The Iranian-origin threat actor acknowledged as Charming Kitten has been joined to a new established of attacks aimed at Middle East plan authorities with a new backdoor named BASICSTAR by producing a phony webinar portal.
Charming Kitten, also referred to as APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a historical past of orchestrating a wide array of social engineering strategies that forged a wide net in their concentrating on, often singling out think tanks, NGOs, and journalists.
“CharmingCypress frequently employs unconventional social-engineering techniques, these as partaking targets in extended discussions around email in advance of sending hyperlinks to malicious content material,” Volexity researchers Ankur Saini, Callum Roxan, Charlie Gardner, and Damien Money mentioned.
Final thirty day period, Microsoft exposed that superior-profile men and women operating on Middle Jap affairs have been focused by the adversary to deploy malware these types of as MischiefTut and MediaPl (aka EYEGLASS) that are capable of harvesting delicate information and facts from a compromised host.

The team, assessed to be affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), has also distributed various other backdoors such as PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho), and NokNok about the earlier yr, emphasizing its willpower to keep on its cyber onslaught, adapting its techniques and solutions in spite of general public exposure.
The phishing attacks noticed concerning September and Oct 2023 associated the Charming Kitten operators posing as the Rasanah Worldwide Institute for Iranian Experiments (IIIS) to initiate and construct rely on with targets.
The phishing tries are also characterized by the use of compromised email accounts belonging to legit contacts and various menace-actor-managed email accounts, the latter of which is named Multi-Persona Impersonation (MPI).
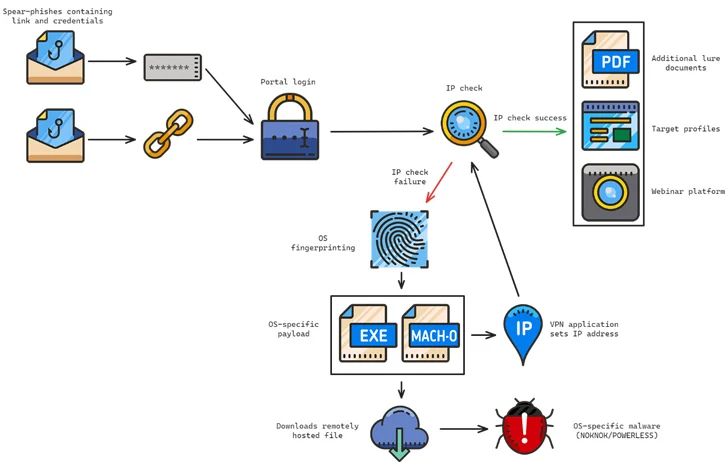
The attack chains commonly hire RAR archives made up of LNK data files as a beginning stage to distribute malware, with the messages urging future targets to join a pretend webinar about topics that are of curiosity to them. A single these kinds of multi-phase an infection sequence has been noticed to deploy BASICSTAR and KORKULOADER, a PowerShell downloader script.
BASICSTAR, a Visual Fundamental Script (VBS) malware, is capable of collecting simple procedure facts, remotely executing commands relayed from a command-and-manage (C2) server, and downloading and exhibiting a decoy PDF file.
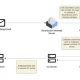
What is actually much more, some of these phishing assaults are engineered to serve distinct backdoors depending on the machine’s operating process. Even though Windows victims are compromised with POWERLESS, Apple macOS victims are focused with an infection chain culminating in NokNok through a practical VPN software that’s laced with malware.
“This danger actor is remarkably fully commited to conducting surveillance on their targets in buy to identify how most effective to manipulate them and deploy malware,” the researchers said. “Also, several other menace actors have regularly churned out as quite a few campaigns as CharmingCypress, dedicating human operators to help their ongoing attempts.”

The disclosure will come as Recorded Potential uncovered IRGC’s concentrating on of Western international locations working with a network of contracting corporations that also specialize in exporting systems for surveillance and offensive uses to nations around the world like Iraq, Syria, and Lebanon.
The romance between intelligence and armed service corporations and Iran-dependent contractors will take the variety of several cyber centers that act as “firewalls” to conceal the sponsoring entity.
They include things like Ayandeh Sazan Sepher Aria (suspected to be affiliated with Emennet Pasargad), DSP Research Institute, Sabrin Kish, Soroush Saman, Mahak Rayan Afraz, and the Parnian Telecommunication and Digital Business.
“Iranian contracting firms are founded and run by a restricted-knit network of personas, who, in some circumstances, stand for the contractors as board associates,” the enterprise claimed. “The folks are carefully associated with the IRGC, and in some conditions, are even representatives of sanctioned entities (this sort of as the IRGC Cooperative Foundation).”
Discovered this report appealing? Stick to us on Twitter and LinkedIn to browse a lot more exclusive content material we publish.
Some parts of this article are sourced from:
thehackernews.com

 FBI’s Most-Wanted Zeus and IcedID Malware Mastermind Pleads Guilty
FBI’s Most-Wanted Zeus and IcedID Malware Mastermind Pleads Guilty