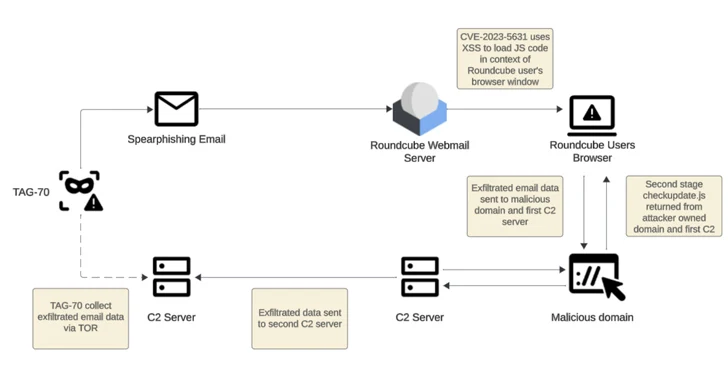
Threat actors working with pursuits aligned to Belarus and Russia have been linked to a new cyber espionage campaign that likely exploited cross-internet site scripting (XSS) vulnerabilities in Roundcube webmail servers to target in excess of 80 corporations.
These entities are principally found in Georgia, Poland, and Ukraine, in accordance to Recorded Future, which attributed the intrusion established to a danger actor acknowledged as Wintertime Vivern, which is also acknowledged as TA473 and UAC0114. The cybersecurity agency is tracking the hacking outfit underneath the moniker Menace Exercise Team 70 (TAG-70).
Wintertime Vivern’s exploitation of security flaws in Roundcube and program was beforehand highlighted by ESET in October 2023, signing up for other Russia-linked risk actor teams such as APT28, APT29, and Sandworm that are known to concentrate on email software package.

The adversary, which has been lively given that at minimum December 2020, has also been connected to the abuse of a now-patched vulnerability in Zimbra Collaboration email program previous yr to infiltrate organizations in Moldova and Tunisia in July 2023.
The marketing campaign identified by Recorded Long term took location from the start out of October 2023 and continued until finally the middle of the month with the intention of collecting intelligence on European political and military services routines. The assaults overlap with more TAG-70 activity against Uzbekistan govt mail servers that ended up detected in March 2023.
“TAG70 has shown a superior amount of sophistication in its attack procedures,” the company said. “The menace actors leveraged social engineering tactics and exploited cross-website scripting vulnerabilities in Roundcube webmail servers to acquire unauthorized entry to targeted mail servers, bypassing the defenses of federal government and navy corporations.”
The attack chains entail exploiting Roundcube flaws to deliver JavaScript payloads that are designed to exfiltrate consumer qualifications to a command-and-control (C2) server.

Recorded Upcoming reported it also uncovered evidence of TAG-70 targeting the Iranian embassies in Russia and the Netherlands, as very well as the Georgian Embassy in Sweden.
“The focusing on of Iranian embassies in Russia and the Netherlands suggests a broader geopolitical interest in assessing Iran’s diplomatic activities, particularly concerning its aid for Russia in Ukraine,” it stated.
“Similarly, espionage towards Georgian federal government entities demonstrates interests in monitoring Georgia’s aspirations for European Union (EU) and NATO accession.”
Discovered this article attention-grabbing? Stick to us on Twitter and LinkedIn to read through extra exceptional information we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Iranian Hackers Target Middle East Policy Experts with New BASICSTAR Backdoor
Iranian Hackers Target Middle East Policy Experts with New BASICSTAR Backdoor