Did you know that Network Detection and Reaction (NDR) has turn into the most efficient technology to detect cyber threats? In contrast to SIEM, NDR offers adaptive cybersecurity with lowered bogus alerts and economical danger response.
Are you conscious of Network Detection and Reaction (NDR) and how it truly is turn into the most effective technology to detect cyber threats?
NDR massively upgrades your security through risk-primarily based alerting, prioritizing alerts primarily based on the potential risk to your organization’s units and information. How? Properly, NDR’s serious-time examination, machine mastering, and threat intelligence offer quick detection, lowering alert tiredness and enabling better determination-generating. In contrast to SIEM, NDR gives adaptive cybersecurity with decreased fake positives and effective threat response.
Why Use Risk-Based mostly Alerting?
Risk-based mostly alerting is an solution where security alerts and responses are prioritized dependent on the level of risk they pose to an organization’s devices, information, and all round security posture. This method permits companies to concentrate their methods on addressing the most critical threats 1st.
Positive aspects of risk-based mostly alerting contain successful resource allocation and much more:
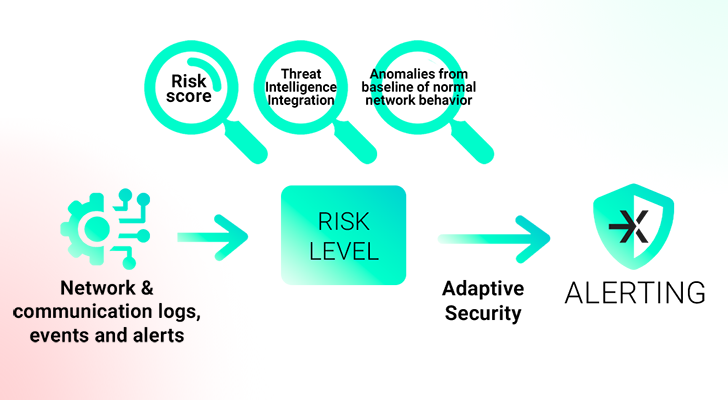
3 Methods to Setting up Your Risk-Centered Cybersecurity Approach
1. The Part of NDR in Risk-Centered Alerts
Network Detection and Reaction (NDR) plays a vital part in facilitating or enabling the implementation of risk-centered alerts in an organization’s cybersecurity approach.
NDR answers are developed to detect and reply to threats on your network and present insights into the potential risks of many actions or incidents: they analyze the designs and conduct of network targeted traffic to detect anomalies that indicate likely security challenges.
With this contextual details about network activity, different weights of analyzers in the network, and an aggregation of many alarms up to the alarm threshold, they can determine distinctive inform stages dependent on the weighting of the evidence. On top of that, certain critical zones can be described in asset administration. This context is important for evaluating the severity and likely effects of security alerts, aligning with the risk-primarily based tactic.
2. Leveraging Threat Intelligence Feeds for Increased Risk Evaluation
Considering the fact that NDR options are built-in with threat intelligence feeds, they enrich the facts employed for the evaluation and categorization of network exercise. Criticality can perhaps be improved by OSINT, Zeek, or MITRE ATT&CK info. This integration boosts the means to evaluate the risk associated with distinct alerts.
Some NDR methods offer automatic reaction capabilities, serving businesses in responding promptly to higher-risk alerts. This aligns with the goal of risk-dependent alerting to deal with critical threats right away:
- A risk rating is assigned to detected occasions or alerts primarily based on several variables, including the severity of the detected exercise, the context in which it transpired, the influenced belongings or methods, and historic data. The purpose is to assess the likely injury or impression of the detected function.
- In the risk booster, different components influencing risk evaluation are weighted in a different way. For example, routines involving critical assets or privileged accounts may perhaps acquire a bigger risk rating. Situations deviating drastically from founded baselines or styles may perhaps also be weighted far more seriously.
- Correlated alerts enjoy a very important function in uncovering concealed attacks in the qualifications of ordinary network functions. Increased correlation of alerts considerably decreases the workload for analysts by minimizing the range of personal alerts they ought to handle.
