The Android banking trojan recognised as Anatsa has expanded its focus to incorporate Slovakia, Slovenia, and Czechia as portion of a new marketing campaign observed in November 2023.
“Some of the droppers in the campaign productively exploited the accessibility service, regardless of Google Play’s enhanced detection and security mechanisms,” ThreatFabric claimed in a report shared with The Hacker News.
“All droppers in this marketing campaign have shown the capability to bypass the limited configurations for accessibility assistance in Android 13.” The campaign, in full, will involve 5 droppers with more than 100,000 whole installations.
Also known by the identify TeaBot and Toddler, Anatsa is identified to be distributed beneath the guise of seemingly innocuous apps on the Google Enjoy Retailer. These apps, known as droppers, facilitate the set up of the malware by circumventing security measures imposed by Google that look for to grant delicate permissions.
In June 2023, the Dutch cellular security business disclosed an Anatsa marketing campaign that specific banking customers in the U.S., the U.K., Germany, Austria, and Switzerland at minimum due to the fact March 2023 utilizing dropper applications that were being collectively downloaded over 30,000 situations on the Participate in Retail outlet.

Anatsa comes equipped with abilities to acquire total regulate over contaminated products and execute steps on a victim’s behalf. It can also steal credentials to initiate fraudulent transactions.
The most recent iteration observed in November 2023 is no distinctive in that one of the droppers masqueraded as a phone cleaner application named “Phone Cleaner – File Explorer” (bundle identify “com.volabs.androidcleaner”) and leveraged a system called versioning to introduce its malicious behavior.
Whilst the app is no more time obtainable for down load from the official storefront for Android, it can however be downloaded via other sketchy 3rd-social gathering sources.
According to data obtainable on application intelligence system AppBrain, the app is approximated to have been downloaded about 12,000 periods throughout the time it was offered on the Google Engage in Shop between November 13 and November 27, when it was unpublished.
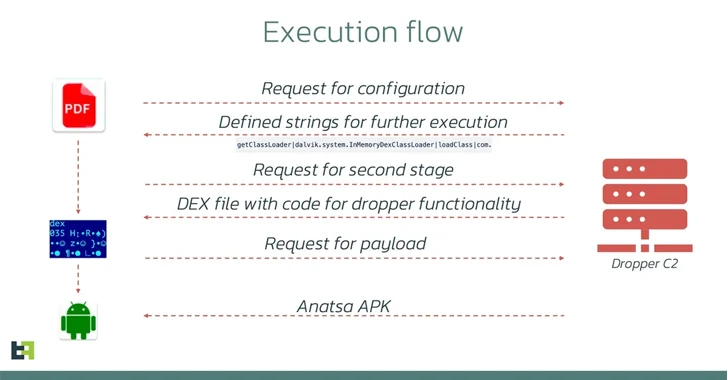
“Initially, the application appeared harmless, with no destructive code and its accessibility assistance not engaging in any harmful activities,” ThreatFabric scientists claimed.
“Nonetheless, a week just after its launch, an update introduced destructive code. This update altered the AccessibilityService operation, enabling it to execute destructive steps these types of as automatically clicking buttons at the time it been given a configuration from the [command-and-control] server.”
What makes the dropper notable is that its abuse of the accessibility services is personalized to Samsung products, suggesting that it was developed to solely target the enterprise-produced handsets at some level, despite the fact that other droppers employed in the campaign have been found to be maker agnostic.
The droppers are also able of circumventing Android 13’s limited options by mimicking the procedure utilized by marketplaces to put in new apps devoid of possessing their obtain to the accessibility services functionalities disabled, as previously observed in the scenario of dropper services like SecuriDropper.

“These actors prefer concentrated assaults on particular regions instead than a world spread, periodically shifting their concentrate,” ThreatFabric said. “This focused tactic enables them to focus on a limited number of money businesses, main to a significant range of fraud conditions in a short time.”
The growth will come as Fortinet FortiGuard Labs detailed one more marketing campaign that distributes the SpyNote remote accessibility trojan by imitating a genuine Singapore-centered cryptocurrency wallet support recognised as imToken to swap desired destination wallet addresses and with actor-managed types and conduct illicit asset transfers.
“Like substantially Android malware today, this malware abuses the accessibility API,” security researcher Axelle Apvrille claimed. “This SpyNote sample utilizes the Accessibility API to goal renowned crypto wallets.”
Identified this short article interesting? Follow us on Twitter and LinkedIn to go through a lot more unique content material we article.
Some parts of this article are sourced from:
thehackernews.com


 Russian-Linked Hackers Breach 80+ Organizations via Roundcube Flaws
Russian-Linked Hackers Breach 80+ Organizations via Roundcube Flaws