The China-linked danger actor recognized as Mustang Panda has targeted numerous Asian nations around the world using a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
“The piece of customized PlugX malware is dissimilar to the basic kind of the PlugX malware that consists of a accomplished backdoor command module, and that the former is only applied for downloading the latter,” Craze Micro scientists Sunny Lu and Pierre Lee said in a new complex create-up.
Targets of DOPLUGS have been primarily situated in Taiwan, and Vietnam, and to a lesser extent in Hong Kong, India, Japan, Malaysia, Mongolia, and even China.
PlugX is a staple resource of Mustang Panda, which is also tracked as BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Purple Lich, Stately Taurus, TA416, and TEMP.Hex. It is really regarded to be energetic since at minimum 2012, although it initially arrived to gentle in 2017.

The threat actor’s tradecraft involves carrying out properly-solid spear-phishing strategies that are built to deploy custom made malware. It also has a monitor file of deploying its possess personalized PlugX variants this sort of as RedDelta, Thor, Hodur, and DOPLUGS (distributed by means of a marketing campaign named SmugX) considering the fact that 2018.
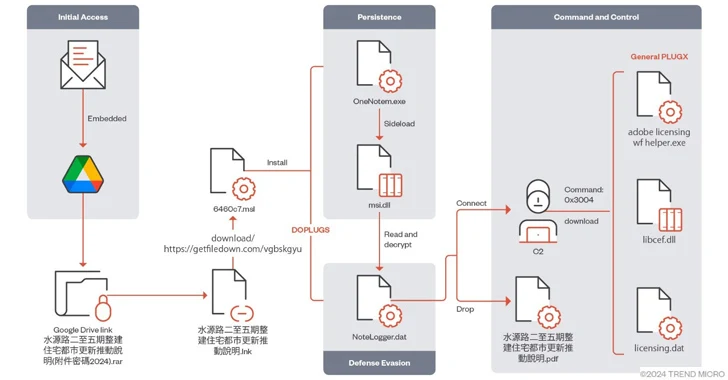
Compromise chains leverage a established of distinctive methods, making use of phishing messages as a conduit to deliver a first-stage payload that, though displaying a decoy doc to the receiver, covertly unpacks a legit, signed executable that is vulnerable to DLL facet-loading in buy to side-load a dynamic-connection library (DLL), which, in transform, decrypts and executes PlugX.
The PlugX malware subsequently retrieves Poison Ivy remote obtain trojan (RAT) or Cobalt Strike Beacon to build a link with a Mustang Panda-managed server.
In December 2023, Lab52 uncovered a Mustang Panda marketing campaign concentrating on Taiwanese political, diplomatic, and governmental entities with DOPLUGS, but with a notable big difference.
“The destructive DLL is composed in the Nim programming language,” Lab52 said. “This new variant uses its personal implementation of the RC4 algorithm to decrypt PlugX, compared with previous variations that use the Windows Cryptsp.dll library.”
DOPLUGS, initially documented by Secureworks in September 2022, is a downloader with four backdoor instructions, 1 of which is orchestrated to obtain the normal type of the PlugX malware.

Craze Micro reported it also recognized DOPLUGS samples built-in with a module recognized as KillSomeOne, a plugin which is dependable for malware distribution, info collection, and document theft via USB drives.
This variant will come equipped with an added launcher component that executes the genuine executable to execute DLL-sideloading, in addition to supporting operation to operate instructions and down load the future-phase malware from an actor-controlled server.
It really is worthy of noting that a tailored PlugX variant, like the KillSomeOne module built for spreading by means of USB, was uncovered as early as January 2020 by Avira as aspect of assaults directed versus Hong Kong and Vietnam.
“This reveals that Earth Preta has been refining its equipment for some time now, continually introducing new functionalities and capabilities,” the researchers mentioned. “The team stays remarkably active, specially in Europe and Asia.”
Uncovered this posting interesting? Adhere to us on Twitter and LinkedIn to browse additional unique articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 6 Ways to Simplify SaaS Identity Governance
6 Ways to Simplify SaaS Identity Governance