3. Automating Responses to Superior-Risk Alerts
The strategic use of automation is of utmost relevance in strengthening network defenses versus opportunity assaults, particularly thinking about the sizeable day-to-day conversation volumes inside of networks that attackers could exploit.
Considering that user and entity conduct investigation is currently integrated into the NDR to examine the habits of users and entities (e.g., products) in the network, insider threats, compromised accounts, or suspicious consumer behavior can be detected much more simply and utilised for risk assessment.
For the reason that risk scores are not static but alter in excess of time, they can be altered as new data gets to be accessible or the security landscape evolves. If an at first lower-risk occasion escalates to a larger-risk celebration, the risk score is adjusted accordingly.
Leveraging NDR with Machine Learning For Dynamic Risk Assessment and Increased Cybersecurity
Equipment discovering algorithms can sift as a result of massive volumes of information to build conventional styles or baselines of network actions. These baselines act as a benchmark for identifying deviations that could sign suspicious or malicious activity. The automation enables security teams to concentrate their endeavours on investigating and mitigating high-risk alerts, boosting general efficiency. Equipment mastering algorithms can continuously learn and adapt to new styles and threats, producing the security procedure far more adaptive and able of tackling emerging challenges. The continual finding out is priceless in the swiftly evolving landscape of cybersecurity.
By integrating NDR abilities with equipment understanding, companies can dynamically assess the risk affiliated with many actions on the network. Device discovering algorithms can adapt to evolving threats and adjustments in network habits, contributing to a a lot more precise and responsive risk assessment.

Illustrations & Use Situations: More Detection, Less False Alerts
Supplied an organization makes use of a Network Detection and Response (NDR) alternative to monitor its network targeted traffic, the business assesses risk scores for detected events based on their opportunity effect and contextual info.
1. Unauthorized Access Endeavor:
An external IP address attempts to get unauthorized accessibility to a critical server. The risk variables are the influenced asset: a critical server made up of delicate consumer data.
Anomalous behavior: The IP deal with has no prior record of accessing this server. The risk score is significant. The NDR procedure assigns a large-risk score to the inform thanks to the involvement of a critical asset and the detection of anomalous conduct, suggesting a likely security breach. The high-risk alert is immediately escalated for investigation and reaction.
2. Software Update:
In this inform, a schedule application update occasion is explained, where by an inside gadget initiates an update from a trustworthy supply. The risk factors include the affected asset (a non-critical consumer workstation) and the schedule conduct of the update from a trustworthy resource, ensuing in a low-risk rating.
The NDR system assigns a small-risk score to this alert, indicating that it includes a non-critical asset, and the actions is program and expected. As a consequence, this very low-risk warn could be logged and monitored but does not require fast focus.
Summary: That is Why It can be Top-quality to SIEM
NDR is regarded as remarkable to Security Info and Occasion Administration (SIEM) for risk-dependent alerting mainly because NDR focuses on real-time examination of network targeted traffic designs and behaviors, offering rapid detection of anomalies and probable threats, while SIEM relies on log assessment only, which might have delays and could miss subtle, network-centric threats as nicely as developing multitudes of alerts (false kinds also).
Last but not the very least, NDR incorporates device understanding and menace intelligence, improving its capacity to adapt to evolving challenges and minimizing wrong positives, leading to additional exact and well timed risk assessments compared to traditional SIEM approaches.
So, prepared to improve and enhance your detection abilities? If you’re even now contemplating, obtain our new Security Detection whitepaper for a deep dive into how risk-primarily based alerting can help you save you expenditures and time and significantly minimize your false alerts.

Identified this report interesting? This write-up is a contributed piece from just one of our valued associates. Comply with us on Twitter and LinkedIn to browse much more exceptional content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Anatsa Android Trojan Bypasses Google Play Security, Expands Reach to New Countries
Anatsa Android Trojan Bypasses Google Play Security, Expands Reach to New Countries