Cybersecurity is an infinite journey in a electronic landscape that under no circumstances ceases to alter. According to Ponemon Institute1, “only 59% of companies say their cybersecurity method has improved more than the past two several years.” This stagnation in tactic adaptation can be traced again to several critical issues.
- Talent Retention Issues: The cybersecurity field is fast advancing, requiring a proficient and experienced workforce. Nonetheless, corporations face a critical lack of this sort of expertise, making it tough to keep strategies agile and related.
- Leadership Concentration: Often, the notice of management teams is divided throughout many priorities, and cybersecurity may not be at the forefront. This can result in techniques turning into outdated and significantly less powerful.
- Board Engagement: Ample board guidance is critical for approach evolution. A deficiency of complete comprehension of cybersecurity issues at the board level can lead to inadequate resources and aid for strategic updates.
- Organizational Silos: When cybersecurity is treated as a different entity, alternatively than an integral component of overall business enterprise method, which it normally is, it generates silos. This technique hinders the progress of cohesive and adaptable cybersecurity techniques.
This tendency to function cybersecurity as a siloed operate is owing to its specialized character and the rapid tempo of technological and danger evolution. What is actually a lot more, every single part – managed SOC, managed risk, and managed method – commonly functions independently owing to their special skills and operational focus:
- Managed SOC: Focuses on speedy risk detection and reaction, and is ordinarily segregated from broader strategic and risk administration discussions.
- Managed Risk: Bargains with threat evaluation and mitigation it is really proactive and analytical mother nature can isolate it from the day-to-day functions of the SOC.
- Managed System: Focuses on very long-phrase arranging and alignment with business goals, but may possibly not intersect immediately with the day-to-day operational or risk assessment elements.
To tackle these challenges, it really is crucial for organizations to adopt a far more built-in solution. Breaking down the silos among managed SOC, risk management, and strategic preparing is important to making certain that cybersecurity procedures are dynamic and responsive to the ever-altering digital landscape.
Why the Latest State of Cybersecurity Requires a Unified Tactic
When SecOps, risk management, and cybersecurity system are not in sync, your organization’s protection procedure is left vulnerable. This deficiency of cohesion heightens the risk of cyberattacks and exacerbates your organization’s vulnerabilities in an previously risky electronic ecosystem.
This misalignment often commences with disjointed instruments and processes, wherever an unintegrated technology stack results in gaps in menace detection and response. In accordance to Ponemon Institute2, security teams in are utilizing on normal 45 tools to handle their security posture, making it increasingly challenging to maintain up with alerts and possible threats.
Beyond a disparate tech stack, misalignment issues frequently extend to the strategic level. When your cybersecurity technique is not in line with your broader business enterprise goals or risk appetite, friction will exist. For case in point, an extremely careful risk management strategy stifles company growth by imposing excessive security steps that prevent innovation. Conversely, a risk appetite that’s also reduced can also prohibit your business’ capacity to increase and evolve. Thinking of this, it is really necessary to strike a harmony wherever your cybersecurity method safeguards your operations without impeding the probable for progress and innovation.
Similarly, when thinking of the pitfalls involved with a disjointed cybersecurity strategy, the relevance of preparedness for inescapable breaches is heightened. Though your business may perhaps employ sturdy cybersecurity prevention methods, the absence of a in depth reaction plan leaves a sizeable vulnerability. This absence of cohesion often benefits in delayed reactions to cyber incidents, therefore exacerbating their effect and disruption.
In addition, a disjointed technique increases the risk of cyberattacks and qualified prospects to misallocation of sources, typically diverting awareness away from critical vulnerabilities. This inefficiency in taking care of cybersecurity sources can significantly gradual down response periods, compounding the potential operational, economic, and reputational hurt from cyber incidents.
The results from IBM’s Charge of a Facts Breach report highlight this:
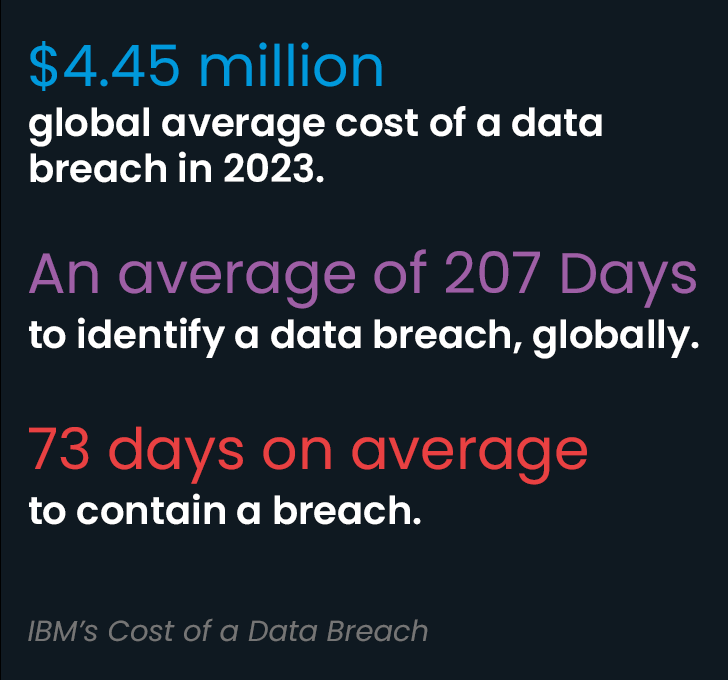
- The world typical price of a details breach in 2023 was $4.45 million.
- It usually takes an average of 207 days to establish a facts breach, globally.
- The normal time to contain a breach was 73 days.
- Breaches with identification and containment moments less than 200 times cost businesses $3.93 million. Those people above 200 days price $4.95 million—a difference of 23%.
To successfully mitigate these hazards, it is essential to combine sturdy preventative steps with a sturdy and effectively-coordinated reaction approach, ensuring a cohesive defense against cyber threats.
Eventually, strengthening your organization’s defense against these threats involves aligning your SecOps, risk administration, and cybersecurity technique. This alignment makes certain a protection technique that is resilient, responsive, and effectively personalized to address a wide spectrum of cyber threats. Obtaining this harmony is vital for a sturdy cybersecurity posture, safeguarding your firm in the present day digital planet.
Address Cyber Threats with 1 Ecosystem
To tackle these troubles effectively, it is essential to move further than a standard technology-centric view and embrace a holistic cybersecurity tactic. This paradigm shift is pivotal, emphasizing that the true energy of your organization’s cybersecurity framework is not just in the technologies employed, but in their seamless integration with managed risk, managed approach, and strong SecOps.

The essence of Manage Risk lies in its proactive nature—it’s not just about reacting to threats as they take place, but actively managing prospective vulnerabilities and exposures to reduce incidents ahead of they materialize. It encompasses a broad variety of routines aimed at understanding and making ready for the landscape of doable challenges. This includes implementing security awareness training and phishing simulations to deal with human threats, as properly as partaking in advanced phishing remediation techniques. On the complex aspect, managed risk entails conducting complete vulnerability assessments and penetration exams, alongside breach and attack simulations. Eventually, the insights gleaned from Managed Risk are employed to inform the enhancement of your cybersecurity tactic.
Managed System is about balancing pitfalls with organization expansion. This involves establishing a complete plan in collaboration with seasoned cybersecurity experts, like a vCISO, that outlines how your business will deal with cybersecurity threats, compliance gaps, and enterprise risks, now and in the future. This involves setting distinct targets, determining source allocation, and creating and tests insurance policies and treatments. A managed strategy guarantees that each individual part of your organization’s cybersecurity endeavours are intentional, coordinated, and aligned with the total organization plans.
A managed Security Functions Center is at the heart of this ecosystem. It capabilities as the operational nerve centre, where true-time checking, assessment, and reaction to cyber threats take place. By integrating managed risk and technique into the SOC, your firm assures that the insights gained from risk administration notify the strategic preparing and operational responses. This integration permits a extra agile, responsive, and successful cybersecurity posture.
By weaving collectively these elements—managed risk, managed approach, and a managed SOC—into a solitary, cohesive ecosystem, organizations are superior outfitted to foresee, prepare for, and adeptly reply to the various and at any time-evolving assortment of cyber threats. This technique to cybersecurity system management is not just a strategic edge but a fundamental necessity for guaranteeing a safe and fortified digital presence in present-day cyber landscape.
See how your organization compares from sector standards. Asses your security posture with our Cybersecurity Checklist. Obtain now.
