Risk actors are resorting to YouTube movies showcasing material linked to cracked software program in buy to entice end users into downloading an details stealer malware identified as Lumma.
“These YouTube films generally element content related to cracked apps, presenting users with equivalent installation guides and incorporating destructive URLs often shortened making use of services like TinyURL and Cuttly,” Fortinet FortiGuard Labs researcher Cara Lin stated in a Monday investigation.
This is not the initial time pirated software program movies on YouTube have emerged as an effective bait for stealer malware. Earlier related attack chains were observed providing stealers, clippers, and crypto miner malware.

In undertaking so, threat actors can leverage the compromised equipment for not only data and cryptocurrency theft, but also abuse the methods for illicit mining.
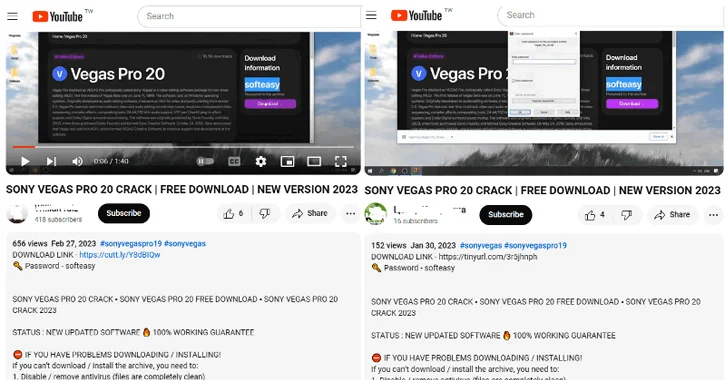
In the hottest attack sequence documented by Fortinet, consumers exploring for cracked versions of legitimate online video modifying instruments like Vegas Pro on YouTube are prompted to click on a backlink positioned in the video’s description, main to the download of a bogus installer hosted on MediaFire.

The ZIP installer, once unpacked, capabilities a Windows shortcut (LNK) masquerading as a setup file that downloads a .NET loader from a GitHub repository, which, in convert, masses the stealer payload, but not prior to doing a collection of anti-digital device and anti-debugging checks.
Lumma Stealer, composed in C and offered for sale on underground community forums because late 2022, is capable of harvesting and exfiltrating delicate knowledge to an actor-managed server.
The progress arrives as Bitdefender warned of stream-jacking attacks on YouTube in which cybercriminals consider about superior-profile accounts through phishing attacks that deploy the RedLine Stealer malware to siphon their credentials and session cookies, and in the end endorse many crypto ripoffs.

It also follows the discovery of an 11-month-old AsyncRAT campaign that employs phishing lures to download an obfuscated JavaScript file that’s then used to fall the distant entry trojan.
“The victims and their organizations are meticulously picked to broaden the influence of the marketing campaign,” AT&T Alien Labs researcher Fernando Martinez claimed. “Some of the recognized targets regulate key infrastructure in the U.S.”
Identified this short article appealing? Observe us on Twitter and LinkedIn to go through far more special written content we post.
Some parts of this article are sourced from:
thehackernews.com

 Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals
Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals