Men and women in the Pakistan location have been targeted employing two rogue Android applications accessible on the Google Participate in Store as aspect of a new specific marketing campaign.
Cybersecurity company Cyfirma attributed the campaign with average self confidence to a menace actor acknowledged as DoNot Crew, which is also tracked as APT-C-35 and Viceroy Tiger.
The espionage exercise requires duping Android smartphone homeowners into downloading a method which is utilised to extract get in touch with and spot information from unwitting victims.
“The motive behind the attack is to get information and facts through the stager payload and use the gathered information and facts for the next-stage attack, utilizing malware with a lot more damaging options,” the corporation said.
DoNot Staff is a suspected India-nexus menace actor that has a standing for carrying out assaults from various countries in South Asia. It has been energetic given that at minimum 2016.
Even though an October 2021 report from Amnesty Worldwide joined the group’s attack infrastructure to an Indian cybersecurity company referred to as Innefu Labs, Team-IB, in February 2023, mentioned it identified overlaps between DoNot Staff and SideWinder, one more suspected Indian hacking crew.

Attack chains mounted by the group leverage spear-phishing e-mail containing decoy files and information as lures to spread malware. In addition, the menace actor is acknowledged to use destructive Android applications that masquerade as authentic utilities in their concentrate on assaults.
These applications, as soon as put in, activate trojan behavior in the background and can remotely handle the victim’s procedure, apart from pilfering confidential info from the infected equipment.

The newest set of purposes learned by Cyfirma originate from a developer named “SecurITY Market” and move off as VPN and chat apps, with the latter continue to out there for obtain from the Participate in Retail store –
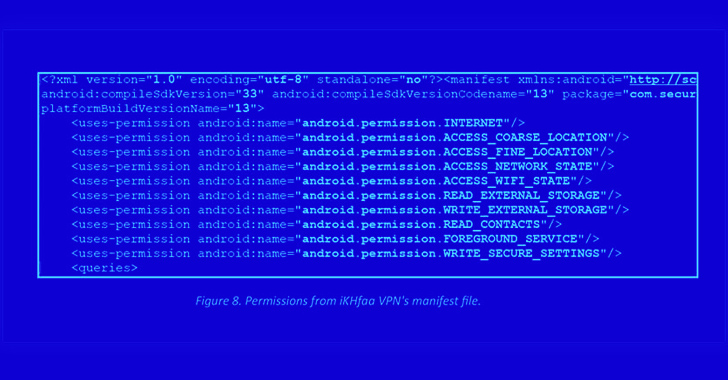
- iKHfaa VPN (com.securityapps.ikhfaavpn) – 10+ downloads
- nSure Chat (com.nSureChat.software) – 100+ downloads
The VPN application, which reuses supply code taken from the real Liberty VPN item, is no lengthier hosted on the official application storefront, even though evidence shows that it was offered as recently as June 12, 2023.
The very low down load counts is an sign that the applications are becoming employed as section of a highly focused procedure, a hallmark of nation-state actors. Both apps are configured to trick the victims into granting them invasive permissions to access their make contact with lists and exact destinations.
Little is recognized about the victims specific employing the rogue apps barring the actuality that they are dependent in Pakistan. It really is believed that users might have been approached by means of messages on Telegram and WhatsApp to lure them into installing the applications.
By utilizing the Google Engage in Keep as a malware distribution vector, the solution abuses the implicit believe in placed by customers on the on the net application market and lends it an air of legitimacy. It can be, therefore, critical that applications are very carefully scrutinized prior to downloading them.
“It seems that this Android malware was specially developed for facts collecting,” Cyfirma said. “By gaining entry to victims’ get hold of lists and places, the risk actor can strategize long term attacks and use Android malware with sophisticated characteristics to target and exploit the victims.”
Uncovered this posting interesting? Observe us on Twitter and LinkedIn to study a lot more unique written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 New Mystic Stealer Malware Targets 40 Web Browsers and 70 Browser Extensions
New Mystic Stealer Malware Targets 40 Web Browsers and 70 Browser Extensions