A legitimate Windows lookup function could be exploited by destructive actors to download arbitrary payloads from distant servers and compromise focused systems with distant access trojans these types of as AsyncRAT and Remcos RAT.
The novel attack technique, per Trellix, normally takes edge of the “look for-ms:” URI protocol handler, which features the ability for programs and HTML links to launch customized nearby queries on a machine, and the “look for:” application protocol, a system for contacting the desktop research software on Windows.
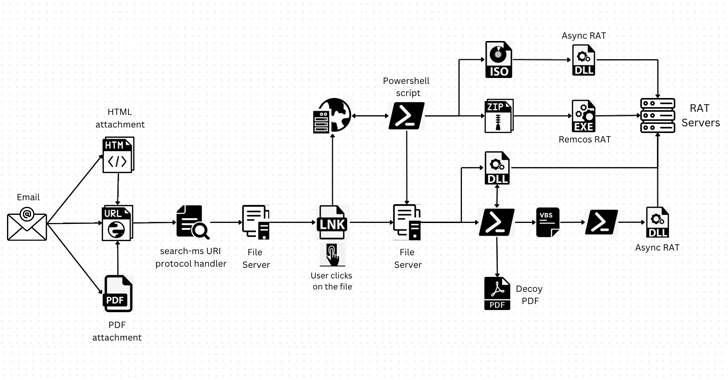
“Attackers are directing customers to web-sites that exploit the ‘search-ms’ operation employing JavaScript hosted on the site,” security scientists Mathanraj Thangaraju and Sijo Jacob reported in a Thursday write-up. “This system has even been extended to HTML attachments, increasing the attack area.”
In this kind of attacks, threat actors have been noticed building misleading e-mails that embed hyperlinks or HTML attachments made up of a URL that redirects people to compromised web sites. This triggers the execution of JavaScript that makes use of the URI protocol handlers to carry out searches on an attacker-controlled server.
It is worthy of noting that clicking on the backlink also generates a warning “Open up Windows Explorer?,” approving which “the research outcomes of remotely hosted destructive shortcut information are displayed in Windows Explorer disguised as PDFs or other trustworthy icons, just like local lookup benefits,” the scientists spelled out.
“This wise strategy conceals the fact that the consumer is staying delivered with distant files and gives the user the illusion of trust. As a result, the user is additional possible to open the file, assuming it is from their personal method, and unknowingly execute malicious code.”
Need to a target click on on one of the shortcut data files, it qualified prospects to the execution of a rogue dynamic-url library (DLL) utilizing the regsvr32.exe utility.
In an substitute variant of the marketing campaign, the shortcut documents are used to operate PowerShell scripts, which, in turn, download additional payloads in the history, whilst exhibiting a decoy PDF document to deceive victims.
Irrespective of the strategy utilised, the infections direct to the installation of AsyncRAT and Remcos RAT that can be employed by the risk actors to remotely commandeer the hosts, steal delicate facts, and even offer the accessibility to other attackers.
Future WEBINARShield Towards Insider Threats: Master SaaS Security Posture Administration
Fearful about insider threats? We have obtained you coated! Be a part of this webinar to investigate practical approaches and the strategies of proactive security with SaaS Security Posture Management.
Be a part of Right now
With Microsoft steadily using methods to clamp down on many first entry vectors, it truly is anticipated that adversaries could latch on to the URI protocol handler approach to evade standard security defenses and distribute malware.
“It is crucial to refrain from clicking on suspicious URLs or downloading documents from mysterious resources, as these steps can expose devices to malicious payloads shipped through the ‘search”https://thehackernews.com/”lookup-ms’ URI protocol handler,” the researchers said.
Discovered this article attention-grabbing? Comply with us on Twitter and LinkedIn to read much more exclusive articles we publish.
Some parts of this article are sourced from:
thehackernews.com

 BlueBravo Deploys GraphicalProton Backdoor Against European Diplomatic Entities
BlueBravo Deploys GraphicalProton Backdoor Against European Diplomatic Entities