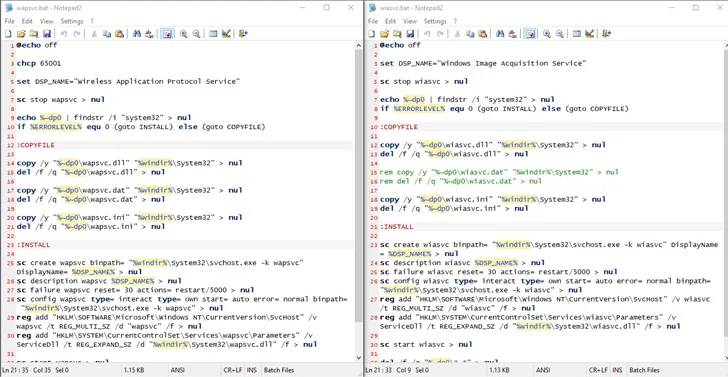
An installer for a software probable employed by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been backdoored to supply a remote entry trojan known as Konni RAT (aka UpDog).
The results occur from German cybersecurity enterprise DCSO, which connected the action as originating from the Democratic People’s Republic of Korea (DPRK)-nexus actors focusing on Russia.
The Konni (aka Opal Sleet, Osmium, or TA406) action cluster has an proven pattern of deploying Konni RAT towards Russian entities, with the risk actor also connected to assaults directed against MID at least due to the fact Oct 2021.
In November 2023, Fortinet FortiGuard Labs exposed the use of Russian-language Microsoft Phrase files to deliver malware able of harvesting sensitive details from compromised Windows hosts.

DCSO said the packaging of Konni RAT in just software installers is a procedure formerly adopted by the team in Oct 2023, when it was identified to leverage a backdoored Russian tax filing computer software named Spravki BK to distribute the trojan.
“In this occasion, the backdoored installer seems to be for a device named ‘Statistika KZU’ (Cтатистика КЗУ),” the Berlin-centered business stated.
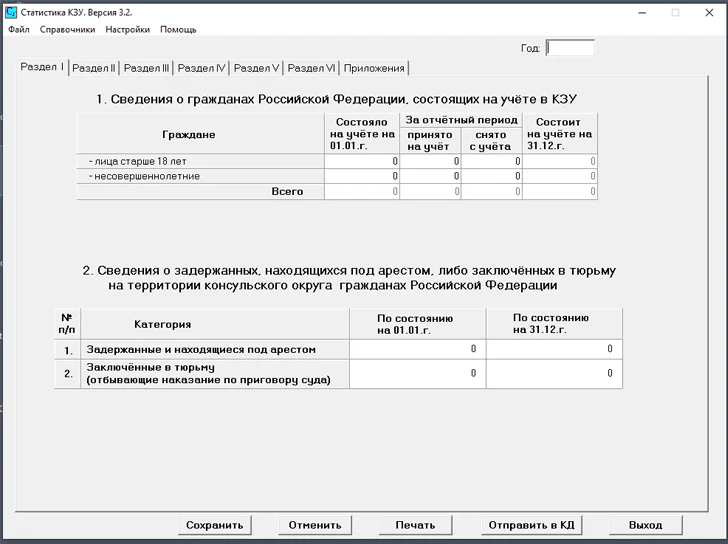
“On the basis of install paths, file metadata, and user manuals bundled into the installer, […] the software program is intended for inner use in the Russian Ministry of Foreign Affairs (MID), exclusively for the relaying of yearly report information from overseas consular posts (КЗУ — консульские загранучреждения) to the Consular Department of the MID by means of a protected channel.”
The trojanized installer is an MSI file that, when launched, initiates the infection sequence to establish get in touch with with a command-and-manage (C2) server to await more instructions.
The remote obtain trojan, which comes with capabilities for file transfers and command execution, is thought to have been set to use as early as 2014, and has also been used by other North Korean risk actors regarded as Kimsuky and ScarCruft (aka APT37).
It can be at present not crystal clear how the risk actors managed to receive the installer, given that it is not publicly available. But it truly is suspected that the long record of espionage functions targeting Russia might have served them detect possible applications for subsequent assaults.

Though North Korea’s targeting of Russia is not new, the improvement will come amid rising geopolitical proximity amongst the two nations around the world. Condition media from the Hermit Kingdom noted this week that Russian President Vladimir Putin has presented leader Kim Jong Un a luxury Russian-produced car or truck.
“To some extent, this must not arrive as a shock increasing strategic proximity would not be predicted to absolutely overwrite extant DPRK collection wants, with an ongoing have to have on the aspect of the DPRK to be ready to evaluate and verify Russian international policy planning and goals,” DCSO claimed.
Located this write-up interesting? Comply with us on Twitter and LinkedIn to study far more special content we post.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders