An ongoing cyber attack campaign has established its sights on Korean-talking people today by using U.S. Armed forces-themed document lures to trick them into operating malware on compromised systems.
Cybersecurity agency Securonix is monitoring the action less than the identify STARK#MULE.
“Primarily based on the source and probable targets, these kinds of attacks are on par with past attacks stemming from common North Korean teams these as APT37 as South Korea has traditionally been a major focus on of the team, primarily its authorities officers,” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov claimed in a report shared with The Hacker News.
APT37, also regarded by the names Nickel Foxcroft, Reaper, Ricochet Chollima, and ScarCruft, is a North Korean country-state actor that is recognized to exclusively concentration on targets in its southern counterpart, precisely those associated in reporting on North Korea and supporting defectors.
Attack chains mounted by the team have traditionally relied on social engineering to phish victims and produce payloads these types of as RokRat on to goal networks. That claimed, the adversarial collective has expanded its offensive arsenal with a assortment of malware households in latest months, like a Go-dependent backdoor known as AblyGo.
A noteworthy trait of the new marketing campaign is the use of compromised Korean e-commerce sites for staging payloads and command-and-management (C2) in an endeavor to fly underneath the radar of security methods installed on the devices.
The phishing e-mails that act as the progenitor make use of U.S. Military recruitment messages to persuade recipients into opening a ZIP archive file, which consists of a shortcut file that seems beneath the guise of a PDF document.
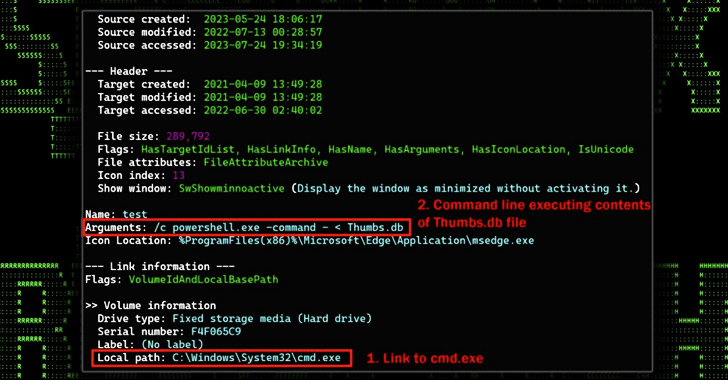
The shortcut file, when introduced, shows a decoy PDF, but also surreptitiously activates the execution of a rogue “Thumbs.db” file present in the archive file.
“This file performs a number of features which include things like downloading further stagers and leveraging schtasks.exe to establish persistence,” the researchers stated.
Two of the subsequent-stage modules – “lsasetup.tmp” and “winrar.exe” – are retrieved from a compromised e-commerce web page named “www.jkmusic.co[.]kr,” the latter of which is used to extract and run the contents of “lsasetup.tmp,” an obfuscated binary that attained out to a second e-commerce site named “www.notebooksell[.]kr.”
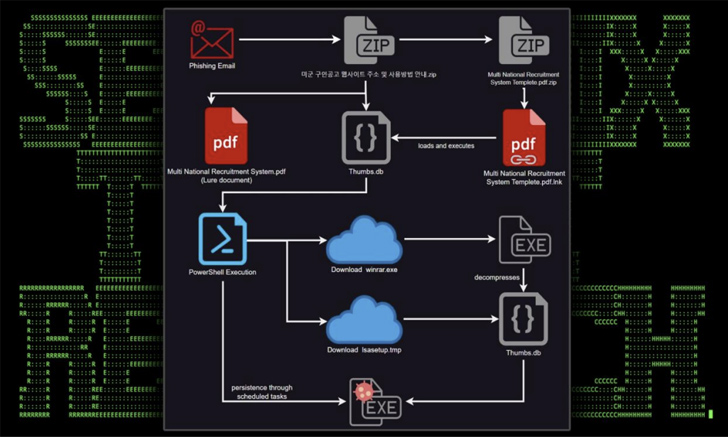
“When the relationship was proven, the attackers were being able to purchase process information this kind of as method MAC, Windows model, [and] IP address,” the researchers explained. “The two web-sites are registered in Korea [and] only use the HTTP protocol.”
The disclosure arrives as APT37 has also been noticed generating use of CHM data files in phishing emails impersonating security emails from economic institutes and insurance coverage corporations to deploy data-thieving malware and other binaries, according to the AhnLab Security Crisis Reaction Center (ASEC).
“In individual, malware that targets specific users in Korea may possibly incorporate content on subjects of desire to the consumer to persuade them to execute the malware, so customers must refrain from opening e-mails from not known resources and should not execute their attachments,” ASEC claimed.
Impending WEBINARShield Versus Insider Threats: Grasp SaaS Security Posture Administration
Worried about insider threats? We’ve acquired you coated! Join this webinar to discover realistic methods and the secrets and techniques of proactive security with SaaS Security Posture Administration.
Be part of Currently
APT37 is one particular of the quite a few North Korean condition-sponsored teams that have drawn interest for executing assaults that are intended to perpetrate fiscal theft – like the latest assaults on Alphapo and CoinsPaid – and acquire intelligence in pursuit of the regime’s political and national security aims.
This also contains the infamous Lazarus Team and its sub-clusters Andariel and BlueNoroff, with the actors leveraging a new backdoor dubbed ScoutEngine and a completely rewritten variation of a malware framework termed MATA (MATAv5) in intrusions aimed at defense contractors in Eastern Europe in September 2022.
“This advanced malware, completely rewritten from scratch, reveals an highly developed and sophisticated architecture that can make use of loadable and embedded modules and plugins,” Kaspersky reported in its APT tendencies report for Q2 2023.
“The malware leverages Inter-Procedure Communication (IPC) channels internally and employs a assorted vary of commands, enabling it to create proxy chains across various protocols, together with within just the victim’s setting.”
Found this article fascinating? Comply with us on Twitter and LinkedIn to browse a lot more distinctive material we put up.
Some parts of this article are sourced from:
thehackernews.com

 A Data Exfiltration Attack Scenario: The Porsche Experience
A Data Exfiltration Attack Scenario: The Porsche Experience