Menace actors running beneath the identify Nameless Arabic have introduced a distant entry trojan (RAT) termed Silver RAT that’s outfitted to bypass security software package and stealthily start hidden apps.
“The developers function on various hacker message boards and social media platforms, showcasing an active and sophisticated existence,” cybersecurity business Cyfirma reported in a report posted very last week.
The actors, assessed to be of Syrian origin and connected to the improvement of an additional RAT known as S500 RAT, also run a Telegram channel presenting numerous products and services this sort of as the distribution of cracked RATs, leaked databases, carding actions, and the sale of Fb and X (formerly Twitter) bots.

The social media bots are then used by other cyber criminals to encourage several illicit companies by quickly partaking with and commenting on user content material.
In-the-wild detections of Silver RAT v1. have been to start with observed in November 2023, even though the risk actor’s plans to launch the trojan had been initial produced official a calendar year prior to. It was cracked and leaked on Telegram all-around October 2023.
The C#-dependent malware offers of a wide vary of attributes to connect to a command-and-control (C2) server, log keystrokes, wipe out procedure restore details, and even encrypt details making use of ransomware. There are also indications that an Android edition is in the performs.
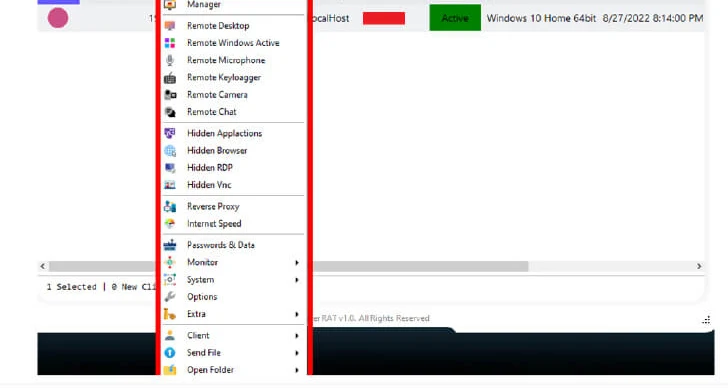
“Even though generating a payload applying Silver RAT’s builder, risk actors can pick numerous possibilities with a payload sizing up to a highest of 50kb,” the business famous. “When linked, the victim appears on the attacker-controlled Silver RAT panel, which displays the logs from the target dependent on the functionalities picked out.”
An appealing evasion aspect built into Silver RAT is its ability to hold off the execution of the payload by a distinct time as effectively as covertly start apps and just take manage of the compromised host.

Additional assessment of the malware author’s online footprint exhibits that one particular of the members of the team is probably in their mid-20s and centered in Damascus.
“The developer […] seems supportive of Palestine based mostly on their Telegram posts, and associates related with this group are lively throughout different arenas, which include social media, advancement platforms, underground discussion boards, and Clearnet web-sites, suggesting their involvement in distributing many malware,” Cyfirma claimed.
Uncovered this report exciting? Abide by us on Twitter and LinkedIn to read much more distinctive articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Unifying Security Tech Beyond the Stack: Integrating SecOps with Managed Risk and Strategy
Unifying Security Tech Beyond the Stack: Integrating SecOps with Managed Risk and Strategy