter and LinkedIn to read more unique content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Ease the Burden with AI-Driven Threat Intelligence Reporting
Ease the Burden with AI-Driven Threat Intelligence Reporting