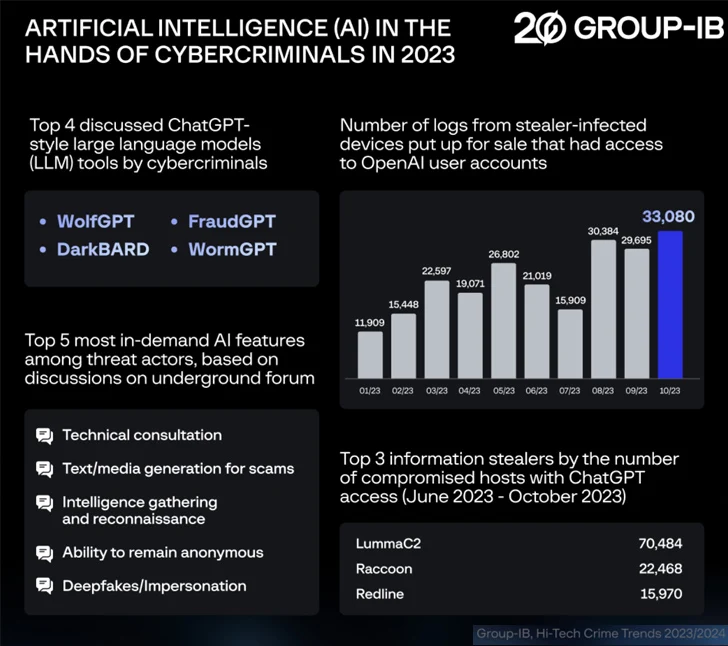
Much more than 225,000 logs containing compromised OpenAI ChatGPT qualifications ended up made out there for sale on underground marketplaces amongst January and Oct 2023, new findings from Team-IB display.
These qualifications have been discovered within just details stealer logs related with LummaC2, Raccoon, and RedLine stealer malware.
“The quantity of contaminated products diminished a little bit in mid- and late summer time but grew considerably between August and September,” the Singapore-headquartered cybersecurity firm stated in its Hi-Tech Criminal offense Traits 2023/2024 report printed past 7 days.

Involving June and Oct 2023, far more than 130,000 one of a kind hosts with accessibility to OpenAI ChatGPT were infiltrated, a 36% enhance more than what was observed for the duration of the first 5 months of 2023. The breakdown by the major 3 stealer family members is below –
- LummaC2 – 70,484 hosts
- Raccoon – 22,468 hosts
- RedLine – 15,970 hosts
“The sharp boost in the number of ChatGPT credentials for sale is because of to the all round increase in the selection of hosts infected with facts stealers, data from which is then put up for sale on markets or in UCLs,” Team-IB claimed.
The development comes as Microsoft and OpenAI discovered that nation-point out actors from Russia, North Korea, Iran, and China are experimenting with artificial intelligence (AI) and massive language designs (LLMs) to complement their ongoing cyber attack operations.
Stating that LLMs can be utilised by adversaries to brainstorm new tradecraft, craft convincing scam and phishing assaults, and increase operational productiveness, Team-IB mentioned the technology could also velocity up reconnaissance, execute hacking toolkits, and make scammer robocalls.
“In the previous, [threat actors] had been mostly intrigued in company desktops and in systems with entry that enabled motion throughout the network,” it mentioned. “Now, they also aim on devices with entry to general public AI techniques.

“This offers them entry to logs with the interaction record involving workers and methods, which they can use to lookup for confidential info (for espionage purposes), specifics about inside infrastructure, authentication facts (for conducting even extra harmful assaults), and information and facts about application supply code.”
Abuse of valid account credentials by risk actors has emerged as a top rated access approach, largely fueled by the easy availability of this kind of information and facts via stealer malware.
“The blend of a rise in infostealers and the abuse of valid account credentials to attain original entry has exacerbated defenders’ identity and entry administration challenges,” IBM X-Power mentioned.
“Business credential info can be stolen from compromised gadgets by credential reuse, browser credential retailers or accessing company accounts straight from own gadgets.”
Uncovered this posting attention-grabbing? Abide by us on Twitter and LinkedIn to read far more exclusive information we article.
Some parts of this article are sourced from:
thehackernews.com


 Warning: Thread Hijacking Attack Targets IT Networks, Stealing NTLM Hashes
Warning: Thread Hijacking Attack Targets IT Networks, Stealing NTLM Hashes