Users of Metabase, a preferred organization intelligence and facts visualization software package package, are getting encouraged to update to the most up-to-date edition pursuing the discovery of an “very significant” flaw that could end result in pre-authenticated distant code execution on affected installations.
Tracked as CVE-2023-38646, the issue impacts open-supply editions prior to .46.6.1 and Metabase Enterprise variations ahead of 1.46.6.1.
“An unauthenticated attacker can run arbitrary instructions with the similar privileges as the Metabase server on the server you are working Metabase on,” Metabase explained in an advisory released very last 7 days.
The issue has also been addressed in the adhering to more mature versions –
- .45.4.1 and 1.45.4.1
- .44.7.1 and 1.44.7.1, and
- .43.7.2 and 1.43.7.2
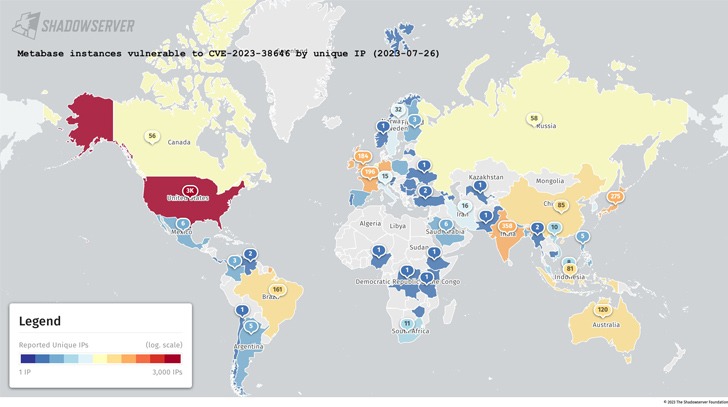
Whilst there is no evidence that the issue has been exploited in the wild, facts gathered by the Shadowserver Foundation shows that 5,488 out of the full 6,936 Metabase scenarios are vulnerable as of July 26, 2023. A bulk of the circumstances are located in the U.S., India, Germany, France, the U.K., Brazil, and Australia.
Forthcoming WEBINARShield Versus Insider Threats: Grasp SaaS Security Posture Management
Worried about insider threats? We’ve got you lined! Sign up for this webinar to explore simple procedures and the insider secrets of proactive security with SaaS Security Posture Management.
Be part of These days
Assetnote, which claimed it discovered and claimed the bug to Metabase, said the vulnerability is because of to a JDBC connection issue in the API endpoint “/api/set up/validate,” enabling a malicious actor to obtain a reverse shell on the system by signifies of a specifically crafted ask for that requires advantage of an SQL injection flaw in the H2 database driver.
Buyers who are unable to utilize the patches immediately are advisable to block requests to the /api/setup endpoint, isolate the Metabase instance from your output network, and observe for suspicious requests to the endpoint in query.
Found this post interesting? Abide by us on Twitter and LinkedIn to go through more distinctive written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Cybersecurity Agencies Warn Against IDOR Bugs Exploited for Data Breaches
Cybersecurity Agencies Warn Against IDOR Bugs Exploited for Data Breaches