6 Advantages of Unifying SecOps, Risk Administration, and Managed Tactic
1. Expense-Efficient Useful resource Allocation
The integration of SOC administration, risk administration, and managed technique prospects to strategic allocation of both human and technology assets in cybersecurity. This approach lowers redundancies, making certain efficient use of investments in staff and security infrastructure. On the human side, this consolidation fosters better interior staff coordination and communication, aligning anyone in direction of widespread cybersecurity ambitions and maximizing all round efficiency, even though also augmenting your staff with hugely-specialised assets, enabling your group to aim on a lot more strategic initiatives.
From a technological standpoint, unifying your cybersecurity program factors assists avert the overlapping of equipment and units, minimizing complexity and associated charges. Improved menace detection and response abilities from this streamlined approach also appreciably restrict financial impacts from cyber incidents. IBM’s report underscores this, noting that corporations with reduced security program complexity faced an average details breach charge of $3.84 million in 2023, as opposed to $5.28 million for these with much more complicated methods, marking a sizeable raise of 31.6%. This info highlights the expense-performance of a unified cybersecurity method.
2. Educated Choice-Producing
At the core of an built-in cybersecurity tactic lies the basic principle of info-driven determination-earning. Nonetheless, now, corporations often offer with cybersecurity assessments that deficiency a robust foundation in info evaluation. This disconnect in between facts and decision-earning drives the have to have for integration. By seamlessly merging each individual part of your cybersecurity plan into a person ecosystem, conclusions become grounded in complete info evaluation, enabling you to quantify challenges in terms of money and operational affect and empowering you to make educated choices making use of metrics to figure out the real company influence.
3. Swift Incident Response
The pace of reaction to security incidents is very important, but since a lot of organizations have a disjointed technique in spot, delayed responses and improved vulnerabilities are inevitable. This disconnection normally benefits in ineffective notify triage, a proliferation of replicate alerts, and a lack of prioritization – all of which exacerbate the operational, financial, and reputational effect of cyber incidents.
The solution lies in an integrated cybersecurity technique that aligns SecOps with risk administration, streamlining the reaction process for extra powerful notify triage, minimizing replicate alerts, and applying a risk-based solution to prioritizing alerts. Such an built-in strategy allows swift and effective responses, considerably decreasing the affect of cyber incidents and safeguarding organizational property and status, in the long run guaranteeing organization continuity and strengthening stakeholder have confidence in in an more and more dynamic digital setting.
4. Improved, Proactive Risk Detection
A unified, risk-dependent method to risk detection entails a transformative change from regular siloed methods to a cohesive method. Usually, disjointed security operations and risk administration led to fragmented risk detection and reactive responses to security threats. The integration of these functions functions as a unifying pressure, bringing previously disconnected info sources and threat intelligence underneath a single dashboard.
This allows for the correlation of knowledge that was once isolated, giving corporations with a detailed 360-degree look at of the menace landscape. On top of that, sophisticated systems like AI and equipment understanding improve this tactic by examining data, identifying designs, and boosting predictive abilities. The consequence is a strengthened cybersecurity posture with improved risk detection and mitigation, actively cutting down pitfalls and safeguarding organizational belongings and popularity in a dynamic digital landscape.
5. Streamlined Compliance Management
Corporations face the substantial obstacle of maintaining up with sophisticated regulatory compliance needs. Ordinarily, fragmented methods in SecOps management, risk, and tactic have led to cumbersome compliance procedures and improved pitfalls of non-compliance, along with prospective legal and economical penalties. A more successful remedy is observed in adopting an built-in cybersecurity solution. By aligning SecOps with risk administration and incorporating specialist direction via managed strategy, organizations can navigate the compliance landscape far more correctly.
This unified technique streamlines compliance through enhanced reporting, enhanced information correlation, and centralized log storage. It also lets for adapting quickly to modifying guidelines and benchmarks beneath the guidance of seasoned professionals. As a outcome, businesses not only simplify their compliance processes but also significantly minimize the risk of lawful and money repercussions, making certain operational continuity and keeping their reputation in a complex regulatory setting.
6. Continuous Progress
In the field of cybersecurity, stagnation equates to vulnerability. Nevertheless, corporations usually struggle to continue to keep up with the amount of transform and find by themselves facing the daunting reality that failing to progress indicates getting more susceptible to threats. The key to beating this lies in adopting a holistic system that encompasses SecOps administration, risk management, and a strong cybersecurity framework.
This solution, blending skilled staff, successful processes, and superior technology, is important for correctly countering threats and facilitating development. By embracing this route of ongoing improvement and adaptation, businesses can create more powerful resilience from the dynamic mother nature of cyber threats, positioning by themselves to confidently navigate foreseeable future challenges and attain lasting enterprise good results.
