Cloud environments go on to be at the acquiring close of an ongoing highly developed attack marketing campaign dubbed SCARLETEEL, with the threat actors now setting their sights on Amazon Web Expert services (AWS) Fargate.
“Cloud environments are even now their principal target, but the equipment and strategies utilized have adapted to bypass new security measures, alongside with a a lot more resilient and stealthy command and regulate architecture,” Sysdig security researcher Alessandro Brucato claimed in a new report shared with The Hacker News.
SCARLETEEL was very first exposed by the cybersecurity enterprise in February 2023, detailing a innovative attack chain that culminated in the theft of proprietary info from AWS infrastructure and the deployment of cryptocurrency miners to profit off the compromised systems’ methods illegally.
A abide by-up assessment by Cado Security uncovered possible links to a prolific cryptojacking group acknowledged as TeamTNT, even though Sysdig informed The Hacker Information that it “could be somebody copying their methodology and attack designs.”
The newest action continues the risk actor’s penchant for likely right after AWS accounts by exploiting vulnerable general public-going through web programs with an greatest intention to achieve persistence, steal mental house, and perhaps deliver revenue to the tune of $4,000 for every day working with crypto miners.
“The actor found out and exploited a blunder in an AWS policy which allowed them to escalate privileges to AdministratorAccess and gain command in excess of the account, enabling them to then do with it what they required,” Brucato described.
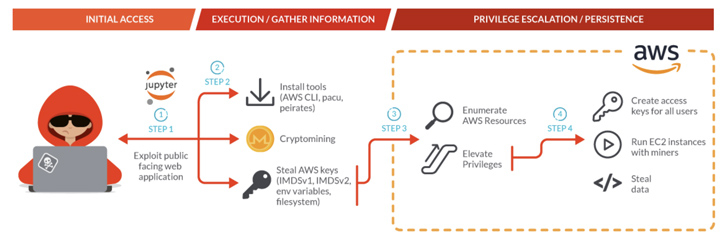
It all starts with the adversary exploiting JupyterLab notebook containers deployed in a Kubernetes cluster, leveraging the first foothold to carry out reconnaissance of the concentrate on network and get AWS credentials to get hold of further entry into the victim’s natural environment.
This is adopted by the set up of the AWS command line device and an exploitation framework named Pacu for subsequent exploitation. The attack also stands out for its use of many shell scripts to retrieve AWS qualifications, some of which concentrate on AWS Fargate compute motor cases.
“The attacker was noticed working with the AWS shopper to connect to Russian devices which are appropriate with the S3 protocol,” Brucato claimed, adding the SCARLETEEL actors utilised stealthy methods to make certain that data exfiltration functions are not captured in CloudTrail logs.
Approaching WEBINAR🔐 PAM Security – Specialist Options to Secure Your Delicate Accounts
This specialist-led webinar will equip you with the understanding and tactics you will need to change your privileged accessibility security approach.
Reserve Your Location
Some of the other methods taken by the attacker contain the use of a Kubernetes Penetration Testing resource identified as Peirates to exploit the container orchestration procedure and a DDoS botnet malware termed Pandora, indicating further attempts on the aspect of the actor to monetize the host.
“The SCARLETEEL actors continue to operate towards targets in the cloud, such as AWS and Kubernetes,” Brucato explained. “Their preferred system of entry is exploitation of open up compute solutions and vulnerable purposes. There is a continued aim on financial gain by using crypto mining, but […] intellectual property is continue to a priority.”
Uncovered this write-up intriguing? Abide by us on Twitter and LinkedIn to study a lot more unique material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Beware of Big Head Ransomware: Spreading Through Fake Windows Updates
Beware of Big Head Ransomware: Spreading Through Fake Windows Updates