The threat actor recognised as TA577 has been noticed working with ZIP archive attachments in phishing e-mails with an intention to steal NT LAN Supervisor (NTLM) hashes.
The new attack chain “can be utilised for delicate details gathering purposes and to permit adhere to-on action,” company security company Proofpoint explained in a Monday report.
At the very least two strategies using gain of this tactic were observed on February 26 and 27, 2024, the business added. The phishing waves disseminated hundreds of messages and focused hundreds of corporations throughout the planet.

The messages by themselves appeared as responses to former e-mails, a recognized approach called thread hijacking, in a bid to boost the chance of the attacks’ good results.
The ZIP attachments come with an HTML file that is designed to speak to an actor-controlled Server Information Block (SMB) server.
“TA577’s aim is to seize NTLMv2 Problem/Response pairs from the SMB server to steal NTLM hashes dependent on features of the attack chain and applications utilised,” the enterprise said, which could then be employed for go-the-hash (PtH) type assaults.
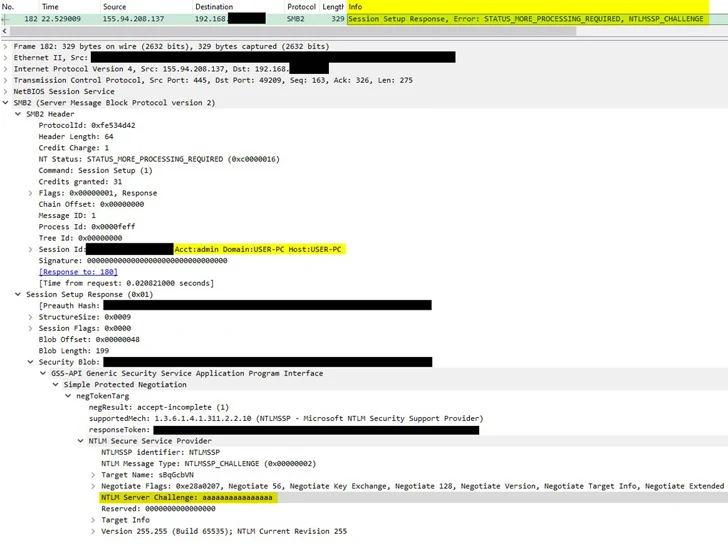
This suggests that adversaries who are in possession of a password hash do not will need the fundamental password to authenticate a session, in the end enabling them to go via a network and get unauthorized accessibility to precious data.
TA577, which overlaps with an action cluster tracked by Development Micro as Drinking water Curupira, is just one of the most sophisticated cybercrime teams. It has been connected to the distribution of malware families like QakBot and PikaBot in the earlier.

“The rate at which TA577 adopts and distributes new tactics, tactics, and procedures (TTPs) suggests the risk actor most likely has the time, assets, and practical experience to speedily iterate and test new supply procedures,” Proofpoint explained.
It also described the danger actor as acutely aware of the shifts in the cyber menace landscape, promptly adapting and refining its tradecraft and supply procedures to bypass detection and fall a wide variety of payloads. Corporations are hugely suggested to block outbound SMB to prevent exploitation.
Identified this report appealing? Follow us on Twitter and LinkedIn to study a lot more unique articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Critical JetBrains TeamCity On-Premises Flaws Could Lead to Server Takeovers
Critical JetBrains TeamCity On-Premises Flaws Could Lead to Server Takeovers