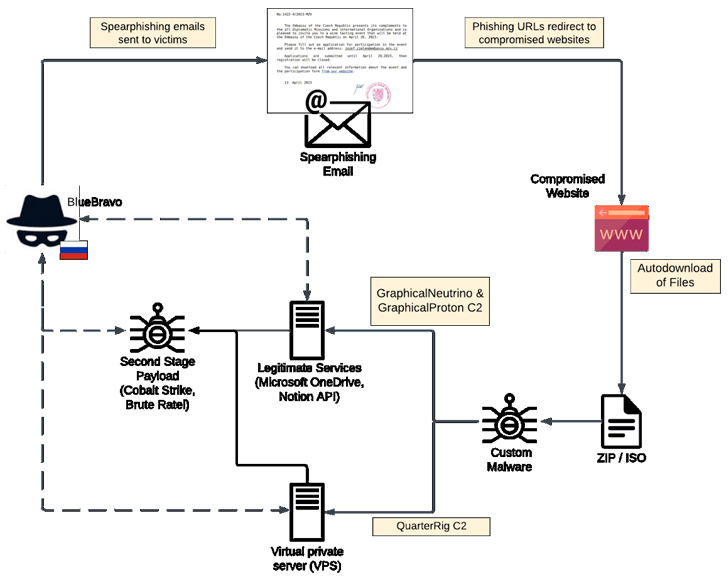
The Russian country-condition actor identified as BlueBravo has been observed focusing on diplomatic entities during Jap Europe with the aim of providing a new backdoor named GraphicalProton, exemplifying the continual evolution of the danger.
The phishing marketing campaign is characterised by the use of genuine internet expert services (LIS) for command-and-management (C2) obfuscation, Recorded Long term claimed in a new report posted Thursday. The activity was observed in between March and May 2023.
BlueBravo, also known by the names APT29, Cloaked Ursa, and Midnight Blizzard (formerly Nobelium), is attributed to Russia’s Foreign Intelligence Assistance (SVR), and has in the earlier used Dropbox, Firebase, Google Push, Notion, and Trello to evade detection and stealthily set up communications with infected hosts.
To that conclude, GraphicalProton is the most current addition to a long checklist of malware targeting diplomatic corporations after GraphicalNeutrino (aka SNOWYAMBER), HALFRIG, and QUARTERRIG.
“Unlike GraphicalNeutrino, which utilised Notion for C2, GraphicalProton uses Microsoft’s OneDrive or Dropbox for communication,” the cybersecurity agency mentioned.
This marks an attempt on the part of BlueBravo operators to not only diversify their tooling but also extend the portfolio of companies misused for concentrating on companies that are of strategic desire to the nation.
“BlueBravo seems to prioritize cyber espionage initiatives against European governing administration sector entities, probably owing to the Russian government’s desire in strategic information all through and after the war in Ukraine.”
The new malware pressure, like GraphicalNeutrino, features as a loader and is staged inside an ISO or ZIP file delivered by using a phishing email bearing automobile-themed lures, overlapping with an intrusion established reported by Palo Alto Networks Device 42 before this month.
Approaching WEBINARShield In opposition to Insider Threats: Master SaaS Security Posture Management
Fearful about insider threats? We’ve acquired you lined! Be a part of this webinar to check out useful approaches and the secrets of proactive security with SaaS Security Posture Administration.
Be a part of Today
The ISO documents consist of .LNK files that masquerade as .PNG pictures of a BMW car or truck that’s purportedly for sale, which, when clicked, sales opportunities to the deployment of GraphicalProton for comply with-on exploitation. This is achieved by using Microsoft OneDrive as C2 and periodically polling a folder in the storage services to fetch extra payloads.
“It is very important for network defenders to be mindful of the risk of the misuse of these services inside their company and to realize circumstances in which they may possibly be employed in similar initiatives to exfiltrate details,” researchers mentioned.
The advancement comes as the Computer Emergency Reaction Staff of Ukraine (CERT-UA) warned of ongoing phishing assaults undertaken by a team known as UAC-0006 group, which the agency claimed is intensifying attempts to entice buyers into putting in a backdoor regarded as SmokeLoader.
Uncovered this write-up attention-grabbing? Adhere to us on Twitter and LinkedIn to read additional special articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Major Security Flaw Discovered in Metabase BI Software – Urgent Update Required
Major Security Flaw Discovered in Metabase BI Software – Urgent Update Required