Cybersecurity scientists have identified two authentication bypass flaws in open up-source Wi-Fi software package observed in Android, Linux, and ChromeOS units that could trick people into becoming a member of a malicious clone of a respectable network or let an attacker to be part of a dependable network with no a password.
The vulnerabilities, tracked as CVE-2023-52160 and CVE-2023-52161, have been learned next a security evaluation of wpa_supplicant and Intel’s iNet Wi-fi Daemon (IWD), respectively.
The flaws “allow attackers to trick victims into connecting to malicious clones of trustworthy networks and intercept their targeted visitors, and join if not protected networks without having needing the password,” Top10VPN claimed in a new study performed in collaboration with Mathy Vanhoef, who has previously uncovered Wi-Fi assaults like KRACK, DragonBlood, and TunnelCrack.

CVE-2023-52161, in individual, permits an adversary to obtain unauthorized obtain to a guarded Wi-Fi network, exposing present people and devices to probable attacks these as malware bacterial infections, knowledge theft, and business email compromise (BEC). It impacts IWD variations 2.12 and lower.
On the other hand, CVE-2023-52160 has an effect on wpa_supplicant variations 2.10 and prior. It is really also the extra pressing of the two flaws owing to the truth that it is really the default application employed in Android units to handle login requests to wi-fi networks.
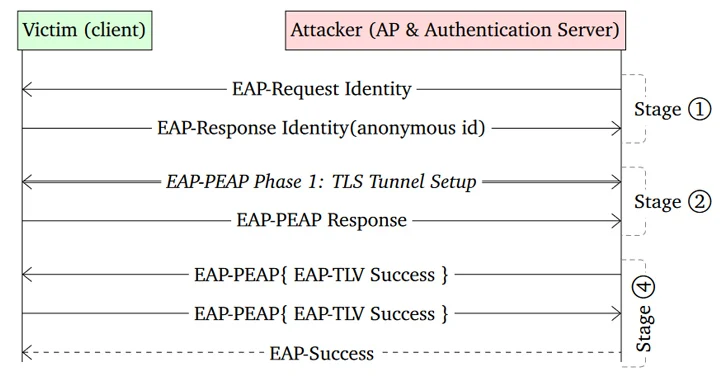
That claimed, it only impacts Wi-Fi consumers that aren’t adequately configured to verify the certificate of the authentication server. CVE-2023-52161, even so, impacts any network that takes advantage of a Linux unit as a wireless access position (WAP).
Profitable exploitation of CVE-2023-52160 financial institutions on the prerequisite that the attacker is in possession of the SSID of a Wi-Fi network to which the sufferer has beforehand linked. It also requires the risk actor to be in physical proximity to the sufferer.
“One particular probable such situation might be where by an attacker walks close to a firm’s setting up scanning for networks just before focusing on an worker leaving the business office,” the scientists claimed.

Important Linux distributions these kinds of as Debian (1, 2), Crimson Hat (1), SUSE (1, 2), and Ubuntu (1, 2) have produced advisories for the two flaws. The wpa_supplicant issue has also been resolved in ChromeOS from versions 118 and afterwards, but fixes for Android are nonetheless to be made available.
“In the meantime, it is critical, hence, that Android consumers manually configure the CA certificate of any saved organization networks to avoid the attack,” Leading10VPN reported.
Observed this report attention-grabbing? Observe us on Twitter and LinkedIn to browse additional unique articles we article.
Some parts of this article are sourced from:
thehackernews.com


 Mustang Panda Targets Asia with Advanced PlugX Variant DOPLUGS
Mustang Panda Targets Asia with Advanced PlugX Variant DOPLUGS