The threat actors joined to the malware loader identified as IcedID have produced updates to the BackConnect (BC) module that is utilized for publish-compromise action on hacked programs, new findings from Team Cymru expose.
IcedID, also identified as BokBot, is a strain of malware equivalent to Emotet and QakBot that began off as a banking trojan in 2017, before switching to the role of an original entry facilitator for other payloads. Latest variations of the malware have been observed taking away operation similar to on line banking fraud to prioritize ransomware shipping and delivery.
The BackConnect (BC) module, 1st documented by Netresec in October 2022, relies on a proprietary command-and-manage (C2) protocol to exchange instructions concerning a server and the contaminated host. The protocol, which comes with a VNC element for remote access, has also been determined in other malware this kind of as the now-discontinued BazarLoader and QakBot.
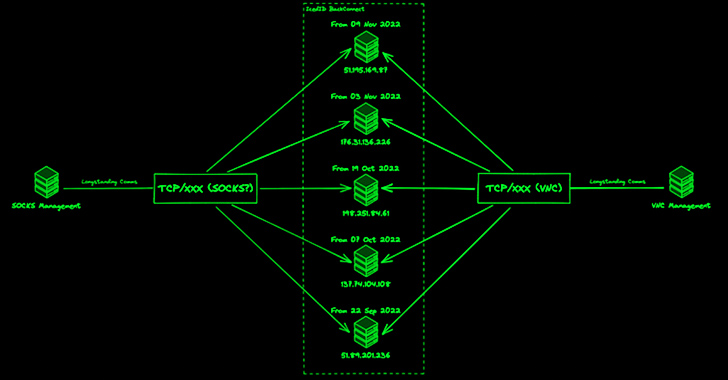
In December 2022, Staff Cymru claimed the discovery of 11 BC C2s active due to the fact July 1, 2022, noting that operators likely situated in Moldova and Ukraine are overseeing distinctive aspects of the BC protocol.
“For the previous quite a few months, BackConnect targeted traffic induced by IcedID was effortless to detect simply because it occurred in excess of TCP port 8080,” Palo Alto Networks Unit 42 mentioned in late May possibly 2023. “Nonetheless, as early as April 11, 2023, BackConnect activity for IcedID improved to TCP port 443, making it tougher to uncover.”
The newest assessment of the attack infrastructure from Team Cymru has uncovered that the amount of BC C2s have shot up from 11 to 34 because January 23, 2023, with the average uptime of a server substantially decreasing from 28 days to eight days.
“Given that 11 April 2023, a full of 20 significant self-confidence BC C2 servers ended up identified, dependent on pivots from administration infrastructure,” the cybersecurity firm mentioned in a report shared with The Hacker News.
“The first observation is that the amount of concurrent C2 servers in procedure has greater […], with as many as 4 C2 servers obtaining management communications on a distinct day.”
A more assessment of the site visitors originating from BC C2 servers has uncovered as quite a few as eight candidate victims amongst late April 2023 and June 2023 that “communicated with three or far more BC C2s in excess of a relatively extensive period of time.”
Future WEBINARShield In opposition to Insider Threats: Learn SaaS Security Posture Administration
Fearful about insider threats? We have obtained you covered! Sign up for this webinar to investigate realistic tactics and the tricks of proactive security with SaaS Security Posture Management.
Sign up for Now
It is also suspected that the similar IcedID operator or affiliate is accessing multiple victims within just the identical time body, based mostly on the volume of targeted visitors noticed involving the victims and the servers.
“In examining administration infrastructure connected with IcedID BC, we are also in a position to discern a pattern of a number of distinctive accesses from end users we evaluate to be both linked with the day to day operations of IcedID, and their affiliates who interact with target hosts put up-compromise,” Team Cymru reported.
“The evidence in our NetFlow knowledge implies that particular IcedID victims are used as proxies in spamming operations, enabled by BC’s SOCKS abilities. This is a potential double blow for victims, not only are they compromised and incurring data / fiscal loss, but they are also further exploited for the needs of spreading more IcedID campaigns.”
Discovered this write-up interesting? Comply with us on Twitter and LinkedIn to read through a lot more distinctive material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 STARK#MULE Targets Koreans with U.S. Military-themed Document Lures
STARK#MULE Targets Koreans with U.S. Military-themed Document Lures