Adapt and Develop a Resilient Cybersecurity Method
According to Gartner, “The only way to offer correctly with the evolving dangers of digitalization and raising cyber threats is to institute a continual security system.” Applying a total cybersecurity software is a journey that requires many strategic actions and crucial staff. By next a thorough roadmap, businesses can systematically integrate their SecOps, risk management, and cybersecurity techniques, thereby constructing a resilient, adaptive cybersecurity posture.
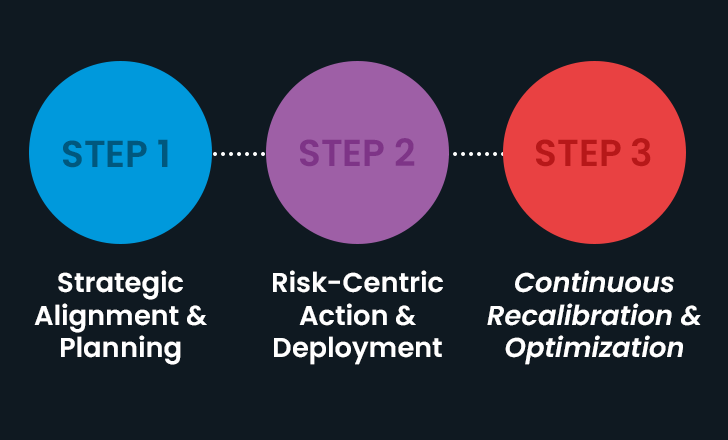
3 Techniques to Develop Your Cybersecurity System
1. Strategic Alignment and Setting up
- Build obvious cybersecurity aims aligned with business enterprise goals.
- Combine security controls into the organizational approach.
- Assist all small business facets with strong security actions.
- Generate a risk prioritization framework to establish critical threats.
- Develop a tailor-made security architecture centered on organization needs and risk profile.
2. Risk-Centric Action and Deployment
- Layout an economical group framework for cybersecurity technique implementation.
- Deploy essential applications and technologies for plan execution.
- Translate strategic plans into actionable measures.
- Allocate assets strategically to substantial-risk spots.
- Ensure steady monitoring and management of security programs.
3. Steady Recalibration and Optimization
- Manage accountability throughout all organizational concentrations.
- Boost incident response capabilities for swift risk reaction.
- Foster a cybersecurity-knowledgeable tradition and teach personnel and stakeholders.
- On a regular basis assess and connect the program’s effectiveness to critical stakeholders.
- Regulate and refine procedures based on ongoing assessments.
- Align cybersecurity measures with evolving enterprise environments and risk landscapes.
Start off the system of recalibrating your security application. Validate your present cybersecurity controls with a Complimentary Security Workshop. Request a Workshop now.
Foreseeable future Developments in Cybersecurity
As we appear in direction of the long run, the landscape of cybersecurity is established to be shaped by emerging technologies like AI, machine mastering, quantum computing, and the Internet of Issues (IoT). These technological progress, especially the refined abilities of AI and equipment understanding, bring both new options and difficulties in cybersecurity. They underscore the critical need for an built-in cybersecurity strategy that is adaptive and forward-seeking. This system need to not only handle existing security problems but also be agile plenty of to foresee and react to the advanced threats that appear with these state-of-the-art technologies. Embracing an built-in strategy is not just a necessity for currently but a essential imperative for the long term, crucial for navigating the evolving threats and harnessing the comprehensive likely of the electronic age.
The integration of SOC management, risk management, and managed cybersecurity technique is not just effective it is a critical need for modern day companies. This convergence paves the way for a resilient, cost-effective, and long run-evidence cybersecurity posture, equipping businesses like yours to efficiently confront both equally present and foreseeable future cybersecurity problems.
For much more data about going over and above your common tech stack, take a look at ArmorPoint’s alternatives and experience the power of a unified strategy to cybersecurity system management.
References:
1 Ponemon Institute. (2022). The Point out of Cybersecurity and 3rd-Bash Distant Accessibility Risk.
2Ponemon Institute. (2020). 2020 Cyber Resilient Business Research.
Observed this article interesting? Observe us on Twitter and LinkedIn to study extra special written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Webinar – Leverage Zero Trust Security to Minimize Your Attack Surface
Webinar – Leverage Zero Trust Security to Minimize Your Attack Surface