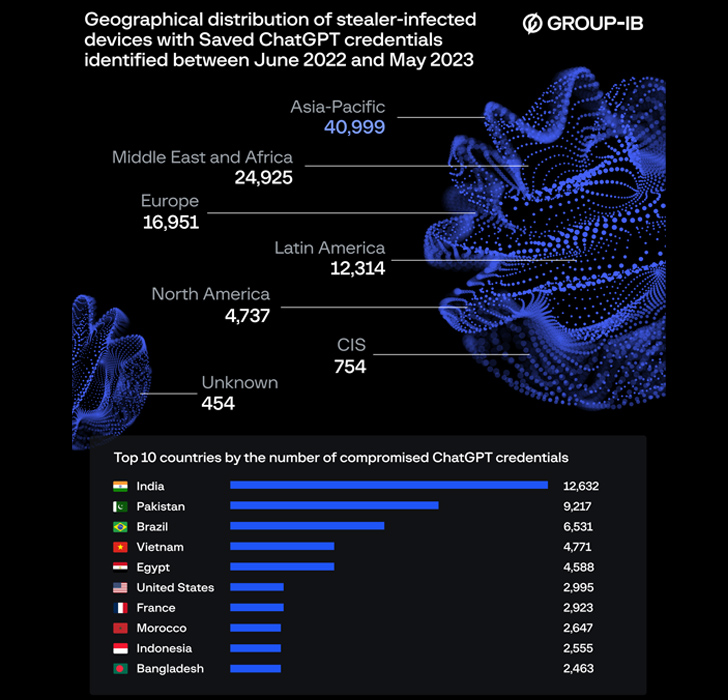
About 100,000 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces in between June 2022 and May perhaps 2023, with India by yourself accounting for 12,632 stolen credentials.
The credentials were being uncovered inside details stealer logs made readily available for sale on the cybercrime underground, Group-IB reported in a report shared with The Hacker Information.
“The number of out there logs containing compromised ChatGPT accounts reached a peak of 26,802 in May well 2023,” the Singapore-headquartered corporation reported. “The Asia-Pacific region has experienced the best focus of ChatGPT qualifications getting presented for sale in excess of the earlier 12 months.”
Other international locations with the most number of compromised ChatGPT qualifications consist of Pakistan, Brazil, Vietnam, Egypt, the U.S., France, Morocco, Indonesia, and Bangladesh.
A even further evaluation has revealed that the the greater part of logs made up of ChatGPT accounts have been breached by the infamous Raccoon facts stealer, adopted by Vidar and RedLine.

Information and facts stealers have grow to be preferred amongst cybercriminals for their capacity to hijack passwords, cookies, credit history playing cards, and other information and facts from browsers, and cryptocurrency wallet extensions.
“Logs that contains compromised facts harvested by information stealers are actively traded on dark web marketplaces,” Team-IB stated.
“Supplemental data about logs accessible on this sort of marketplaces includes the lists of domains found in the log as nicely as the information about the IP tackle of the compromised host.”
Usually available centered on a subscription-centered pricing design, they have not only decreased the bar for cybercrime, but also provide as a conduit for launching observe-on attacks employing the siphoned credentials.
“Quite a few enterprises are integrating ChatGPT into their operational move,” Dmitry Shestakov, head of threat intelligence at Group-IB, reported.
“Personnel enter labeled correspondences or use the bot to improve proprietary code. Given that ChatGPT’s conventional configuration retains all discussions, this could inadvertently present a trove of sensitive intelligence to risk actors if they get hold of account credentials.”
To mitigate these kinds of pitfalls, it truly is proposed that end users adhere to acceptable password cleanliness methods and safe their accounts with two-factor authentication (2FA) to avoid account takeover assaults.
The growth arrives amid an ongoing malware marketing campaign that is leveraging fake OnlyFans webpages and grownup content lures to supply a distant entry trojan and an details stealer named DCRat (or DarkCrystal RAT), a modified edition of AsyncRAT.
Upcoming WEBINAR🔐 Mastering API Security: Comprehending Your Legitimate Attack Surface
Explore the untapped vulnerabilities in your API ecosystem and take proactive steps in the direction of ironclad security. Sign up for our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:soon afterdisplay:inline-block.examine_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-right-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimension:13pxmargin:20px 0font-weight:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-prime:2px stable #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-weight:900text-align:leftline-height:33px.wn-descriptiontext-align:leftfont-size:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
“In noticed instances, victims ended up lured into downloading ZIP files that contains a VBScript loader which is executed manually,” eSentire researchers mentioned, noting the activity has been underway since January 2023.
“File naming conference indicates the victims were lured employing express pics or OnlyFans content for various adult movie actresses.”
It also follows the discovery of a new VBScript variant of a malware known as GuLoader (aka CloudEyE) that employs tax-themed decoys to start PowerShell scripts capable of retrieving and injecting Remcos RAT into a authentic Windows process.
“GuLoader is a hugely evasive malware loader frequently utilised to supply information-stealers and Remote Administration Instruments (RATs),” the Canadian cybersecurity corporation mentioned in a report released previously this thirty day period.
“GuLoader leverages person-initiated scripts or shortcut data files to execute various rounds of hugely obfuscated instructions and encrypted shellcode. The final result is a memory-resident malware payload running within a legitimate Windows process.”
Uncovered this post intriguing? Follow us on Twitter and LinkedIn to read through extra exceptional articles we post.
Some parts of this article are sourced from:
thehackernews.com


 Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign
Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign