The U.S. Condition Section has introduced financial rewards of up to $15 million for information that could direct to the identification of crucial leaders in just the LockBit ransomware group and the arrest of any specific participating in the operation.
“Because January 2020, LockBit actors have executed in excess of 2,000 assaults towards victims in the United States, and about the entire world, producing expensive disruptions to functions and the destruction or exfiltration of sensitive information,” the State Division stated.
“Far more than $144 million in ransom payments have been produced to get better from LockBit ransomware events.”
The enhancement will come as a sweeping regulation enforcement operation led by the U.K. Countrywide Criminal offense Agency (NCA) disrupted LockBit, a Russia-connected ransomware gang that has been active for extra than 4 yrs, wreaking havoc on enterprise and critical infrastructure entities close to the globe.
Ransomware-as-a-company (RaaS) operations like LockBit and other people do the job by extorting organizations by thieving their delicate info and encrypting them, producing it a beneficial business enterprise product for Russian e-crime groups that act with impunity by having advantage of the fact that they are outdoors of the jurisdiction of Western law enforcement.

The core developers are likely to tap into a network of affiliates who are recruited to carry out the assaults working with LockBit’s malicious program and infrastructure. The affiliates, in change, are identified to invest in entry to targets of curiosity employing preliminary accessibility brokers (IABs).
“LockBit rose to be the most prolific ransomware group given that Conti departed the scene in mid-2022,” Chester Wisniewski, world wide discipline CTO at Sophos, reported.
“The frequency of their assaults, mixed with having no limits to what sort of infrastructure they cripple has also produced them the most harmful in modern many years. Anything that disrupts their operations and sows distrust amongst their affiliate marketers and suppliers is a massive win for regulation enforcement.”
LockBit is also known to be the initially ransomware team to announce a bug bounty plan in 2022, supplying rewards of up to $1 million for finding security issues in web-site and locker software program.
“LockBit’s procedure grew in scale by continually delivering new products functions, furnishing very good client assistance, and at times, advertising and marketing stunts that provided paying men and women to tattoo themselves with the group’s brand,” Intel 471 stated.
“LockBit flipped the script, allowing its affiliate marketers obtain the ransom and trusting them to shell out it a part. This made affiliates self-confident that they have been not likely to drop out on a payment, consequently attracting additional affiliate marketers.”
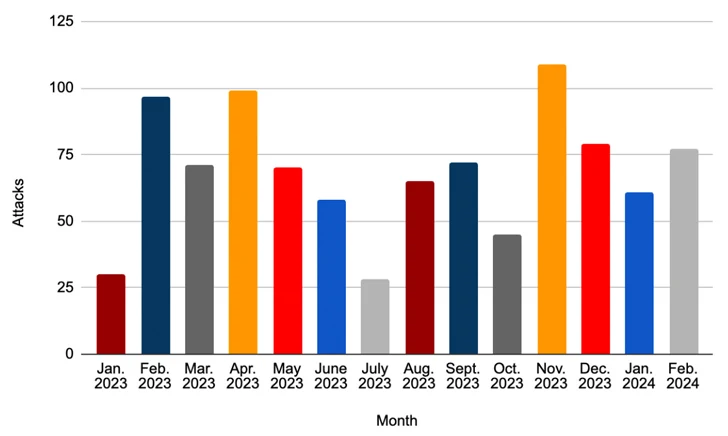
SecureWorks Counter Threat Device (CTU), which is monitoring the team under the title Gold Mystic, claimed it investigated 22 compromises showcasing LockBit ransomware from July 2020 by way of January 2024, some of which relied only on knowledge theft to extort victims.
The cybersecurity enterprise more pointed out that LockBit’s apply of ceding management to its affiliates to deal with ransom negotiation and payments allowed the syndicate to scale up and draw quite a few affiliate marketers above the many years.
LockBit’s takedown adopted a months-lengthy investigation that commenced in April 2022, primary to the arrest of three affiliates in Poland and Ukraine, the indictment in the U.S. of two other alleged users, as nicely as the seizure of 34 servers and 1,000 decryption keys that can aid victims get well their data without the need of earning any payment.

These arrests contain a 38-calendar year-aged gentleman in Warsaw and a “father and son” duo from Ukraine. LockBit is believed to have utilized about 194 affiliate marketers between January 31, 2022, and February 5, 2024, with the actors making use of a bespoke knowledge exfiltration instrument recognised as StealBit.
“StealBit is an illustration of LockBit’s try to provide a complete ‘one-stop shop’ provider to its affiliates,” the NCA reported, introducing the executable is utilised to export the info as a result of the affiliate’s possess infrastructure in advance of StealBit’s in a probable effort to evade detection.
That explained, the fluid construction of these RaaS manufacturers signifies that shutting them down may possibly not decisively effects the legal business, letting them to regroup and resurface less than a diverse name. If the the latest record of very similar takedowns is any sign, it will not be extended right before they rebrand and go on from wherever they still left off.
“Extensive degradation of LockBit’s infrastructure will probably consequence in a shorter cessation in exercise from LockBit operatives prior to they resume functions – both beneath the LockBit title or an alternate banner,” ZeroFox stated.
“Even if we you should not often get a full victory, like has occurred with QakBot, imposing disruption, fueling their anxiety of receiving caught and raising the friction of operating their prison syndicate is continue to a gain,” Wisniewski additional. “We need to continue to band collectively to increase their fees at any time increased until we can place all of them where by they belong – in jail.”
Uncovered this posting exciting? Follow us on Twitter and LinkedIn to study a lot more exceptional articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers
New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers