A developing piece of ransomware known as Big Head is being dispersed as section of a malvertising marketing campaign that will take the type of bogus Microsoft Windows updates and Word installers.
Large Head was initial documented by Fortinet FortiGuard Labs previous month, when it identified numerous variants of the ransomware that are built to encrypt data files on victims’ devices in trade for a cryptocurrency payment.
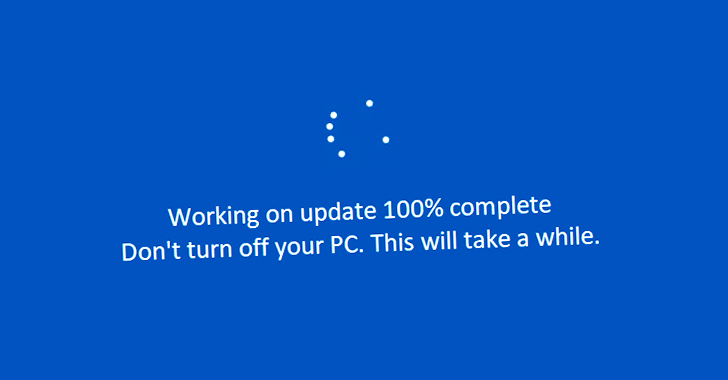
“One Significant Head ransomware variant displays a phony Windows Update, potentially indicating that the ransomware was also distributed as a pretend Windows Update,” Fortinet scientists explained at the time. “One of the variants has a Microsoft Term icon and was probably dispersed as counterfeit software.”
A the greater part of the Massive Head samples have been submitted so considerably from the U.S., Spain, France, and Turkey.
In a new examination of the .NET-based mostly ransomware, Trend Micro detailed its interior workings, contacting out its capacity to deploy a few encrypted binaries: 1.exe to propagate the malware, archive.exe to aid communications more than Telegram, and Xarch.exe to encrypt the data files and” show a fake Windows update.
“The malware shows a fake Windows Update UI to deceive the victim into contemplating that the destructive action is a legitimate software program update approach, with the share of development in increments of 100 seconds,” the cybersecurity organization claimed.
Huge Head is no unique from other ransomware people in that it deletes backups, terminates quite a few procedures, and performs checks to ascertain if it truly is functioning in just a virtualized natural environment in advance of proceeding to encrypt the documents.
In addition, the malware disables the Task Manager to avert users from terminating or investigating its process and aborts itself if the machine’s language matches that of Russian, Belarusian, Ukrainian, Kazakh, Kyrgyz, Armenian, Georgian, Tatar, and Uzbek. It also incorporates a self-delete perform to erase its existence.
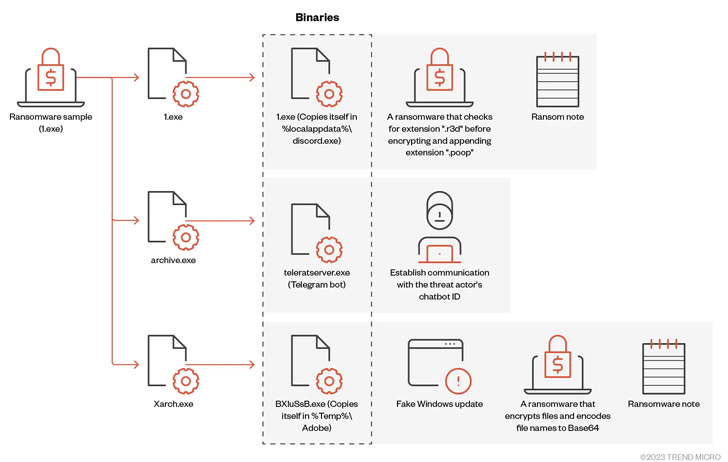
Pattern Micro stated it detected a 2nd Massive Head artifact with the two ransomware and stealer behaviors, the latter of which leverages the open up-source WorldWind Stealer to harvest web browser history, listing lists, managing procedures, solution essential, and networks.
Forthcoming WEBINAR🔐 PAM Security – Professional Solutions to Protected Your Delicate Accounts
This specialist-led webinar will equip you with the information and procedures you will need to rework your privileged accessibility security system.
Reserve Your Place
Also identified is a 3rd variant of Massive Head that incorporates a file infector identified as Neshta, which is made use of to insert destructive code into executables on the infected host.
“Incorporating Neshta into the ransomware deployment can also provide as a camouflage system for the remaining Huge Head ransomware payload,” Trend Micro researchers claimed.
“This method can make the piece of malware appear as a different type of threat, this kind of as a virus, which can divert the prioritization of security alternatives that generally target on detecting ransomware.”
The identity of the menace actor powering Big Head is now not known, but Development Micro explained it recognized a YouTube channel with the identify “aplikasi quality cuma cuma,” suggesting an adversary probably of Indonesian origin.
“Security groups must continue to be prepared offered the malware’s diverse functionalities,” the scientists concluded. “This multifaceted nature gives the malware the potential to cause considerable hurt when entirely operational, generating it much more hard to protect systems against, as every attack vector needs independent awareness.”
Observed this post intriguing? Adhere to us on Twitter and LinkedIn to read through much more exclusive articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Apple Issues Urgent Patch for Zero-Day Flaw Targeting iOS, iPadOS, macOS, and Safari
Apple Issues Urgent Patch for Zero-Day Flaw Targeting iOS, iPadOS, macOS, and Safari